HTTP Parameter Pollution or HPP in short is a vulnerability that occurs due to passing of multiple parameters having the same name.
What is Parameter Pollution?
HTTP Parameter Pollution or HPP in short is a vulnerability that occurs due to passing of multiple parameters having same name. There is no RFC standard on what should be done when passed multiple parameters.(Wikipedia)
How Node.JS (Express) Reacts to Parameter Pollution
There are various ways of passing parameters in order to cause a problem and we can see the list of some possible ways in this table:
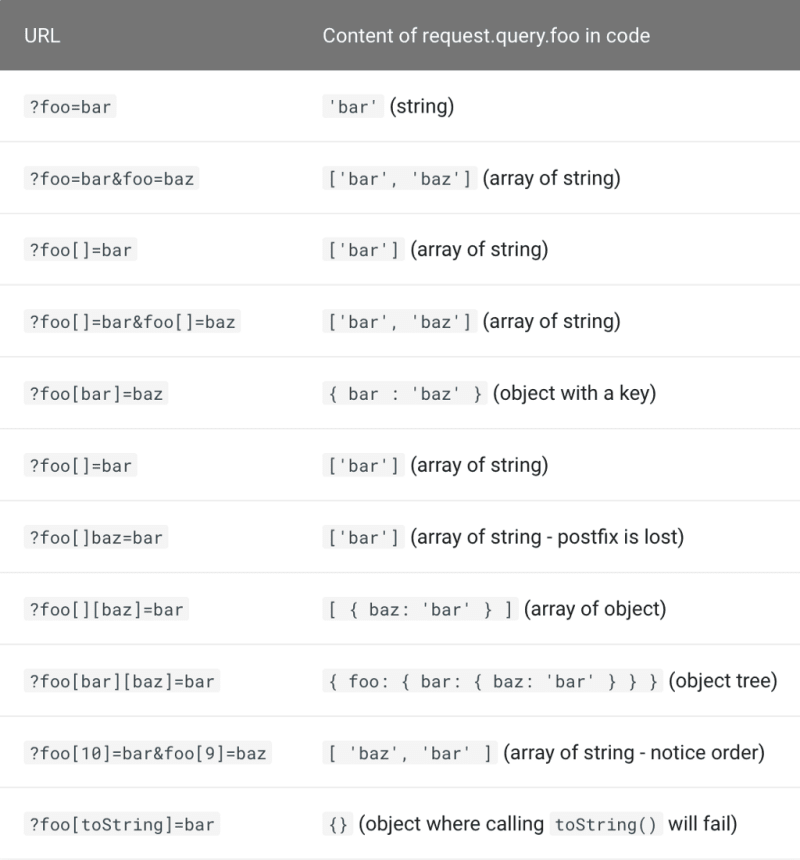
Different ways of passing parameters
Now that we are cognizant of various forms and problems that someone can cause by passing parameters we can say that we must take it seriously. Let’s see how validators react to parameter pollution:
Two Node.JS Validators Reaction to Parameter Pollution
1-express-validator
This library is one of the most common Javascript libraries and it is built on top of the validatorjs library.
We have a simple express server that we want to send the email and after validating that we want to do something:
https://medium.com/media/2bd7079f8e8a6be13f98360ffb59458a/hrefWhat happens when we try to pollute the parameters?
As you can see if we pass the first parameter a valid email we can bypass the validation and guess what I have on my console (line 9 of the code)?
Now we have an invalid email that might be saved into the database. Let’s hope that the attacker is sending I'm malware or something like alert("I'm a happy hacker") .
You might argue that we are going to send POST method and not get so this is the POST method example:
https://medium.com/media/0c0439820a911fb2c5366d9149ec2cfb/hrefLet’s see what is the result this time:
As you expect the email log is { email: [‘test@gmail.com’, “I’m the same malware” ] }
2- Joi
Joi is another popular validation library. Let’s see how Joi reacts in the same situation:
https://medium.com/media/9ed0ab6a96f79b3b6feef981756ca26b/hrefLet’s see the result
As we can see Joi understands that this is not a string. Also if we use validator.js directly we are going to see a result like this and the problem of the former examples was express-validator.
How can we prevent parameter pollution?
We have two ways:
- Using a library
- Implement our own function
There is a useful library(unfortunately it seems that it is not maintained regularly) called hpp
Using it is a walk in the park and we can use it by adding it as a middle-ware to our express app:
app.use(hpp());
After adding this line, if we pass a parameter more than once it changes the query to this:
GET /search?firstname=John&firstname=Alice&lastname=Doe
=>
req: {
query: {
firstname: 'Alice',
lastname: 'Doe',
},
queryPolluted: {
firstname: ['John', 'Alice']
}
}
It moves that parameter to queryPolluted and takes the last value.
Also you can add an exception since sometimes we want to pass an array.
What can we implement to prevent Parameter Pollution?
let’s implement a simple middle-ware:
https://medium.com/media/e94c77c3b8aa0f04d336392fd5e106b1/href
hppProtector is the middleware that is accountable to handle hpp. We simply iterate over the parameters and if the type is not string we check that, if the type is array we are choosing the first one(We could choose the last one too), if the type is object we send a bad request error because the user is sending something like this: email[as][ds]=something . This is just a simple example, do not rely on that.
Let’s see what happens when we send requests:

Simple HPP Implementation Result
In this case, the parameter generates an object and we send bad parameters error.
Let’s send a parameter more than once:

Passing One Parameter more than once to our HPP Implementation
The result of req.query.email is test@gmail.com since we use the first element of the array.
Summary
Parameter Pollution is a vulnerability that occurs due to passing of multiple parameters having same name. Some validation libraries are vulnerable to this kind of attack so we should handle this attacks using a library or our own implementation.
Nodejs Security - OWASP Cheat Sheet Series










Top comments (0)