This is the syllabus we will cover here for the AZ-104 exam.
Managing Azure Active Directory
Identity : Something that can be authenticated ex: A user / service etc.
Account : Data attributes associated with an identity is an account.
Azure AD account: Accounts created in Microsoft cloud or AD.
Azure Tenant /directory: Dedicated instance of an Azure AD which is generally created during sign up of any Microsoft cloud subscription.
Azure active directory (AD) vs Azure active directory domain services (ADDS)
Azure AD pricing
Azure Active Directory comes in four editions—Free, Office 365 apps, Premium P1, and Premium P2. The Free edition is included with a subscription of a commercial online service, e.g. Azure, Dynamics 365, Intune, and Power Platform. Office 365 subscriptions include the Free edition, but Office 365 E1, E3, E5, F1 and F3 subscriptions also include the features listed under the Office 365 apps column. The Premium editions are available through your Microsoft representative, the Open Volume License Program, and the Cloud Solution Providers program. Azure and Office 365 subscribers can also buy Azure Active Directory Premium P1 and P2 online. Sign in here to purchase.
Check out from this link
User accounts
Group
We can have 2 type of groups. 1) Security Groups

While creating a group, you can also see these two:
Moreover, the assigned type can be 1)Assigned
Note: You can not use Dynamic user and Dynamic device in Azure free account. You need Premium 1 or 2 to use these assigned features.
2) Dynamic user: You can set some rules by which if any user follows those, they get assigned to those groups... Or automatically gets added or removed.
While using dynamic user, you have to provide dynamic query.
You have to then provide property, operator and value.

After selecting these 3 options, we get this query:

You can then save that one and create.
Moreover, you can also manually add people and if that person also follows the group rules, then you can see the tick option.

Now, users who follow this rule will automatically get added to this group.
But if you add someone and that person does not follow group rules, you will see a cross .
3)Dynamic device : Devices depending on operating system or others will automatically get into this group. So, you need to share metrics etc here.
While creating a group, you can again check this assigned options:
Azure AD Join
While connecting your device with Azure AD, you can get these features:
Self service Password generation
Basically users will be prompted to set a new password once they login.
This is the features and process we need to go through:
For the admin users, they will be able to set password by default.
But for the others, you need to go to the users or Password reset and then select.

When you choose the selected options,you can choose users to reset their password.

Moreover, you can set the number of authentication the users can set.
Multi tenant/directory environment
No tenant or directory is dependent on other tenant. Check out the features:

So, after going to the Azure AD, you can go to the manage tenants

If we want to create a new one, we can follow this process:

in the configuration page, you can see that we will always have .onmicrosoft.com while creating a new organization's domain.
Then we can create a tenant .
Moreover, we can customize our new tenant with a custom domain name if we wish to.
Finally, we can switch between different tenants by this one.
After pressing this icon, we can see how many tenants we have and which tenants we want to switch.
As we have just one for now, we can see switch options . But it might look like this.
Azure Subscriptions
Role based access control (RBAC)

Here you need to know about security/service principal, role definition (how much a role can access or perform), scope (role's power boundary), role assignment(adding role definition to a service principal at a certain scope)
So, what is role definition?
By default we have certain roles created (Contributor, owner) but if we need to create new roles, we can do that too. It's called Custom roles.
Here you can see the json code for Contributor role.
Sp, what is scope?
It actually means boundary. For example, if we set a role to "Management group" level, even Subscription, resource group and resources will have access to that role.
Again , if we just provide a role access to just the resource group, resource group and resources will have that access.

So, this is how this tree comes in to play.
Moreover, these are the difference between RBAC and AD roles.

You can refer to this picture.
Custom roles :
Roles that we create for our own use.

So, in the Azure portal, you have to go to your subscription and then IAM(Access control)

Here you can see all of the things we have mentioned by far.

Moreover, when we go to the Management group, you can see that my root management group has been provided a subscription key.
Here you can see that, under root management group, all the management groups reside and surely we can assign each management group a different subscription.
Here, all of the management groups under our root management group can now access this subscription key due to the concept Scope we discussed earlier.
Moreover, we can move our subscription from one management group to another.

Just we need to go to the level-1 management group and add subscription. Then we can add it and now level-1 will get access to the subscription, not the root management group.

So, what is the difference?
Actually now not all the management group under root management group can access to the subscription except the level-1 management group.
To check out the roles, we need to go to the management group and go to IAM.

You can see a lots of roles here.

Moreover, if we want to assign some roles to some people, just go to role assignment and then +add

We have given 3 users the reading access of this resource ( meaning the Level-1 management group)

To create a custom role, we have to follow this process.

Now you can filter our your custom role from the roles.
Azure Tags
Tags are used to track and filter a lot of things and they are in name:value pair.

If you go to your resources and choose one, here you will find tags.
Note: The tags that you create on Resources level will be part of billing . So, if you create tag on resource group level,it won't be a part of billing.
Resources Lock

You can add them to subscription , resource and resource group level.

Here we have went to the resources group and choosed a resource group, and you can see the lock here.
Now if you check out this resource under the resource group you created a lock, you will see the resource also inherits this.

The reason in simple. As we have assigned the lock on resource group level, the resources also got that as assigned.
If you now try to delete this resource which has already a lock (that lock won't let you delete this resource),

These are some ways to minimize cost

You can also chain policies together to create an Azure Initiative.

In azure portal , you can see this:
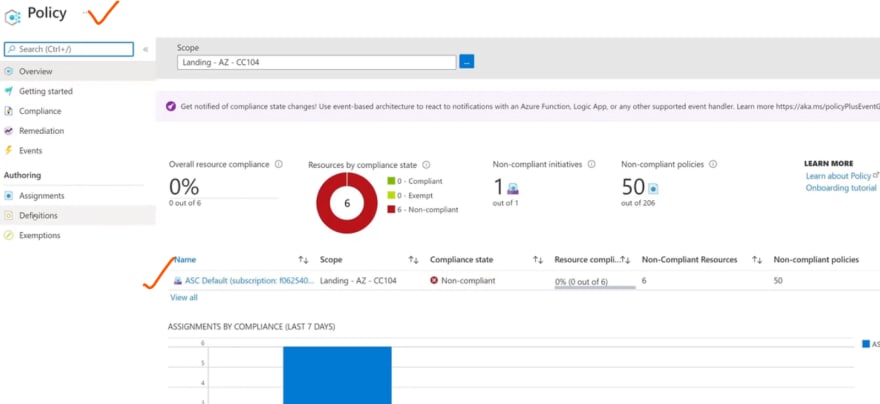
In the definitions, you can find all of the built in policies.

Moreover, this is how you can create initiatives by adding Azure policy definitions.
To learn more about identity and authentication, you can checkout Auth0 website















































Top comments (2)
The AZ-104 exam is a key certification for Azure administrators. For reliable study materials, visit DumpsVibe.com.
dumpsvibe.com/microsoft/az-104-dum...
Dumpsforsure proved to be a valuable resource throughout my AZ-120 preparation. Their questions were not just practice—they helped reinforce core concepts.
Some comments may only be visible to logged-in visitors. Sign in to view all comments.