DAY 12 - 👮 Monitor unauthorized SSH attempts on your server.
✅Connect with me on Twitter
🤝🏽Connect with me on Linkedin
🧑🏼🤝🧑🏻 Read more post on dev.to or iCTPro.co.nz

Tweet This Blog - Read on GitHub - Read On iCTPro.co.nz
PWN ing your server is one of the scariest thing , Monitor your server from unwanted SSH attempts.
Getting unauthorized access to your server is usually main motive for attacker, Monitoring the SSH attempts will help you to understand and take proper remediations before the server gets compromised.
📋 Table of Contents
- Install CloudWatch log agent and Configure.
- Create Metric and Setup SNS Notification.
- Get alerts for unauthorized SSH access.
👀 Install CloudWatch log agent and Configure.
Step 1 Install CloudWatch log Agent
Step 2 Configure awslogs.conf
- Editing this file will help you to deliver custom logs to cloud watch
sudo nano /var/awslogs/etc/awslogs.conf
- add this information, make sure you change to your Log group name . if you have followed Step 1 tutorial , the name will be Ec2-Log-Group.
[general]
state_file = /var/awslogs/state/agent-state
[logstream1]
file = /var/log/auth.log
log_group_name = Ec2-Log-Group
log_stream_name = {instance_id}
datetime_format = %b %d %H:%M:%S
- restart the awslog service
sudo service awslogs restart
- Test SSH failed attempts
sudo tail -f /var/log/auth.log
Now if you try with a un-auth name or key , you will be able to see the attempt here.
Verify in CloudWatch log group
- Goto Cloudwatch Dashboard and go to your log group and select your Stream.
- Search for invalid user
Create a metric filter for SNS
- when your verify , you can see an option for create metric filter
| Comments | Screenshots/Action |
|---|---|
| Create Metric Filter | |
| Name the filter and add metric value and click Create |  |
| Test the metric you have created , goto loggroup and click Metric filters | |
| select the filter and click edit, Now select your server and click Test pattern, if everything is good you can see your results | 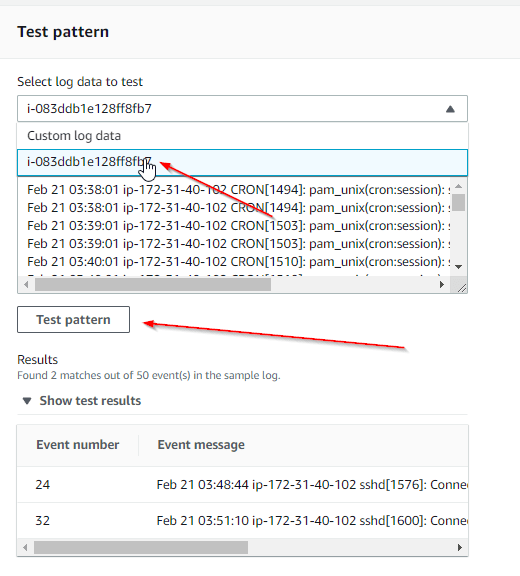 |
| Select the Same metric filter and then click Create alarm to create one |  |
| Change the period to 1 min or less |  |
| add Conditions and click next |  |
| Create SNS TOPIC to deliver email alert, Click Create topic | 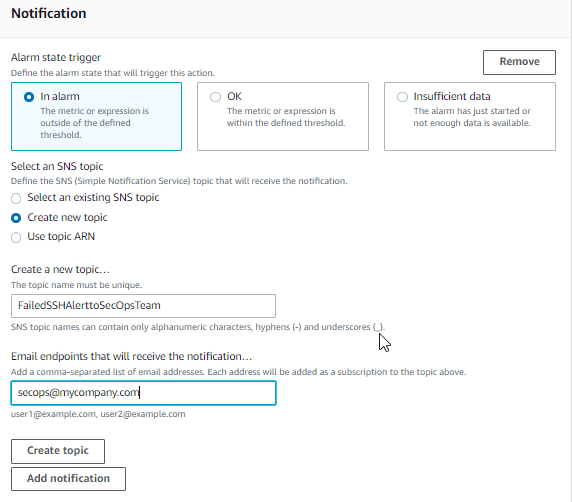 |
| Name Alarm name and Alarm description |  |
| Now Click Next and Create alarm |
Lets Test for un-Authorized SSH Access.
- go to your mail and subscribe to the email that you have received.
- Now goto putty , enter a different user name and try accessing the server.
- if you check the alarm state you can see its changed to 🔴In alarm.
- Now check your registed email, You can see
🎉Congratulations🎉 you have successfully configured your alert to monitor Failed SSH attempts.






Top comments (0)