Log4j is a popular Java logging tool with a critical cybersecurity vulnerability that gained global attention in December 2021. The U.S. Dept. of Homeland Security’s Cyber Safety Review Board stated in a recent report that it is one of the most serious vulnerabilities seen in years. Because of the popularity of the Log4j tool with Java developers, the problem is an “endemic vulnerability” for the software industry, according to the board. Luckily, we can identify this security vulnerability in Java projects at no cost with the fastest and most accurate free scanner in the market, CodeSec by Contrast!
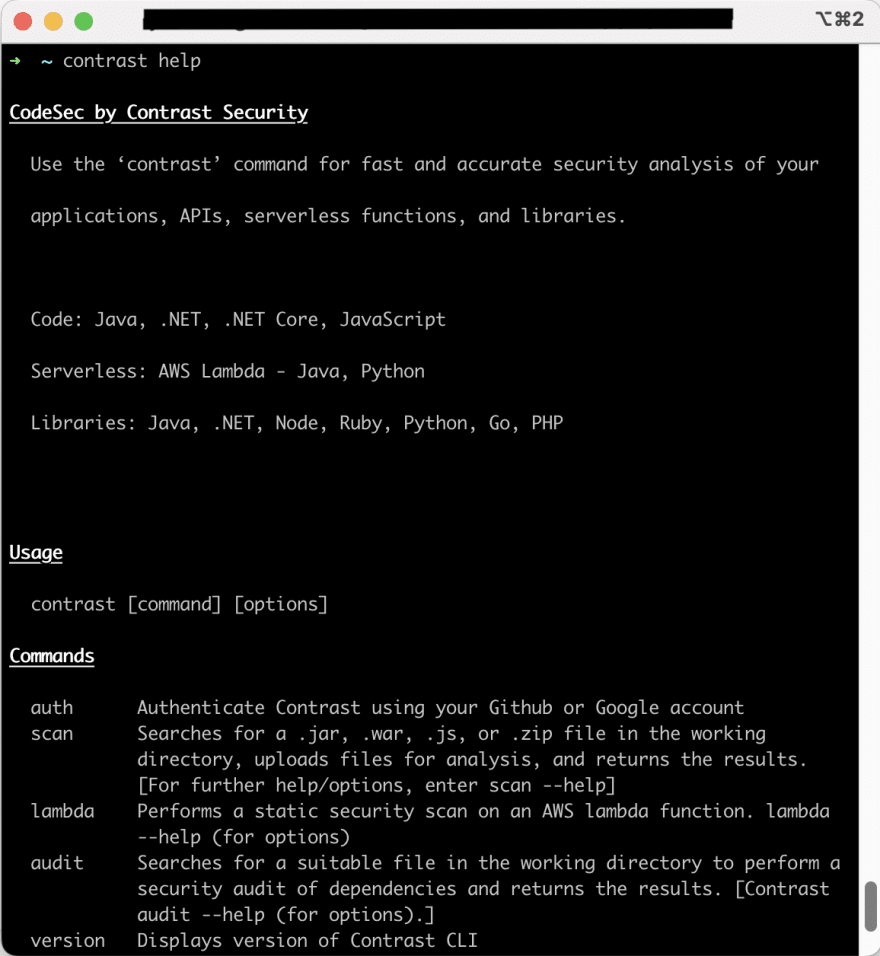
1. Get started with CodeSec
For this walkthrough, we will use both CodeSec and a demo of the Log4j exploit. The first step is to get CodeSec onto your machine. Contrast Security has great instructions on our Developer Central hub for getting started with CodeSec, but we will review the process here as well.
a. Install CodeSec
As of August 2022 Contrast Security offers three options for installing CodeSec: Homebrew for MacOS, NPM for any operating system running newer NodeJS versions and binaries through Artifactory.
For this example we will be using NPM:
Run Command: npm install -g @contrast/contrast
Pro tip: Running the command contrast help will show you the usage guide if the install has gone successfully.
b. Authenticate
Authentication is needed to access Contrast Security’s enterprise-class cybersecurity services through CodeSec. You can use your existing Github or Google account to authenticate.
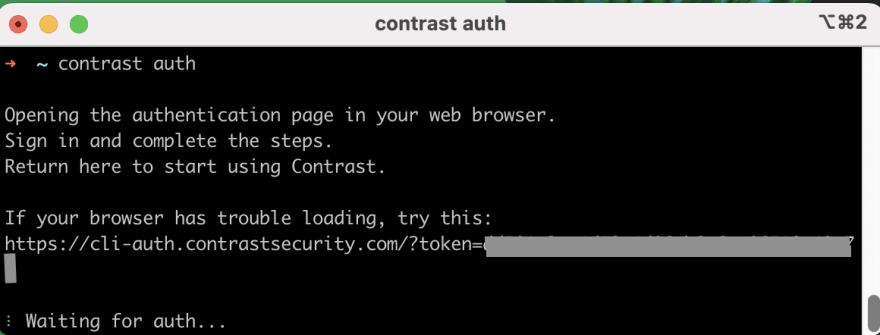
To authenticate, run the command contrast auth
A tab will then open in your browser, asking you to finalize your authentication by connecting with your existing Google or GitHub account.
*Note: * When completing the authentication steps for the first time, your command line may disconnect and output a message stating that the authentication session has timed-out. But do not worry! By re-running the command contrast auth, a new browser window will open, and this time when the initial path chosen to authenticate (GitHub or Google) is clicked, the window will immediately redirect to the Success page, and your terminal will output an “Authentication successful” line.
Now that CodeSec is set up to use locally, the next step is to get a demo of the Log4j vulnerability.
2. Log4j vulnerability
The NIST National Vulnerability Database’s page on the Log4j vulnerability has a wealth of resources about this security concern, including links to demo projects with example code implementing the vulnerability.
One linked project is the “Apache Log4j2 2.14.1 Remote Code Execution” project from Packet Storm (available here). It is a very minimalist proof of concept project that includes vulnerable versions (in this case, 2.14.1) of the Log4j libraries as Maven dependencies in the project’s pom.xml file.
Once you have the project downloaded and unzipped locally, you can check it for vulnerable third-party dependencies. In our case, we are concerned with using vulnerable versions of Log4j.
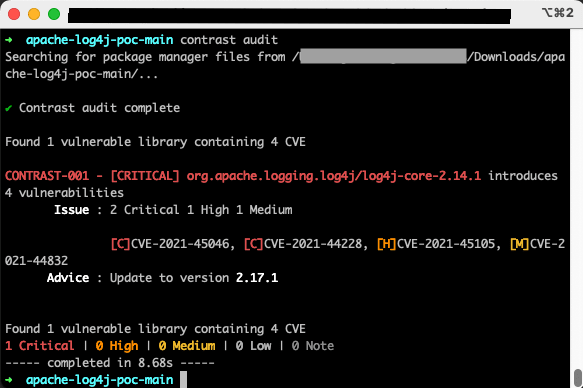
Utilize CodeSec by Contrast to secure those vulnerable libraries by running the command: contrast audit
As described, this simple command from CodeSec found the vulnerable versions of Log4j defined in our project. Additionally, it lists the specific vulnerability codes (which we could look up in the NIST NVD database for more details), and it gives advice on how to make the project more secure by upgrading the versions of Log4j used.
Contrast Security also has an entire online portal dedicated to the Log4j problem. There you can find more resources, whitepapers and information about all the other tools Contrast Security offers for handling and remediating your Log4j risks.
Conclusion
CodeSec gives developers an expert tool that handles the chores of searching Java projects for vulnerabilities while staying up to date on the latest developments in cybersecurity research. It is a highly valuable and free utility that can improve a team’s software development practices.







Top comments (2)
Hi there, we encourage authors to share their entire posts here on DEV, rather than mostly pointing to an external link. Doing so helps ensure that readers don’t have to jump around to too many different pages, and it helps focus the conversation right here in the comments section.
If you choose to do so, you also have the option to add a canonical URL directly to your post.
Hi Sloan, thanks for the comment! We will keep this in mind moving forward.
Some comments have been hidden by the post's author - find out more