Injection attacks are one of the top three most common security breaches according to OWASP Top 10. Injection attacks pass a string of code as an input to a web app, which alters the operation of the application by executing certain commands. One of the most common injection attacks is SQL injection.
Why is SQL Injection Used?
SQL Injection can be used by attackers to:
Bypass Authentication - Attackers can pass a piece of code to the database that allows them to bypass the authentication process.
SELECT * FROM users WHERE username = '' OR 1=1-- ' AND password = 'foo'
What will happen here is 1=1 will return 'true', and everything after '--' will not be executed because '--' is used to comment out code in SQL, so the rest of the query will be ignored.
Exfiltrate Data - There are many areas that can be exploited to steal data from a targeted source. A common HTTP Server request could look like this:
SELECT * FROM users INTO OUTFILE '/var/www/html/output.txt'
This will select all from users table and export that data as a text file.
Execute OS commands - Beyond databases, attackers can gain access to an entire operating system and run system commands. SQL injection attacks are often used as a vector for gaining command of the shell. If an attacker has enough information about their target, they can pass something like this:
' union select 1, '<?php system($_GET["cmd"]); ?>' into outfile '/var/www/dvwa/cmd.php' #
This piece of PHP code will allow the attacker to execute os commands. They will have access to the shell via their browser.
<?php system($_GET["cmd"]); ?>
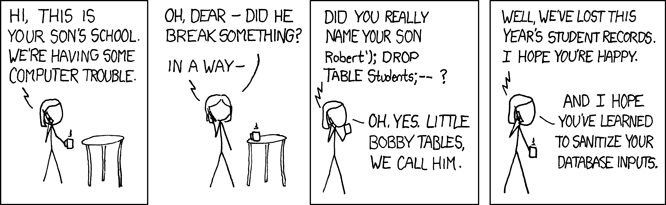
Vandalism/DoS - Attackers can drop tables from a database and otherwise break things with SQL injection. Here is one of my favorite comics:
Prevent SQL Injection
Here are some steps can be taken to prevent SQL injection attacks:
Sanitize all inputs. Basically, the client input cannot be trusted. Use whitelists and when possible, do not let user directly communicate with the database. Perform server-side validation.
Do not expose native database errors. Attackers can use database errors to learn more about your database and find vulnerabilities.
Use Object Relational Mapping (ORM). ORM creates a layer between the language and the database. In Rails, ActiveRecord translates between Ruby and SQL. This is mostly secure, but some things can still be exploited.


Top comments (0)