One of mine website stopped working with the “Connection reset” error.
NGINX configs seem to be correct, and other sites on the same server are working.
NGINX also gave nothing, no errors, PHP-FPM also are good.
Let’s check the website with the curl:
$ curl -Iv [https://example.setevoy.org.ua/](https://example.setevoy.org.ua/)
* Trying 139.59.205.180:443…
* Connected to example.setevoy.org.ua (139.59.205.180) port 443 (#0)
* ALPN, offering h2
* ALPN, offering http/1.1
* successfully set certificate verify locations:
* CAfile: /etc/ssl/certs/ca-certificates.crt
* CApath: none
* TLSv1.3 (OUT), TLS handshake, Client hello (1):
* OpenSSL SSL_connect: Connection reset by peer in connection to example.setevoy.org.ua:443
* Closing connection 0
curl: (35) OpenSSL SSL_connect: Connection reset by peer in connection to example.setevoy.org.ua:443
The cause
Because the error above are reported from the SSL_connect call, then the first thing to check was the website's certificate, although if it was expired, then the error must be different.
Still, go to try to renew the certificate:
root@rtfm-do-production-d10:/etc/nginx/conf.d# certbot renew
…
Attempting to renew cert (example.setevoy.org.ua) from /etc/letsencrypt/renewal/example.setevoy.org.ua.conf produced an unexpected error: Failed authorization procedure. example.setevoy.org.ua (http-01): urn:ietf:params:acme:error:dns :: DNS problem: SERVFAIL looking up CAA for setevoy.org.ua — the domain’s nameservers may be malfunctioning. Skipping.
…
“DNS problem: SERVFAIL looking up CAA for setevoy.org.ua — the domain’s nameservers may be malfunctioning.” — okay, now we’ve got more details and a new error.
But why the error appears from the top-level domain — setevoy.org.ua? And why Let’s Encrypt checking the CAA record? Previously, everything was working without it.
Anyway, let’s go to check the DNS of the domain — find them:
root@rtfm-do-production-d10:/etc/nginx/conf.d# whois setevoy.org.ua | grep nserver
nserver: ns-1083.awsdns-07.org
nserver: ns-2030.awsdns-61.co.uk
nserver: ns-271.awsdns-33.com
nserver: ns-721.awsdns-26.net
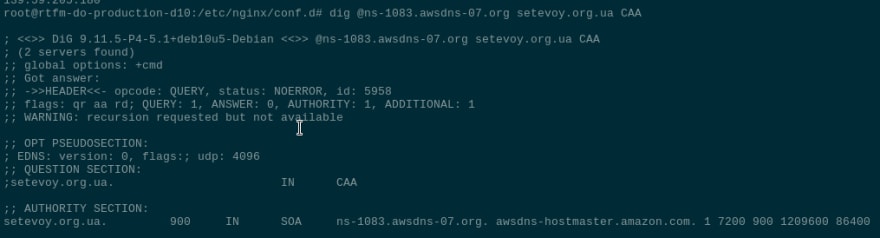
Check, if a server returns an answer:
root@rtfm-do-production-d10:/etc/nginx/conf.d# dig @ns-1083.awsdns-07.org setevoy.org.ua +short
139.59.205.180
All is good here.
Go to the Google, and find a discussion тут>>>, and this topic from Namecheap.
Go to check if I have CAA on the root domain:
Um… But Google has it:
root@rtfm-do-production-d10:/etc/nginx/conf.d# dig google.com CAA +short
0 issue “pki.goog”
And rtfm.co.ua, by the way, also hasn’t it, and everything is working here (yet). Maybe, it will break on the next renew, will see.
The solution
Go to the Route53, add a new record:
Choose its type as CAA, set its value as 0 issue "letsencrypt.org" to allow issuing SSL certificates from Let's Encrypt:
Check, if DNS were updated:
root@rtfm-do-production-d10:/etc/nginx/conf.d# dig setevoy.org.ua CAA +short
0 issue “letsencrypt.org”
Try to run certbot renew again:
root@rtfm-do-production-d10:/etc/nginx/conf.d# certbot renew
…
Congratulations, all renewals succeeded. The following certs have been renewed:
/etc/letsencrypt/live/example.setevoy.org.ua/fullchain.pem (success)
Done.
Originally published at RTFM: Linux, DevOps, and system administration.





Top comments (0)