Some AWS services require access across services because they need to perform an action on that service. Whenever that happen our AWS web services are treated like a user and need to given permission to other services. Roles provide you this functionality and allow users of other accounts to use our services.
The most common use of this is to provide the EC2 service access to other services. We will learn more about EC2 service later on. Let's start
Go to AWS IAM console same as in the user creation article
-
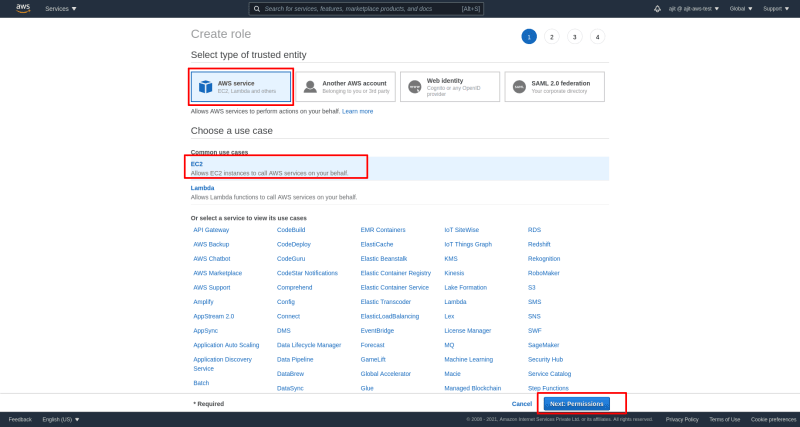
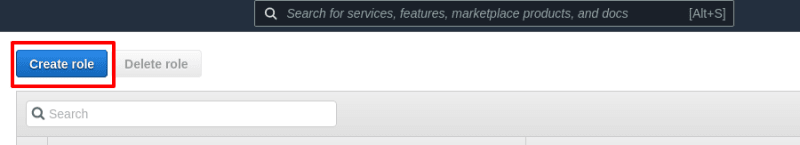
Once you click on create role there will be four options available
- AWS Service
- Another AWS Account
- Web Identity
- SAML 2.0 federation
for a basic understanding of the service let us ignore the last three for now and focus on the first one. Once you select the first one you will see a list of services that can be provided access. Let us select EC2 it is most common use case for creating roles. Click on next:permissions.
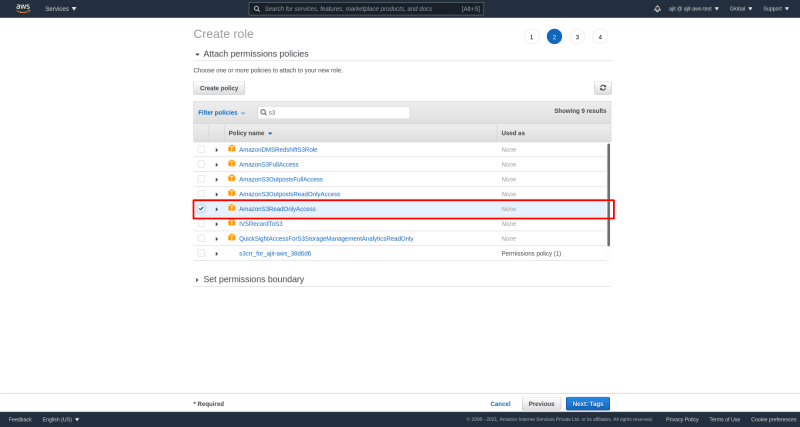
Now we select policies(permission) as we selected while creating user. For this tutorial let's give S3 readonly access to our EC2 service. With the policy AmazonS3ReadOnlyAccess(We will study more about the S3 service later on) and click on Next:Tags.
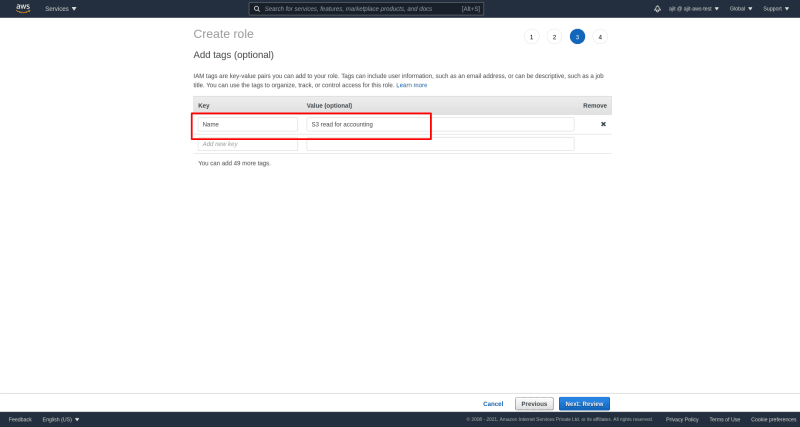
Now we can add tags to our role to better identify roles via these tags
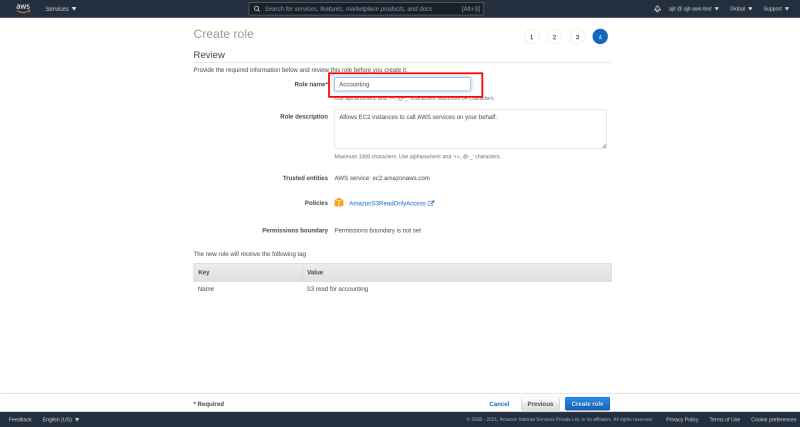
Finally in review screen we can review everything and add a role name. Click on create role after reviewing everything. A role is created now for our EC2 instance has S3 read access.






Top comments (2)
Good explanatory article.
Thanks