It can be challenging to monitor the EC2 instances that developers or admin teams launch. Sometimes, these launches may exceed the budget allocated to an organization. To address this, I will demonstrate how to set up automatic remediation actions using AWS Config, AWS Systems Manager and AWS Lambda. This setup ensures that only EC2 instances of type 't3.medium' are considered compliant. Any instance launched with a type other than 't3.medium' will be identified as non-compliant by AWS Config and will be immediately stopped by an automatic remediation action. This approach helps in maintaining budget control and ensuring compliance with organizational standards for resource usage.
In this case we will make custom rules with help from AWS Lambda in AWS config. Before start, this is my network topology diagram for real life testing.
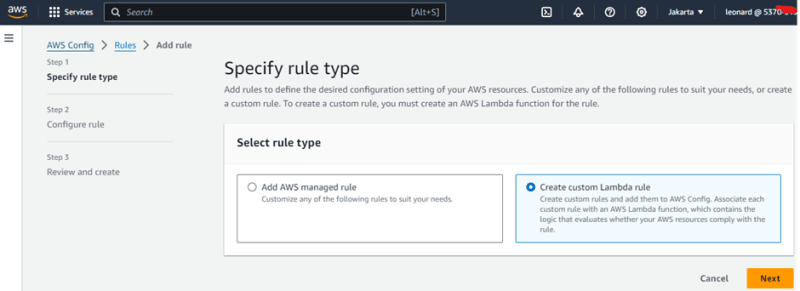
Add new rule:
I will choose custom lambda rule to make custom AWS config rule.
For lambda code,this is lambda code I configured:

AWS Config detects a change in an EC2 instance's configuration, it will triggers this Lambda function. This function evaluates the instance and reports back to AWS Config whether the instance is compliant or not.
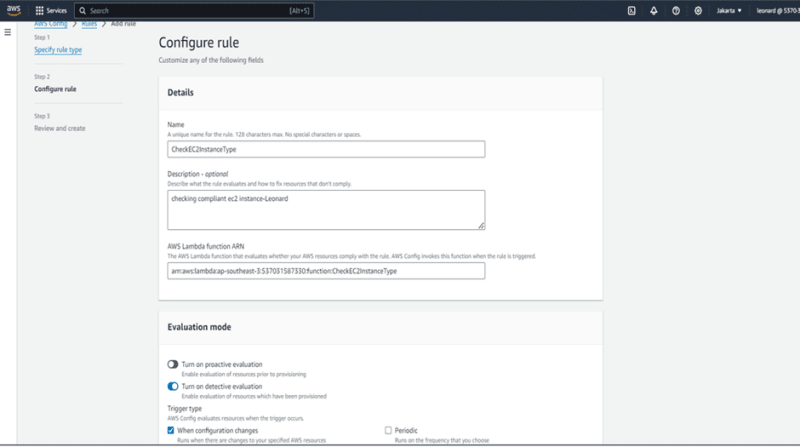
Configure the rule, and fill lambda ARN with ARN lambda we just created.
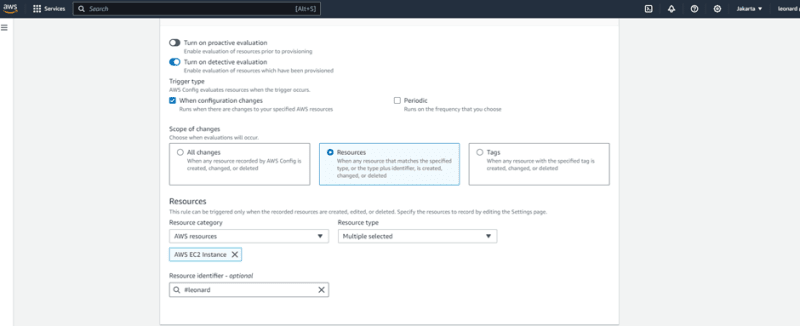
I configured trigger type with “when configuration changes” and resource= “AWS ëc2 instance”
Check review for one last time:
After creating rules, we will make remediation action IF our rule is not compliant.
We go to AWS System Manager to use Automation Document to help us with remediation automatic action.
We will use automation document named : AWS-StopEC2Instance. This is the content of automation document in SSM.
After this, we can continue setting automatic remediation action in AWS config.
AWS Config also offers manual remediation, or manual remediation with a human approval process. We can choose based on our requirements.
We can setup retries for this script to take action, I setup just 1 time. Resource id parameter I fill with InstanceID.
For remediation action, choose the document we choose at AWS System Manager.
Our rules and automatic remediation action have now been completed. It's time to test if our script and design are functioning correctly.
I am attempting to launch a noncompliant EC2 instance with the type “t3.micro”. After the EC2 instance starts and passes the status check, it won't be long before our SSM automation initiates action to stop this instance.
The EC2 instance will be stopped automatically.
Summary of aws config detail page:
Our remediation action status is “Äction executed successfully “.
Lets try it again to launch another ec2.
Only ec2 type t3.medium running well. Not comply ec2 already stopping by SSM automation action .
(Unused ec2 already terminated by me after stop)
And one of important to run these lab is IAM role and policy.
This is IAM role to make SSM run automation process to stopping ec2 that not compliant. We can change policies ”EC2fullaccess” to have more least privilege level in our production /development level.
With trust relationship to SSM.
Source to read:
















Top comments (0)