Welcome to another article on network forensics. We are still talking about the SMB protocol family, but this time let's focus on messages that carry hints about the connected endpoints. These hints can be used to infer knowledge about the client and server (e.g. OS version). This process is called fingerprinting.
Protocol negotiation
SMB1 NegotiateProtocolRequest (smb.cmd == 0x72) carries information about the dialects that the client understands. Similarly SMB2 NEGOTIATE request (smb2.cmd == 0) contains a list of client's dialects and SMB 3.x capabilities. These bits are specific to client implementation (or configuration) and thus can be used as part of the client's fingerprint.
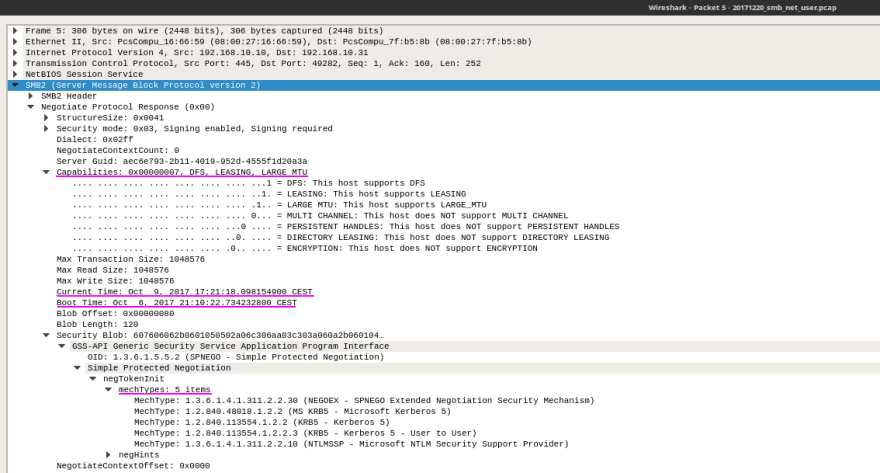
The same applies for the response as well. Fields like server capabilities
(smb.server_cap), system time (smb.system.time), time zone (smb.server_timezone), boot time (smb2.boot_time) or authentication mechanisms (spnego.mechTypes) can tell a lot about the server endpoint.
Wireshark filter: smb.cmd == 0x72 or smb2.cmd == 0
PCAP sample: smb-on-windows-10.pcapng on Wireshark wiki
NTLM authentication
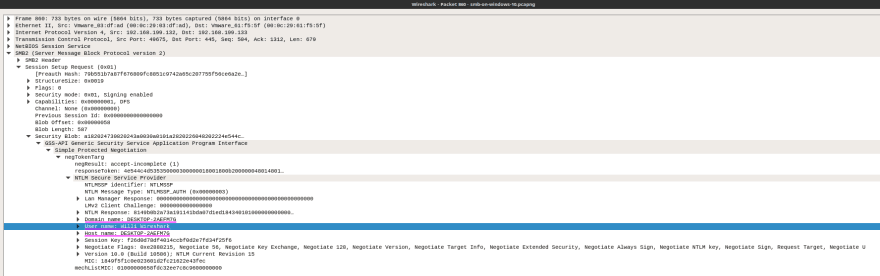
NTLM authentication has been long superseded by a more secure Kerberos, but in my experience it can still be found wildly in public institutions and smaller companies and sometimes even in corporate networks. From a forensic POV we are mainly interested in usernames, hostnames and NTLM hashes:
Wireshark filter: ntlmssp (or gss-api for all negotiation packets)
PCAP sample: smb-on-windows-10.pcapng on Wireshark wiki
Kerberos authentication
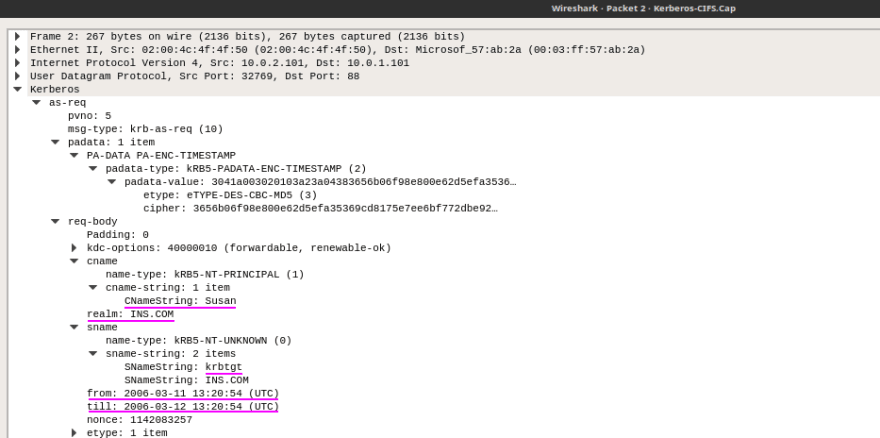
In case of Kerberos there are still useful metadata like realm aka. domain name (kerberos.crealm), principals aka. user/server names (kerberos.cname/kerberos.pname/kerberos.sname), auth period (kerberos.from/kerberos.til) and more.
Also, Kerberos AS-REPs (kerberos.cipher field) can sometimes be cracked to yield credentials e.g. with John the Ripper.
Wireshark filter: kerberos (or gss-api for all negotiation packets)
PCAP sample: Kerberos-CIFS.Cap at pcapr
SPOOLSS GetPrinterData
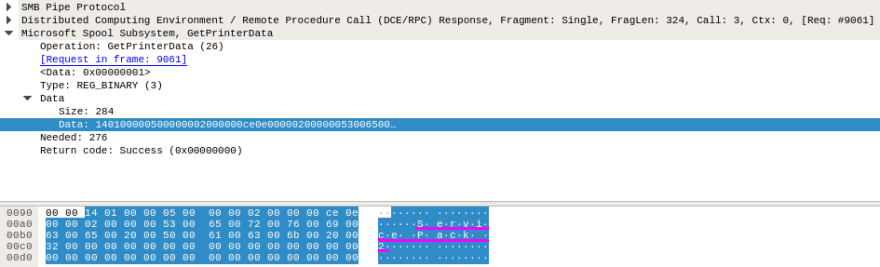
OK this is probably a really niché case, but hey, that's what forensics is all about. When using a shared network printer, MS Spool Subsystem (spoolss) is typically used over SMB/RPC stack. Once that printer is available, the OS can request various printer data using GetPrinterData function. Inspecting these data can reveal interesting bits, e.g. OS Version of the print server.
Wirehsark filter: spoolss.printerdata
If you're interested in reading more about OS/application/device fingerprinting, there's sadly not many links I could point you to. Tools like p0f or nmap can provide a good start. You can also read this post by SecurityTrails which summarizes different means of fingerprinting including SSH or TLS protocols.



Top comments (0)