In the last post we focused on using inlets to create a WebSocket to provide a secure public endpoint for the Kubernetes API and port 8080 for Kasten K10 that are otherwise not publicly reachable. In this post we are going to concentrate on the Kasten K10 and multi cluster configuration. I am going to share a great article talking about Kasten multi-cluster from Dean Lewis.
Deploying K10
Deploying Kasten K10 is a simple helm chart deployment that I covered in a post a few months back here.
➜ kubectl create ns kasten-io
namespace/kasten-io created
➜ helm install k10 kasten/k10 --namespace=kasten-io
Accessing K10
For the purposes of this demo, I am just port forwarding each cluster out, but you could use ingress to expose to specific network addresses, If I was going to do this again though I would setup ingress on each of the clusters and then this would slightly change the inlets configuration.
Multi-cluster setup-primary
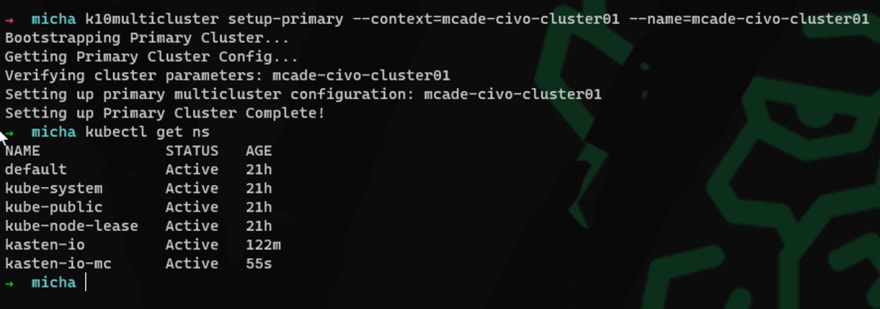
We have 3 clusters, and we need to decide our primary cluster so that we can start the configuration and bootstrap process. In this demo I have chosen the CIVO cluster located in NYC1. More about this configuration setup can be found here in the official documentation.
You will see from the commands and the images below that we are using the K10multicluster tool this is a binary available from the Kasten github page and it provides the functionality of bootstrapping your multi cluster configurations.
k10multicluster setup-primary --context=mcade-civo-cluster01 --name=mcade-civo-cluster01
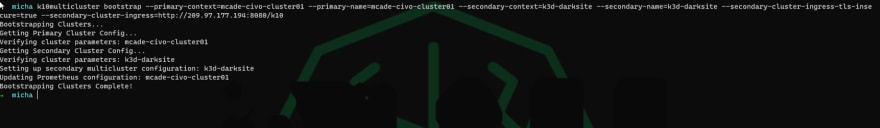
Bootstrap the secondary (dark site)
The main purpose of the demo is to prove that we can add our local K3D cluster from a data management perspective in one location.
k10multicluster bootstrap --primary-context=mcade-civo-cluster01 --primary-name=mcade-civo-cluster01 --secondary-context=k3d-darksite --secondary-name=k3d-darksite --secondary-cluster-ingress-tls-insecure=true --secondary-cluster-ingress=http://209.97.177.194:8080/k10
or
k10multicluster bootstrap \
--primary-context=mcade-civo-cluster01v \
--primary-name=mcade-civo-cluster01 \
--secondary-context=k3d-darksite \
--secondary-name=k3d-darksite \
--secondary-cluster-ingress-tls-insecure=true \
--secondary-cluster-ingress=http://209.97.177.194:8080/k10
Managing Kasten K10 multi-cluster
I will make more content going into more detail about Kasten K10 multi cluster but for the purposes of the demo, if you now login to your primary cluster web interface you will now have the multi cluster dashboard and with the above commands ran you will now see that we are managing the K3d cluster.
From here we can create global backup policies and other global configurations which also could enable the ability to move applications between your clusters easily. I think there is a lot more to cover when it comes to multi cluster and the capabilities there. The purpose of this blog was to highlight how inlets could enable not only access to the Kubernetes API but also to other services within your Kubernetes clusters.
You will have noticed in the above that I am using TLS insecure, this was due to me changing my environment throughout the demo. Inlets very much enables you to use TLS and have verification on.
Useful Resources
I mentioned in the first post that I would also share some useful posts that I used to get things up and running here. As well as a lot of help from Alex Ellis
https://blog.alexellis.io/get-private-kubectl-access-anywhere/
https://docs.inlets.dev/#/?id=for-companies-hybrid-cloud-multi-cluster-and-partner-access
https://inlets.dev/blog/2021/06/02/argocd-private-clusters.html
I have obviously used Kasten K10 and the Kubernetes API but this same process could be used for anything within side a private environment that needs to be punched out to the internet for access.



Top comments (0)