Is it really how hacking looks ?
You have probably seen many movies where hacking is portrayed like this..
Wait... what does it actually mean ?
Let's understand what hacking actually is!
From the point where you are casually browsing the web to the point where your social media accounts were hacked, Hacking happened. The hacker was able to take over your digital life but how did he manage to do that. He might have done one of these 3 things.
Let's talk about them in detail...
1. BREACHES :
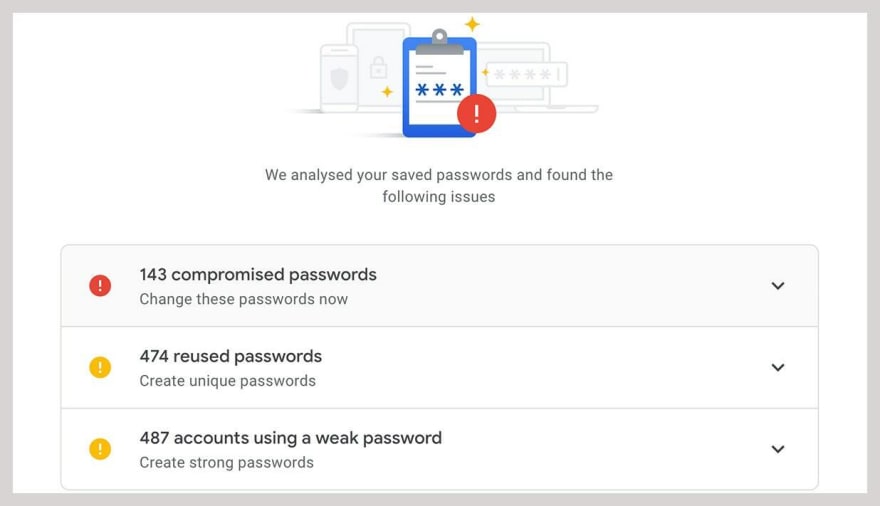
Believe me or not, your passwords are probably already out there, publicly available on the internet without even your knowledge. This might feel a bit unconvincing but it's true that there is a chance. But how is this actually possible that your credentials are publicly available on the internet..? This is because of the data breaches.
When hackers manage to hack a website and get access to the website database, they leak/sell all this data like (user's credentials and details) on the internet, on hacker's forum, Dark web, PasteWin; it's the hacker's choice of course. So, if you are user of the website that got breached, your data is leaked too.
Most of the websites, pre-hash your passwords before they store it in the database with a fast hashing algorithm (such as SHA-256, Argon2id, PBKDF2, etc..). But most of the data breaches on internet contain plain text passwords. Many famous websites like LinkedIn, Twitter, 000webhost, etc.. already suffered major data breaches and all these breaches are publicly available on the internet.
If you want to check whether your credentials are included into any data breach, visit click here and enter your email. Even though your results are positive on this site, your data might be still in one of the breaches which is not popularly known but still exists.
The best way to stay away from data breaches is to use different passwords for different websites.
2. SOCIAL ENGINEERING :
This is literally, you giving away your login credentials to a stranger on the internet. Hackers can pretend to be someone else to try to extract your crucial information directly from you.
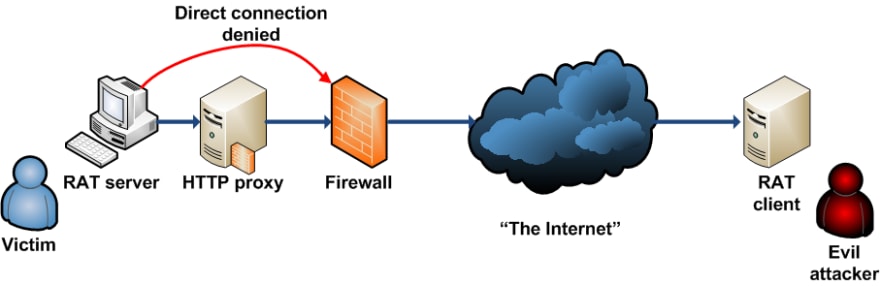
A hacker can still install a Remote Access Trojan (RAT) through social engineering by linking it to the cracked software, phishing attacks, etc.. which gives remote access to the hacker. With this, the hacker will be able to control your system from a remote server.
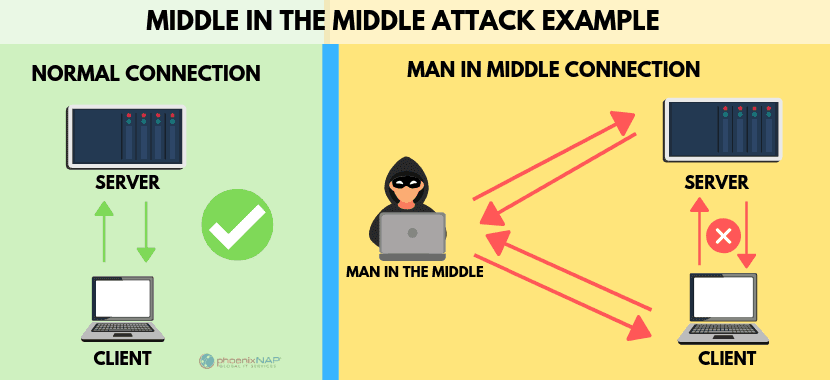
3. MAN IN THE MIDDLE :
Now this type of hacking is not very likely to occur but there is a chance that you might get hacked by Man in the middle Attacks. In this attack, the hacker puts himself as man in the middle between you and the internet you are browsing.
Targets are typically the users of financial application sites, businesses, e-commerce sites, and other websites where logging in are required. Information obtained during an attack could be used for many purposes, including identity theft, unapproved fund transfer, or an illicit password change.
Broadly speaking, a man in the Middle attack is the equivalent of a mailman opening your bank statement, writing down your account details, and then reselling the envelope and delivering it to your door.
There are some practical tips to prevent the man in the middle attack, such as
a. Avoid Wi-Fi connections that are not password protected.
b. The next one is, to log out immediately from a secure application when it is not in use.
c. The third one, Avoid using public networks such as coffee shops and hotel WIFI when conducting sensitive transactions, etc...
Wanna know more about some of such similar and famous Cyber Attacks ?
Check out this
Written by -- Gudi Varaprasad








Top comments (0)