A big problem with blockchains is that you can't know the code behind an on chain program, meaning you would have to blindly trust a protocol with your signature, not being able to verify what's really going on behind the scenes.
That's why a lot of companies and projects publish their programs code to build trust. But now the problem is, "how can I be sure the public source code is the same as the deployed programs source code ?".
That's why Ellipsis Labs has built a build verification CLI, which can be used to compare an on-chain program byte code to the build output when you build its underlying program.
Let's now take a look at how you can create a program and verify it using Ellipsis Labs verifiable builds.
Creating a program
First of all, initialise your program:
anchor init verifiable-build
Now let's add a little functionality to our program so it isn't the boring standard one.
Replace the existing content with the following code in programs/verifiable-build/src/lib.rs:
use anchor_lang::prelude::*;
use anchor_lang::system_program;
declare_id!("AD62W7aAQETg11ajkadk57DYfPTWPzKLiXuLZVB4eQaw");
#[program]
pub mod verifiable_build {
use super::*;
pub fn transfer_sol(ctx: Context<TransferSol>, amount: u64) -> Result<()> {
system_program::transfer(
CpiContext::new(
ctx.accounts.system_program.to_account_info(),
system_program::Transfer {
from: ctx.accounts.payer.to_account_info(),
to: ctx.accounts.recipient.to_account_info(),
},
),
amount,
)?;
Ok(())
}
}
#[derive(Accounts)]
pub struct TransferSol<'info> {
#[account(mut)]
recipient: SystemAccount<'info>,
#[account(mut)]
payer: Signer<'info>,
system_program: Program<'info, System>,
}
Let's build the program now:
anchor build
Deploying your program
First, let's set the network we want to deploy our program on, I will be doing it on a local Solana validator.
Set your network running this command:
solana config set -c --url l
Now launch a local solana validator in a separate terminal:
solana-local-validator
And now deploy your program
anchor deploy
Verify the deployed program
Now comes the important part. Let's verify that the byte-code of the program we just deployed matches the program we've written.
Install the verifiable-build CLI
cargo install solana-verify
Get local executable hash
First, let's get the hash of the build output from our program:
Here, make sure to use the program's lib name, found under [lib] in Cargo.toml.
solana-verify get-executable-hash target/deploy/verifiable_build.so
This is the output we get:
Get hash from program bytecode
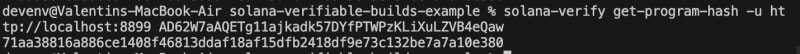
And now let's get the hash of the program bytecode:
Here, replace $PROGRAM_ID by the program id of your deployed program.
solana-verify get-program-hash -u http://localhost:8899 $PROGRAM_ID
We can see here that both of the hashes are the same, meaning we've proven that the program you've built locally corresponds to the one you've deployed.
Verify an on chain program from a Github repository
For this, I've created a Github repository with the program we've just built and also deployed it onto the Solana devnet.
You can do the same but don't need to, as you can just use this with the repository I have created.
Verify hash between repo and program
To verify a hash between an on-chain program and a GitHub repository, run this command in your terminal:
solana-verify verify-from-repo -ud --program-id AD62W7aAQETg11ajkadk57DYfPTWPzKLiXuLZVB4eQaw https://github.com/valentinmadrid/solana-verifiable-builds-example
If the hash from both of these programs match, you can consider a program's source code to be verified.
Conclusion
Verifiable builds are really important. That's why it's great to see companies like Ellipsis Labs coming up with amazing ways of verifying if the code of an open-source program matches it's deployed version.
This is a great step forward for achieving a better open source culture on Solana. But, we still have ways to go. It would be amazing to see projects take initiatives to build tools such as a registry of verified programs for explorers, GitHub workflows that can update a verifiable hash in a database each time a program is updated or even wallets that integrate verifiable builds to spot harmful program interactions.
Thanks for reading this post. Feel free to drop any feedback on my Twitter: @valentinmadrid_.



Top comments (0)