My nickname in the networks is Coding Bugs, and I have been working as a software developer and architect for more than 15 years. In my dashboard, you will find articles about programming languages, programming techniques, and other concepts that will help you improve.
Collaboration models allow people to perform different tasks to achieve a common goal. In the case of the tools available in Office 365, digital collaboration models establish how employees and workers should perform their tasks to achieve a certain business goal: selling a certain number of units of a product, training a specific department in the use of a tool, executing the presentation of the company's results, etc.
In this article I show a collaboration model based on the privacy of the content being worked on. From a private point of view, where a small and specific set of employees work together and the contents are not visible to the rest of the colleagues, to a way in which all workers can consume any kind of information and enrich it with more contents.
The sense of privacy is established on the basis of who can access information and documents and who cannot. For example, a company's financial results are worked on privately within the scope of, possibly, the finance department. The employees of this department are the only ones who can access the document and make changes. However, as soon as the head of the department determines that the document has been finalized, it is published to the company's employees. The privacy of the document has changed and its consumption is no longer as restrictive as it was previously. In the event that the document is exposed so that anyone can consult it, the privacy changes again and it has no privacy at all.
With this definition of privacy we determine 4 areas of privacy in the world of work:
- Personal: the information to be managed belongs exclusively to the employee,
- Team: the information to be managed belongs to the team members. Its consumption can only be done by the team members as well as the generation of new information or documentation. The rest of the company's employees will have no knowledge of the existence of the team or the information it handles,
- Portal: the information to be handled belongs exclusively to the portal members. The consumption of the information is done by any employee of the company. However, the generation of new information is the responsibility of the portal members. Company employees will be able to search and consume existing information in any portal,
- Company: the information to be managed belongs to all employees. The consumption of information and the generation of new information can be done by any employee.
Office 365 is the set of tools and cloud services that Microsoft makes available to companies to manage company tasks. Specifically, for document management and collaboration between employees we have Microsoft Teams, SharePoint Online, Yammer, and OneDrive for Business. The features of each of these tools make them ideal for covering the above privacy areas.
Personal security area
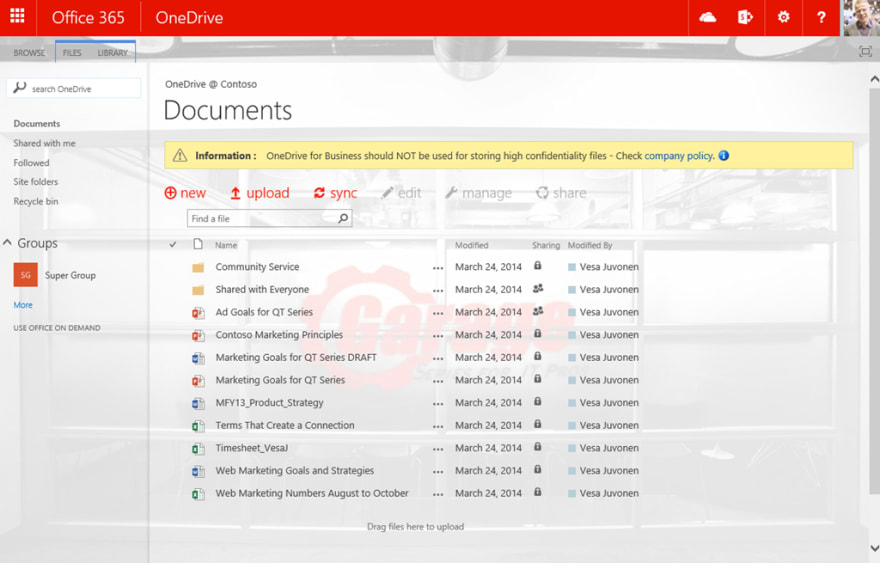
As mentioned above, this area of security is the most restrictive of all. Following its definition, we must provide each employee with a secure space in which they can manage the documents they work on and to which only they have access.
The most suitable tool is OneDrive for Business. Thanks to this, each employee has a private space in the cloud where to store and work with their own documentation. It can be considered as a local folder but with many more features to be discussed in another article.
Team security area
This area would be the next one with a lower restriction than the previous one. In terms of its definition, we can consider it an extension of Personal security area but for several employees, that is, to provide a secure space for a group of employees in which they can manage the documents they work on.
The most suitable tool is Microsoft Teams. When creating a team in Microsoft Teams, a shared space is created for the team members in which only they themselves can work. It can be seen as a shared network folder specifically for a group of employees. However, this space has many more features to help team members communicate. An example of this is the ability to have a persistent chat.
Some examples of spaces with Team security scope are: project spaces, work groups, departmental spaces, training spaces, etc.
Portal security area
This area is an extension of the previous one because it allows exposing team information to the rest of the company's employees. In other words, we divide the workspace into two parts: a private part where team members can work securely without anyone outside the team being aware of the information contained; a public part where any employee can consume the information that the team wishes to publish.
For this purpose, SharePoint Online is the most suitable tool. Due to its nature for document and web content management, it is ideal for publishing content and exposing it through existing web components configured on its pages. We consider these elements as the public part but, for the private part, we can also create and configure its elements so that team members are the only ones to access and collaborate.
Note that Microsoft Teams has a SharePoint Online site to manage its document content.
Some examples of spaces with Portal security scope are: departmental or area spaces, general training spaces, human resources spaces, business knowledge spaces, etc.
Enterprise security area
Finally, this security scope is the least restrictive. Existing content is created by any employee of the organization and can be expanded with further information such as comments, discussions, questions, etc.
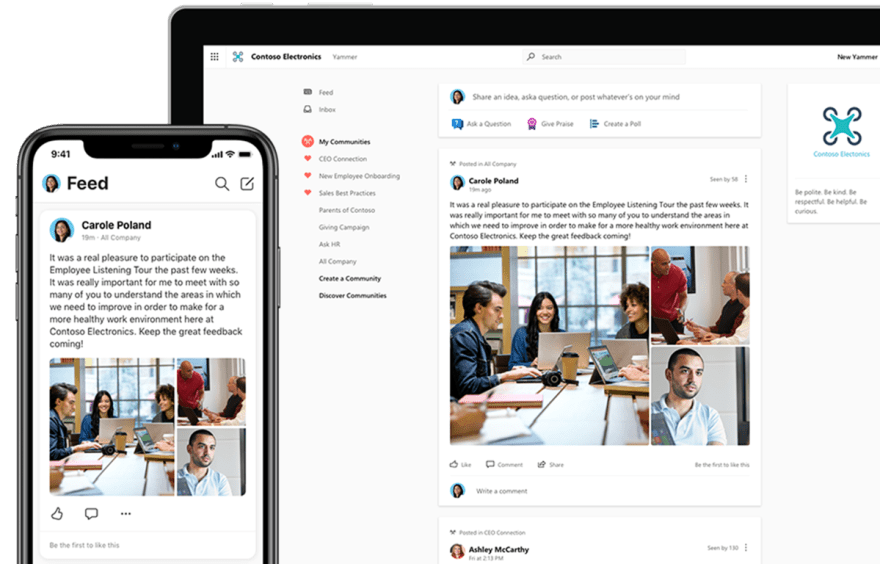
Yammer is the tool whose features are appropriate to meet the above definition. In Yammer you can create open communities where any employee can subscribe and receive notifications of new published content. Or, you can simply search for any relevant content and find related communities, conversations, discussions or questions. If you want to add more information or ask a specific question, you can do so without belonging to that particular community.
Some examples of spaces with Enterprise security scope are: knowledge communities, training communities, FAQ communities, welcome communities, etc.
To wrap up
The exercise carried out in this article establishes some rules for the use of Office 365 tools based on the privacy of the information and who manages it. We can make other classifications based on other premises and even suggest other tools for the security areas defined here. However, in my view, this is a good classification and a starting point for more complex models.
Feedback
If you liked this article, do not forget to click on the heart or the unicorn and share it with your friends and colleagues. Leave me your comments at the bottom about what you liked or how to improve and if you want me to write about other topics send me a direct message to my Twitter account.
Credits
The header image comes from Unsplash and is courtesy of Kaleidico.





Top comments (0)