In the previous part, we saw the basics of azure signalr connections. In this part we are going to see how to secure the connection between azure signalr and web app.
Let us secure our Azure SignalR Service
Azure SignalR Security features
By the design itself Azure signalr service has a public endpoint that is accessible through the internet, and it currently does not support deploying directly into a virtual network and allowing IP address because of this you cannot leverage certain networking features with the offering's resources such as network security groups, route tables, or other network dependent appliances such as an Azure Firewall.
However, it allows you to create private endpoints to secure the traffic between resources in your virtual network and Azure SignalR Service.
You can also use Service tags and configure network security group rules to restrict inbound/outbound traffic to Azure SignalR Service.
Since in our POC we are using Azure Web app, which is internal to azure, so we are going to leverage the private endpoint to secure the internal connectivity and restricting the entire public internet access.
Default network access control(NAC) will looks like below
Here we are opening/allowing the Server and Client Connection to the open internet(entire public).The rest of connections like Rest API and Trace API will be denied by the Default Action setting
By the way the Trace / REST API are a new connection still in development phase, as of now there is no official docs from Microsoft yet
We are going to update this default setting as per our POC configurations.
Architecture Design
Securing connection between Azure SignalR and Web App
Our requirement is to connect the azure signalr from azure webapp. The Azure Web App can be accessible from internet. So, the way we need to configure the NAC will be like
-
Configure the public network rule to only allow Client Connections from the public network
-
For the Server connection we need to configure it privately using the private endpoint and allow the Server Connection from that private endpoint connection, i.e., we should not allow the Server connection from the public network
This step involves a series of other steps to be configured on azure app service as well, let us see that.
Configuring VNet
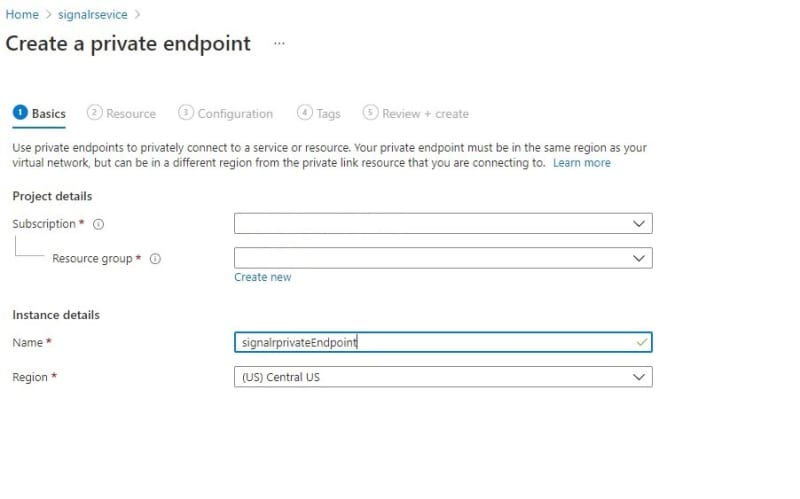
- First we need a Virtual Network (VNet), which should be in the same location as your App services and azure Signalr. In my case it would be Central US
-
vnet-cus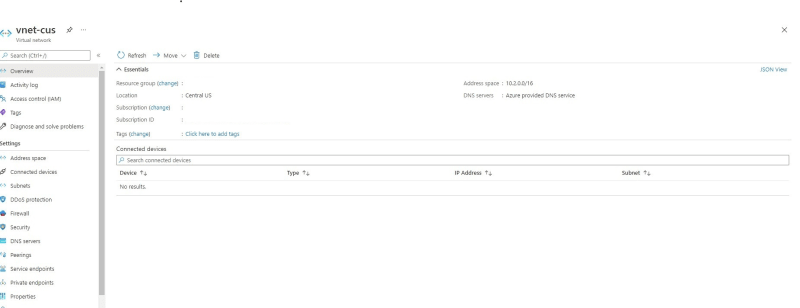
-
- Create 2 subnets inside the VNet, one for our Web App and another for Private Endpoint (azure signalr)
-
public-subnet -
private-endpoint-subnet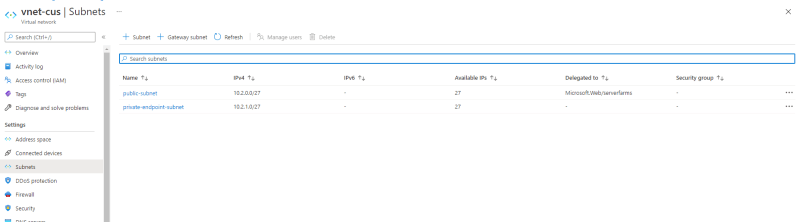
-
Integrating Azure App Service with VNet
- Configure the VNet Integration on our Web App, i.e., Integration with
vnet-cusandpublic-subnet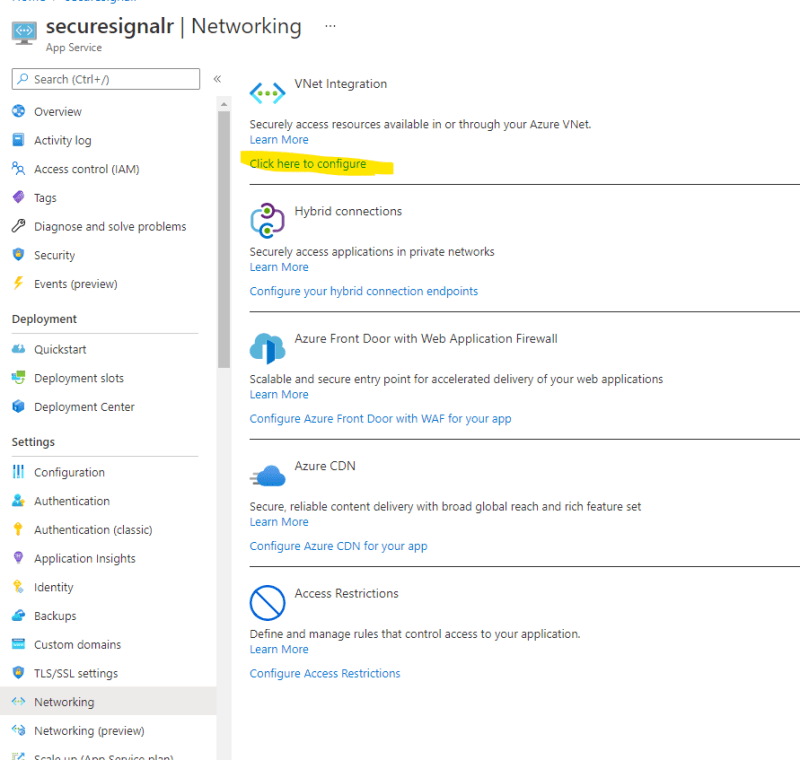
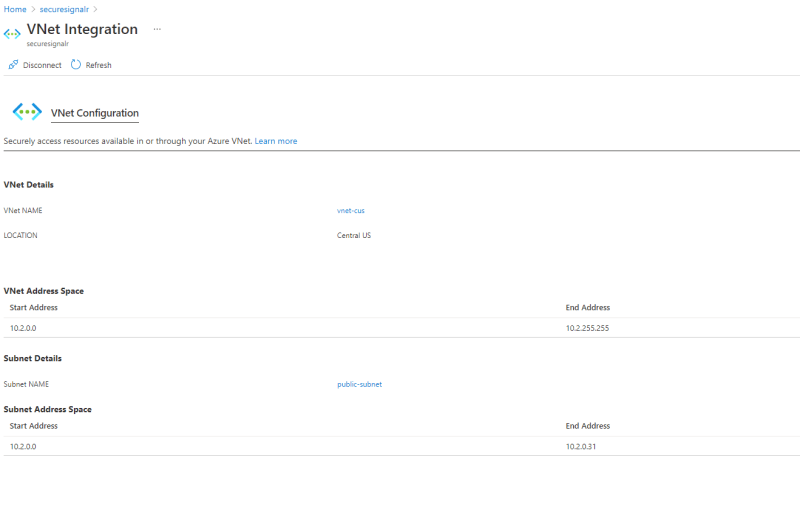
Configuring Private endpoint on Azure SignalR
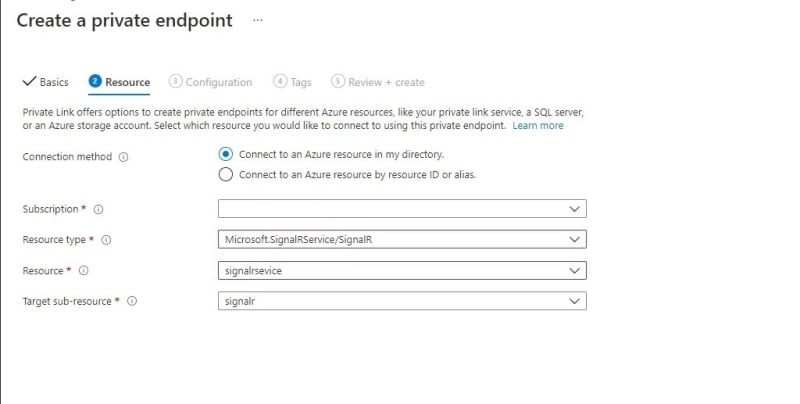
From Azure signalR menu, =>
Private endpoint connectionsand create a newPrivate Endpoint

-
Configure the Private endpoint like below
- Basic (note that the Region should be same as your VNet)
- Resource (Choose your SignalR service as your Resource)
- Configuration (choose
subnetasprivate-endpoint-subnet)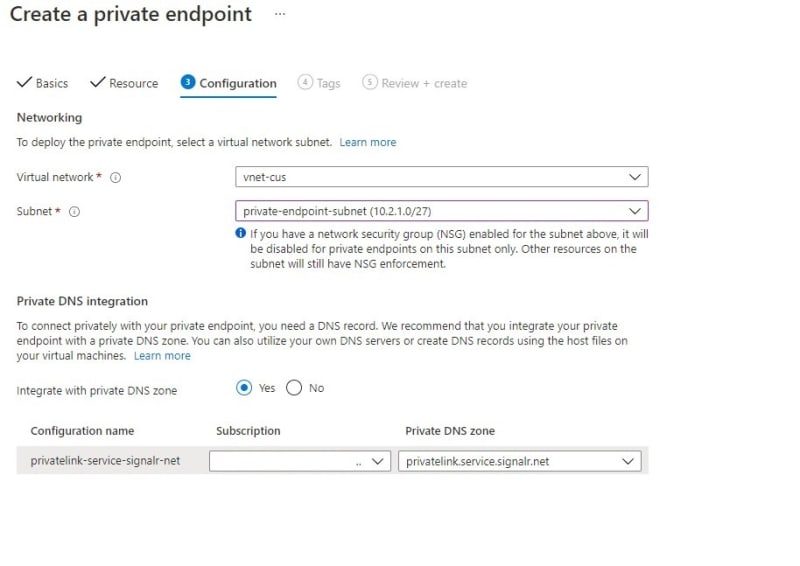
- Basic (note that the Region should be same as your VNet)
Once you created your private endpoint connection the state should be in
Approved- since I'm the actually the owner of the subscription it gets auto-approved for me, if you are not seeing approved state, please reach out to the resource owner
Configuring NAC on Azure SignalR
- As we now have an approved private endpoint connection, it is time to secure our Server connection via private endpoint
Testing
Well, that is it, we have secured the connectivity between our azure web app and azure signalr.
But WAIT? How can I make sure that my Web app is using the private endpoint and not the internet for the Azure SignalR connectivity?
I am glad you asked this question, let us find it out.
From my Azure Web App, I tried to nameresolve the azure signalr service.
> nameresolver signalrsevice.service.signalr.net
If we see the output , it is returning the private IP 10.2.1.4 of the signalr resource which confirms that connection to signalr is private and not public.
In the next part we will see the concepts related to signalr Infrastructure using terraform 💪









Top comments (5)
Thanks Jayendran, really comprehensive and details tutorial. Thanks for sharing!
I followed your steps and used the same configuration details for vnet and subnets but unfortunately at the end when I try to resolve SignalR name from App Service instance console I'm getting public IP instead of private one. I tried to ping (with tcpping) SignalrR service by private IP which I got from connected devices tab from virtual network details, but that's end up with connection time out.
Any suggestions what I may have missed or how to debug the issue?
I just deleted private endpoint and private dns zone, recreated private endpoint and .. it started to work 😑🥳
hmm. glad it worked for you atlast :)
Images are not loading properly. Can you check
Great post, but the images are still not loading. Just wondering if you're able to check please? Many thanks.