Welcome Everybody! The magnificent Hacktober went and I hope this sweet November is going extremely well. I believe past September and this Hacktober is a champion among different months in my ethical hacking profession. No, I normally don't put stock in the Horoscopes.
What number of you play or ever played PlayStation?
PlayStation is a gaming brand that consists of four home video game consoles, as well as a media center owned by **Sony. **Wondering why it's identified with this work? I was able to take over the accounts of all PlayStation users and employees and can release sensitive information and data.
I always desired to be featured in Sony's security researcher's Hall of Thanks and wanted to wear Secure @ Sony T-Shirt. I still remember when I made strides in Web Application Penetration testing, Sony.com was my first target and subsequent to spending an entire day on it. I wind up with reporting only a missing X-Frame Option on Sony which was not really a security frail. In any case, this time I got a few aptitudes with good fortunes. Let's get started :D
A few months back one of my friends posted a photo of himself wearing a cool T-Shirt of Secure @ Sony. Subsequent to asking him he revealed the secret to me that he reported Cross-Site Request Forgery in one of PlayStation's site that is PlayStation Jobs. Likewise, I noted down the target and planned to do a security test on a particular date.
A few days back, I tested PlayStation Jobs and established two security vulnerabilities that influenced the structure and the attacker was able to take over all the accounts of the website playstationjobs.co.uk.
- Cross-Site Request Forgery in Adding or Removing Job from Job Basket.
- Privilege Escalation leads to all users Account Takeover.
Cross-Site Request Forgery in Adding or Removing Job from Job Basket
The vast majority of you wonderful people from a security background knew about Cross-Site Request Forgery but in case you don't. Give me a chance to entirety up in some great words. Cross-site Request Forgery (CSRF), XSRF, or Sea surf refers to an attack against authenticated web applications using Cookies wherein an attacker is able to trick a victim into making a request the victim did not intend to make. Therefore, with CSRF an attacker abuses the trust a web application has with a victim’s browser.
In the crave of playing with some functionality of the site. I saw that the site was allowing users to add or remove Jobs in the Job basket like we used to do in Adding things in the shopping basket. I took a gander at this functionality HTTP Response and saw that the GET method is utilizing when adding or removing Job from Job basket with no authenticity or CSRF token or any further check is applied.
So it's reasonable for me that I was able to add or remove Job from any user Job basket without making him aware of the act. I made an HTML form to check whether it works or not and subsequent to testing it worked accurately and it's sufficient to abuse users and site behaviour. If it's not too much trouble investigate video proof of concept for better understanding of vulnerability.
Privilege Escalation leads to all users Account Takeover
This is outstanding amongst other security issues. I've established myself and I truly learnt a ton and trust me it's much more simple than your expectations. Privilege Escalation itself not considered as a security flaw. It's the act of exploiting a bug, design n oversight in an operating system or software application to gain elevated access to resources that are normally protected from an application or user.
Confronted a situation were registering an account from the same email leading to account users account takeover. Why not divide this additionally? In case you're a developer and you're perusing this Hi-Five you're really a great place. In short, no validation on the form field allows me to take over the account of all the users and actually these users are the employees of PlayStation. This type of vulnerability is also considered a logical security vulnerability. But how is it exploitable? The site allows different users to make accounts and apply for specific Jobs. After applying, the website asks you to enter your Name and Email and the site diverts you to another page where you need to upload our CV and include different subtle elements for applying for Jobs. Suppose we have made an account and uploaded our CV and updated different details also and now we logged out from our account.
Presently as other users apply for Job or want to register on PlayStation Jobs and in case he applied for that Job from my Email. The site functionality didn't ask for the current password which is also considered as Insecure Password Mechanism. Also, it doesn't check if the Email is already registered in the Database or not. The attacker was then easily able to sign in into my account without entering the password and if somehow attacker gets my Email he can possibly takeover my whole account and see the intensely sensitive data which includes:
Download or modify CVs.
Change Email Address.
Password Change.
View Job Applications.
Referral Invite.
Approved Jobs.
Declined Jobs.
Contact Numbers.
Address Details.
Delete Account and attacker can do every possible revelation.
If it's not too much trouble, take a look at video demonstration for better understanding of vulnerability.
I hope you comprehended the broken feature of the application that enables an attacker to totally take over the account of all the employees just by knowing the Email of the victim which is an Employee of PlayStation in this situation.
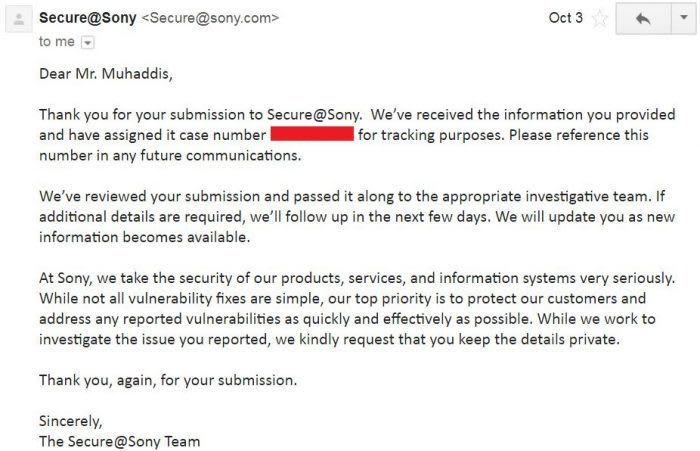
Without squandering my chance this time, I composed a detailed report regarding both of the issues and forward it to the Sony Security team. The next day I got a reply from their security team.
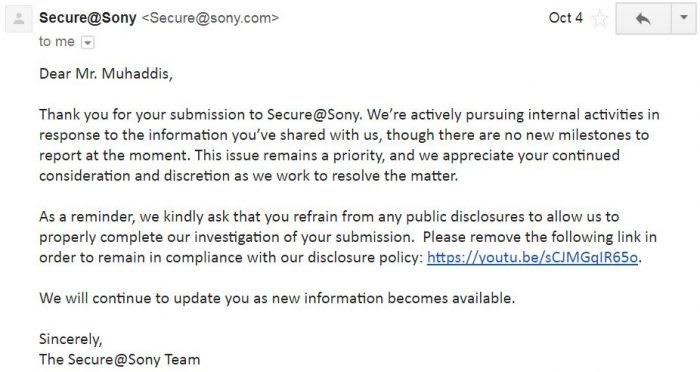
Next day on October fourth I got an Email from Sony Security. As it was a Critical security flaw, their security asked me to bring down the video from YouTube in case it goes in the hands of an attacker.
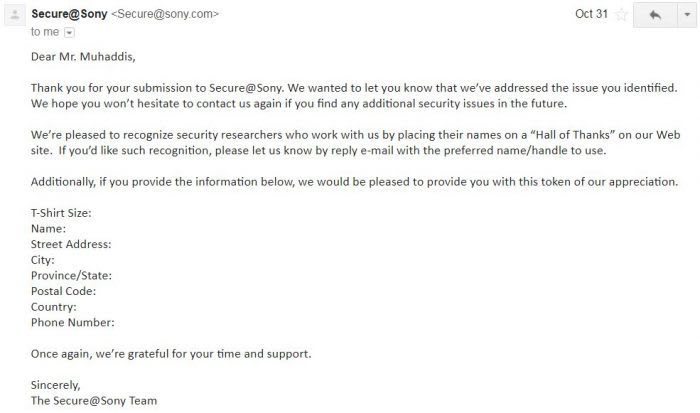
For the time, I take down videos from YouTube. Following a couple of days, they released a patch and fixed a security flaw and approached me for Swag as a reward and offered me a mention on Sony's hall of thanks page.
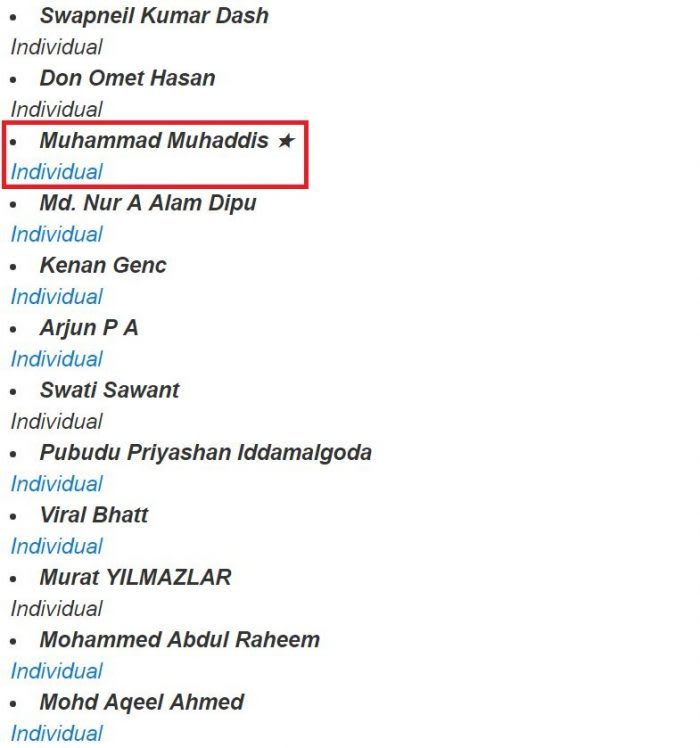
I provided them with my details and the next day they recognized me by adding my name in their security researchers hall of thanks.
You might be wondering that Star in front of my name. According to Sony security policy, “★ Researcher who denotes multiple submissions in one year”.
A few days ago I received two cool T-Shirt swags from Sony saying Secure @ Sony Finder || 2017. I'll feel so proud of wearing this.
Thanks for taking the time, I hope you learned something. I truly value that. I look forward to seeing you there again soon enough. I require recommendations from wonderful people. Don’t hesitate to subscribe to my NewsLetter. Feel free to comment and let me know what your thoughts are.




Top comments (0)