The Secure Shell, or SSH, protocol plays an essential role in providing encrypted and secure communication between devices. In Cisco device, strong authentication is essential. This article uses SSH keys for authentication to Cisco devices using PuTTY as the interface in a Windows environment.
SSH key usually consist of a public and private pair, providing a more secure alternative to password-based authentication. PuTTY, a popular SSH client for Windows, includes PuTTYgen, a utility that simplifies the creation and maintenance of SSH keys.
Prerequisite:
Download PuTTY and PuTTYgen on your local Windows, if you don't have.
Generating SSH Key Pair with PuTTYgen:
Open PuTTYgen, to generate public and private key for secure connection.
Move your mouse over the blank area to generate randomness.
Select key type:
Select the key size and key type.
Save the Keys:
Click on Save private key to save the private key. This file generally has a .ppk extension.
Click on Save public key to save the public key.
Configure PuTTY connection:
Open PuTTY on your Windows, enter your remote server public IP address or username in the Hostname section.
Set the connection to SSH and port to 22.
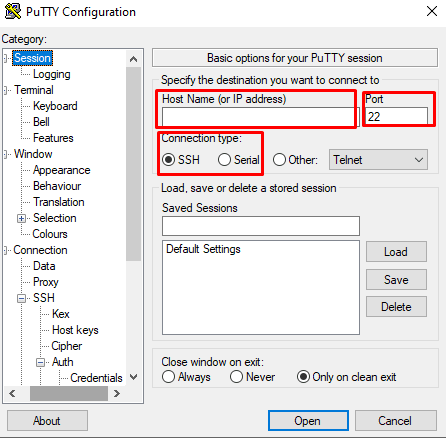
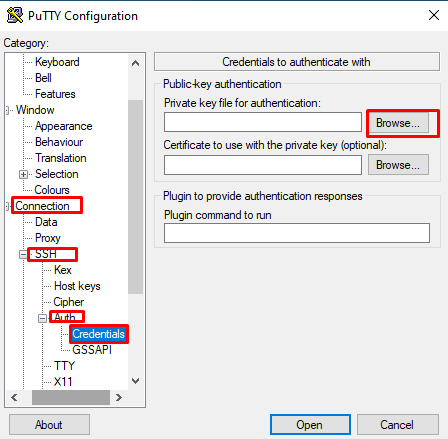
On the left panel, navigate to the Connection>SSH>Auth category.
Click on Browse and select the PuTTYgen-generated private key.
Saving session:
Enter a name in the Saved Session section and click on save to save the connection for later use.
Establish the connection:
Click on Open to make the connection.
Enter the username and password when prompted.
Using PuTTY for enabling SSH key authentication for Cisco devices provides a secure and efficient solution to access and manage network devices. By eliminating the need for password-based authentication, SSH keys improve security by lowering the risk of unauthorized access and potential security breaches.







Top comments (0)