This weekend I took a dive into 0x00Sec's new bi-monthly CTF.
Note::: NO, I won't be posting the found flag{}, but I will be posting the methods I used.
- CTF Name: Exercise #6
- Resource: 0x00SEC
- Difficulty: Easyish
- Number of Flags: 1
Flag1
- Hint:
- Note in the Source Code of
<!-- TODO: -->
<!-- * Test IP whitelisting security -->
- Acquired By:
- Step 1: Is to see the hint in the code and look at the site. There really isn't much to this site.

- Step 2: So I need to figure out how to get on their whitelist. "IP whitelisting is a security feature often used for limiting and controlling access only to trusted users." (2) So, if we look at the response we can see that it is a "Server: nginx/1.17.5" and "X-Powered-By: PHP/7.3.14" in the header. php 7.3.14 has a whitelist but as I was looking at this and trying different URL parameters I found information about the X-Forwarded-For header and how it "is a de-facto standard header for identifying the originating IP address of a client connecting to a web server" (3) and if I make a request with this in the header then I can change the IP address that is displayed at the rejected one. How to exploit this though?
- Step 3: I started sending different requests in the X-Forwarded-For header and a lot of the simple things like quotes and slashes did nothing. I did find that a payload of
X-Forwarded-For: "XOR(if(now()=sysdate(),sleep(6),0))OR”produced an interesting output that was missing information.
- Step 4: Now that I have a point of change I can see what else I can do. I did notice that there was no sleeping so this isn't going to work, but what will happen if I change this to something else? It seems like maybe it wants a few inputs that maybe I can leverage. To do this I take a while and over think it.
- Step 1: Is to see the hint in the code and look at the site. There really isn't much to this site.
Originally, I was assuming that this was something more complicated as I was not getting anything back. I thought that I was working with some blind injection but after 2 hours I realized I just needed to try a few local IP addresses. I did Fuzz a few of the local 192.x.x.x ip range but forgot about the 127.x.x.x range. Eh. Once I tried a "127.0.0.1" I got access to the flag. 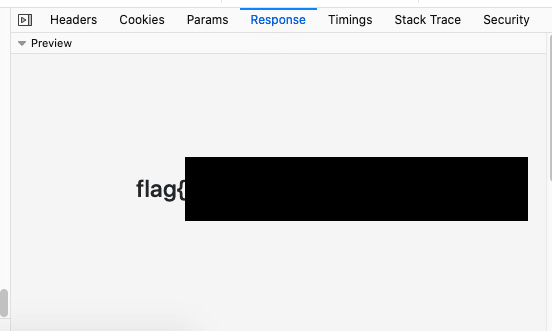
Learned
This CTF taught me about a common security misconfiguration, header spoofing, and that there are a lot of other ways that this header misconfiguration can be used to exploit a system.
I find it interesting that this header could be used to exploit a database if the database is logging it. I did not find out if it can be used if the host is not doing anything with it but that will be an interesting new research point for me.
Resources
- https://ctf.0x00sec.org/
- https://help.gooddata.com/doc/en/building-on-gooddata-platform/gooddata-architecture/ip-whitelisting
- https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Forwarded-For



Top comments (0)