Welcome here, Hunting before the examination is very fun when contrasted with typical days. Well, I was not in an inclination of bug chasing with full fixation yet all that happened surprisingly, Sound funny? I'm not joking. Each analyst has a fantasy to test security platforms like HackerOne or BugCrowd and so forth. These stages are effectively tried by many top security researchers so I don't think whether my security discoveries will be acknowledged or not. In support of a renowned axiom, hope is the key to success, I began testing one of the subdomains of a BugCrowd. Recently one of my companions discovered Cross-Site Scripting (XSS) vulnerability in the same area and he has been compensated with an extraordinary measure of Bug Bounty. My fortunes worked this time, so let's go how it starts.
Bugcrowd is a vulnerability disclosure platform. It provides Bugcrowd Security Researchers with a secure platform to submit vulnerabilities to your team and allows you the ability to incentivize our researchers through. Bugcrowd points or monetary rewards
On 2nd February 2017, I wished to make a Security group account on CrowdControl to permit pen-testers to security test into my site directly in the wake of watching Cross-Site Scripting (XSS) video proof of concept on CrowdControl. I did it all and as I swung to Logout but I wouldn't permit me to logout without testing that web as well.
I configured my Burp-Suite and began testing, and in under five minutes I've established medium vulnerability, you can think of it as an Authentication issue, no it was not a session management flaw. At first, I thought to report it but it would be cooler if I tested the entire space. I wrote down the steps of replication and began chasing once more, and around five minutes I discovered the Information Disclosure issue, does it sound familiar? No, it was not a User/Email list through Signup.
Indeed, with the these both Vulnerability combination, I'm now able to disclose sensitive data and information which including:
I can read or reply reports
I can read or reply reports
Export all reports
User / Email Enumeration
User APIs (If activated)
I can invite any member to join the team (Just in case if the owner is a victim)
Much more sensitive data related to CrowdControl
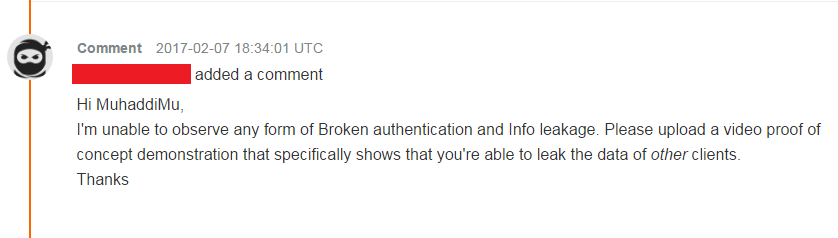
By chaining both vulnerabilities and reporting that Vulnerability chain which leads to sensitive information disclosure and in the next five days they answered that they require some more information identified with that defect and it will be great if I give them a video demonstration of vulnerability.
I gave them video evidence of the idea and in the next fifteen days, they changed the report status to triaged and stamp it as P3 (third level need scope).
In the next twelve days, the report status changed to resolved from triage and they acknowledged me by issuing my name in their Hall of fame. Furthermore, the issue is not reproducible any longer from my side.
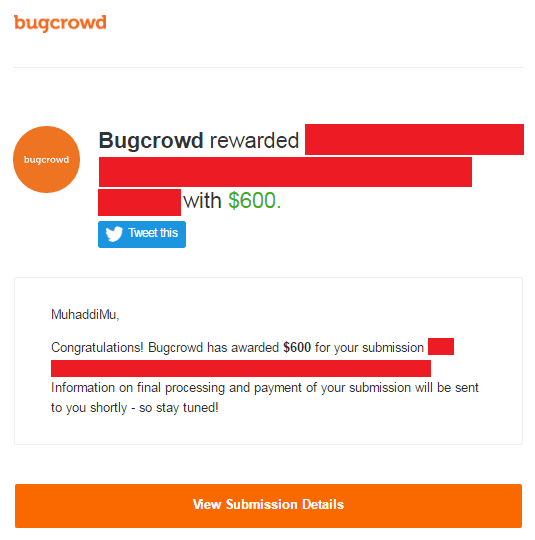
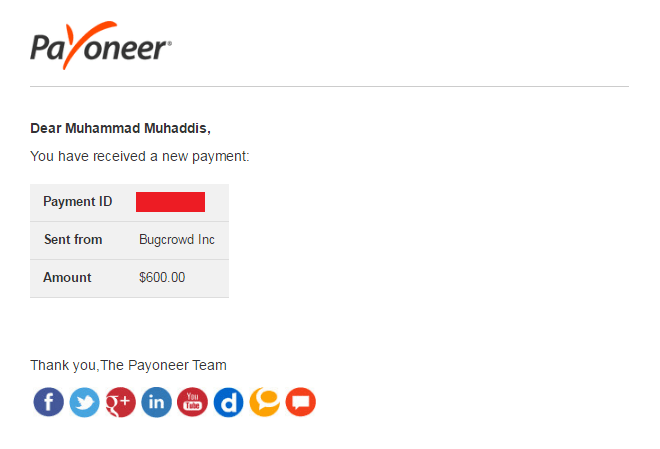
Furthermore, they remunerated me with a reward measure of 600$ abundance and that was my incredible accomplishment.
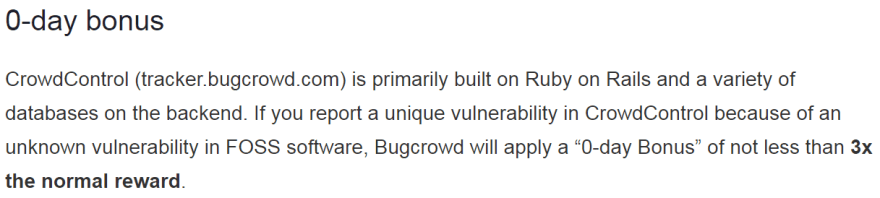
Why Bonus Bounty? According to the BugCrowd security policy CrowdControl is built on Ruby on Rails and they compensate a researcher 3X then their ordinary reward, and their beginning price is 200$.
Timeline
Report Submitted on 2nd February 2017 \
They asked for a video demonstration on 7th February 2017 \
Provided proof of Concept on 10th February 2017 \
I recall them about the report on 24th February 2017 \
They changed state to triaged and P3 on 24th February 2017 \
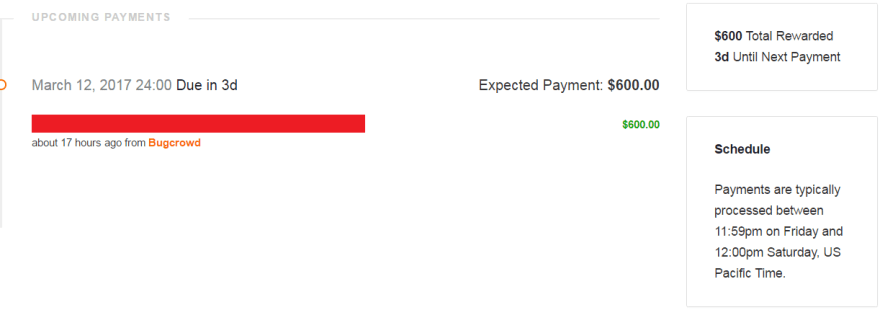
They resolved the report and added a 600$ reward on 8th March 2017 \
I received bug bounty on 12th March 2017 \
They sent me that bug bounty to my Payoneer’s account.
As indicated by the disclosure policy of BugCrowd I can't uncover that bug with complete proof of, yet I trust you comprehend the outline of that Vulnerability.
I am appreciative to BugCrowd for reward and acknowledged my endeavours and time. I am likewise appreciative to you for your profitable time. If you have any proposals or any perplexities identified with this article don't hesitate to remark down. Stay tuned, keep smiling :-)



Top comments (0)