 Still on the subject of the Okta and SSO for Jenkins – let’s configure a Role-Based Security plugin for our Jenkins. See the first part in the Jenkins: SAML Authentication with Okta SSO and users groups post.
Still on the subject of the Okta and SSO for Jenkins – let’s configure a Role-Based Security plugin for our Jenkins. See the first part in the Jenkins: SAML Authentication with Okta SSO and users groups post.
The general idea is to have user groups defined in the Okta, and Okta has to pass a user’s group when he will log in to the Jenkins.
Then Jenkins has to assign correct permissions for this user based on its group(s).
The Role-Based Security plugin configuration
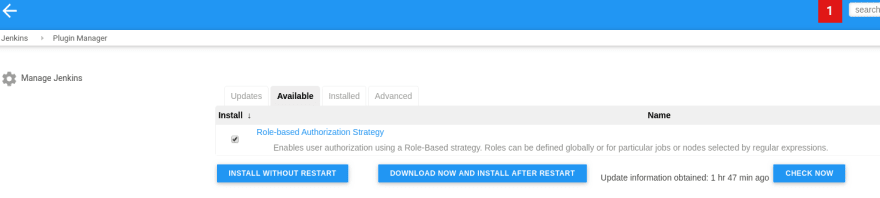
Install the Role-based Authorization Strategy plugin itself:
Go to the Configure Global Security, switch the button to the Role-Based Strategy:
Go to the Manage and Assign Roles:
Create roles – global roles
Roles here are divided into three areas:
- global roles: obviously, global roles for global permissions, such as create/delete Views, Jobs, Overall
- project roles: the permission settings on a per-project basis – jobs are limited by a regular expression
- agent roles: Jenkins slaves/workers/agent permissions
If you’ll try to log in right now – will face with the “ missing the Overall/Read permission ” error:
To avoid it – we need to create a global role with the Overall Read permissions.
Go to the Manage Roles:
Create a new global role called read_all and set permissions to the Overall – Read:
Save.
Assign Roles
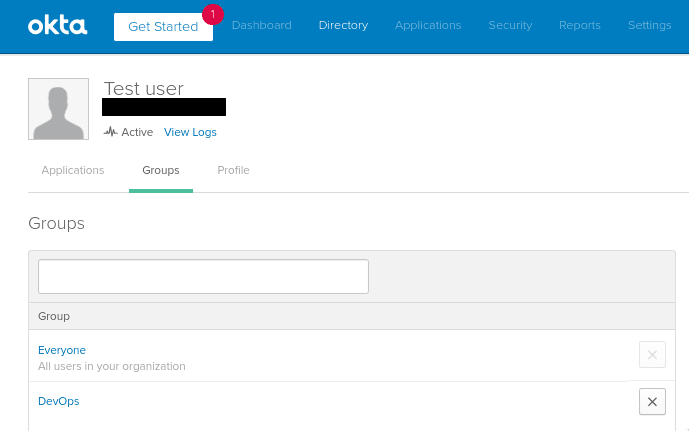
For example, let’s take a Test user:
It has two groups assigned – the Everyone and the DevOps.
Go to the Assign Roles, add the Everyone group and assign the read_all to it:
Save and log in under this user:
Okay – you are able to log in, but can’t see any jobs right now.
Project roles
Next, need to create roles to grant access to various jobs/views.
For example, we have an Android view with jobs for our Android-developers:
Go to the Manage Roles, add an android_developer role and in the Pattern set the (?i)android_.* value – here, with the (?i) we set to case-insensitive search and with the android_.* – will select all Android jobs:
You can click on a regex to see which jobs will match the filter you set in the Pattern:
Go to the Assign Roles, attach the android_developer role to the Android group:
Okta Groups
Go to the Okta, add the Android group to our test user:
Log in with this user:
Awesome – we are able to see only Android jobs and views.
In the same way let’s create another role – ios_config, for iOS, but this time – with the Configure permissions:
Assign this role to the iOS group:
In the Okta attach the iOS group to the Test user:
Log in and you’ll see iOS jobs now:
And the Configure permission is working:
Backup
Security Realm, groups, and users which you created in the Jenkins will be saved in the config.xml file:
So it’s good practice to back up this file before changing any Security Real settings.
Done.





















Top comments (1)
Hi,
Could you please present a demo spring boot app to authenticate user with okta using SAML protocol.
Could you please show how to use spring's "SAMLAuthenticationProvider"