This weekend I took a dive into 0x00Sec's new bi-monthly CTF.
Note::: NO, I won't be posting the found flag{}, but I will be posting the methods I used.
- CTF Name: Exercise #3
- Resource: 0x00SEC
- Difficulty: Easy
- Number of Flags: 1
Flag0
Hint: Note in the Source Code of
<!-- TODO: -->
<!-- * Implement secure object references -->-
Acquired By:
- First thing to do is to just to look at the source code. This shows nothing specific except the hint. All scripts are bootstrap that are being used and nothing looks custom.

- Second thing is to see what it happening when a login is attempted with a "test:test" username:password combo. This showed that there was a "Cookie: PHPSESSID" that was being passed to the application but unlike the previous exercise, this appeared to be a random number and not holding any user information like "admin" or "login=true".
- Third: I actually played around a bit with looking up information on "Information disclosure" as there didn't seem to be any way to register or login without knowing the log in and I didn't want to just keep trying random things. Sadly this didn't really give me any hints so I consulted my bf.
- After talking to my bf I stumbled on trying the "admin:admin" for the "username: password" and that logged me right in...

- So after that I was able to see the "admin" was actually user_id=5.
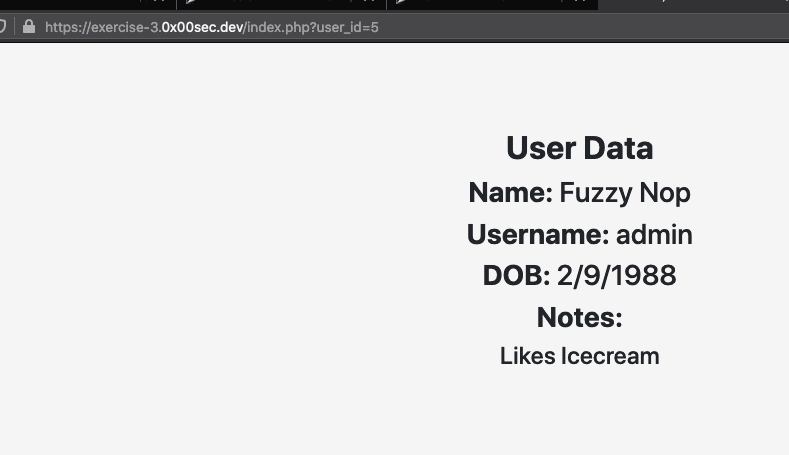
- Now that I tested out different user_id numbers to see if one of them had the flag and after a few different id numbers there it was.

- First thing to do is to just to look at the source code. This shows nothing specific except the hint. All scripts are bootstrap that are being used and nothing looks custom.
Thoughts
This was easy once I got the admin:admin login. I'm a bit irritated that I didn't think of trying that combo as I had been trying admin username with other passwords, but I did get it.
Once logged in this allowed me to find the insecure object references of the user_ids and find the code.
Learned
This CTF taught me a tad about secure object references but more so about trying admin:admin for the username and password on these CTFs...
¯_(ツ)_/¯



Top comments (0)