Table Of Contents
Day 1️⃣3️⃣ - Linux Enumeration, Discovering and Priv Escalation
👣Steps
- Initial access
- The first few questions only need to follow the info provided in the questions
- After running
nmap {machine IP}, out of the 3 open ports telnet is the old, deprecated service that stands out. - To get the password, just run
telnet {machine IP} {telnet port number}. The username and password are shown in the login welcome messages.
- Enumeration
- Run the 3 commands recommended by the questions to learn more about the machine
cat /etc/*releaseuname -acat /etc/issue
- The answer for the first question is shown in the output of the first command above
- Running
cat cookies_and_milk.txtwill show the answer for the question ofWho got here first?
- Run the 3 commands recommended by the questions to learn more about the machine
- Privilege Escalation via DirtyC0w 🐮
- The question provided a link that contains more info about this exploit.
- That link contains this page where it has a lot of proof of concepts (POCs) for this exploit.
- However, non of them is the one that this question intend us to use.
- Ended up using grep.app to search code online to find the original code.
- The search string used is
struct Userinfo user;
- The search string used is
- All the top search results are the correct original dirtyc0w C source code
- Choose the C file in exploitdb even though it's filename is not correct because exploitdb is a known repo to me
- The answer to the question on how to compile the code is found in line 17.
- The subsequent question is what is the new user that is created when ran using the original source
- The answer can be found by reading the original source
- The answer is in line 131
- Lastly, to obtained the flag ⛳
- first create a file named dirty.c, then copy all the content of 40839.c into in
- This can be done in various ways, what I did were the following:
touch dirty.cnano dirty.c- Paste all the content by right click / shirt-insert / any other paste shortcut of your terminal
-
Ctrl+oto save to file - Followed by
Ctrl+xto exit the Nano text editor
- This can be done in various ways, what I did were the following:
- run
gcc -pthread dirty.c -o dirty -lcryptto compile the exploit - run the exploit ->
./dirty- enter any new password for
firefartuser
- enter any new password for
- Either background the current process, or open another telnet connection
-
su firefartto attempt to switch user to firefart- enter your new password
- read the message left by prepertrator as mentioned in the question
cat message_from_the_grinch.txt- inside it explains what it means to "leave behind the coal"
- perform the action explained
- finally run
tree | md5sumas explain in the text file and the question - flag obtained == profit 💰
- first create a file named dirty.c, then copy all the content of 40839.c into in
Day 1️⃣4️⃣ - OSINT (Open Source Intelligence)
🧠 Info
- Tips & tricks
- Use search engine query as a precusory scan through the internet
- The use of special symbols such as quotes, negative sign etc goes a long way reveal just the results that we wanted
- Directly search the site itself rather than using search engine might reveals desirable results
- Example, reddit & twitter
- Uses different search engines or niche search engine for a specific search type
- For example, use SymbolHound to search for query that contains special characters.
- Use image searches to search for visually similar images
- Use breached data
- Tools to search for user accounts across social media platforms.
👣Steps
- Task #1
- To begin, search for
reddit IGuidetheClaus2020in DuckDuckGo - Go to the first result, clicked on the
commenttab and the URL is the answer for the first question - For the second question, the answer is in the
overviewtab - Google'd
IGuidetheClaus2020 creator robertwill reveals IGuidetheClaus2020's creator last name - Along side IGuidetheClaus2020's creator, among the search results is IGuidetheClaus2020 twitter account. This is the answer for the fourth question
- To begin, search for
- Task #2
- In a few of the retweets, IGuideClaus2020 mentioned a TV show.
- Two of the tweets mentioned about parade, with the first one explicitly giving hint about going to a parade
- Performing a visual search of the image will reveal in which city the parade is held.
- The question about where exactly the parade image is taken is the most technical so far
- First, find an image metadata viewer AKA EXIF viewer. Search for
online exif data viewerand use the first result. For me it is https://onlineexifviewer.com/ - Using this we can avoid the need to download and install a software
- Using the 2 URLs of the 2 images of the parade, we found that they don't contain any EXIF data.
- However, another post shared a high quality photo of one of the parade image.
- Using that URL in https://onlineexifviewer.com/ reveals the exact GPS location coordinate.
- Round down the precision to 6 decimal will yields the answer.
- In the same EXIF data, there's a flag in the
copyrightfield
- First, find an image metadata viewer AKA EXIF viewer. Search for
- The question about has Rudolph been pawned and what password of his appeared in a breach is a more open ended question
- There is hints in the task#2 description where it mentioned questions #6 -11 can be solved by using info on his twitter account
- Steps to answer this question is as follows
- Follow the steps in this site to use Scylla
- However, found out that the tools are outdated and don't work on the current Twitter
- Visit the twitter user page and noticed the email is listed in the user description
- Use haveibeenpwn to search and it only mentioned about the password is being breached in LiveJournal
- Search online for more data breached site and came across breach directory
- Here it shows two sha1 which hints of what are the password
-
live************: 7ae929950f2d937538eee064371ceb612ed9c59e -
spyg***: 6e3f262dccc80924be40aa96554ce5df182e939a
-
- Then, use a site called md5decrypt to search for the decryted password. Usually the sha1 of common password are easily searchable without the need to crack 🦀 them ourself
- For the question of what is the street number of the hotel Rudolph is staying
- Originally can't figure out where to start.
- However, after some pondering and failed online search got a relization that this question probably is asking about Rudolph when he is in Parade as those twitter post will still be consider new during the time this CTF is on-going
- Check the EXIF data of the parade high-res photo using https://onlineexifviewer.com/
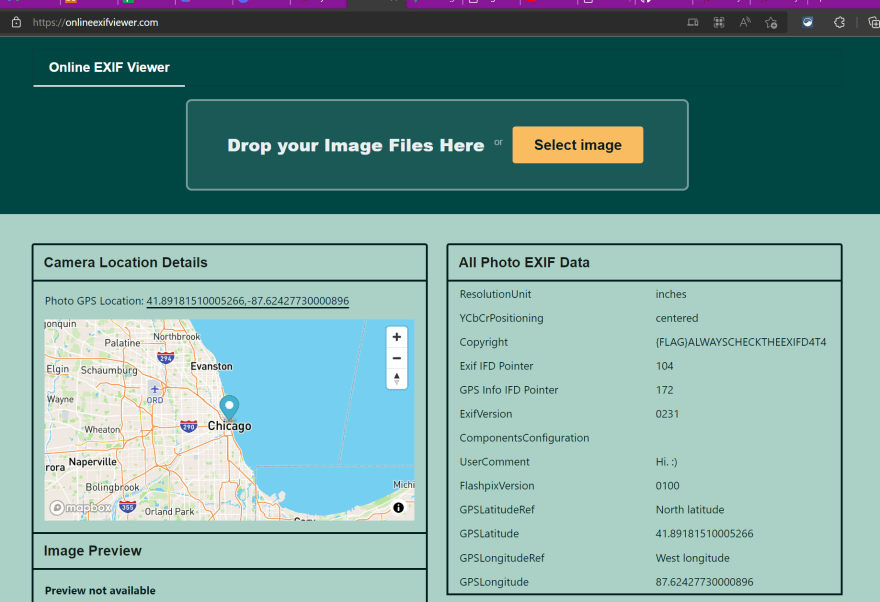
- Opening the GPS coordinate using google map, and search for the closest hotel.
- The street number of the hotel address is the answer to the final question

![Cover image for AoC 2 [2020] TryHackMe CTF 🐱💻Day 13 & 14](https://media2.dev.to/dynamic/image/width=1000,height=420,fit=cover,gravity=auto,format=auto/https%3A%2F%2Fdev-to-uploads.s3.amazonaws.com%2Fuploads%2Farticles%2F7z0vnxr9jn5bams06n6l.png)

Top comments (0)