According to a 2022 Stack Overflow survey of more than 50K professional developers, JavaScript is the top programming language of choice. Finding cybersecurity risks in JavaScript code is critical for developers working with modern web technologies. CodeSec by Contrast can help developers find and fix risks in their code, like cross-site scripting (XSS) or broken access control vulnerabilities.
CodeSec is Contrast Security's free developer security motion that is very easy to install with either Homebrew, npm or straight from binary. You can find CodeSec at Contrast’s Developer Central online portal.
Once CodeSec is installed on your machine and you have authenticated with either your GitHub or Google account, you can start scanning your JavaScript project for vulnerabilities with the command contrast scan. Scan will look up to three folders deep in your project for either a single *.js file to scan or a *.zip file of JavaScript files to scan. At first glance, this might seem strange, but ZIP format is just a more compact way to upload the code files that need to be examined.
In this article, we will assume that you have a modern JavaScript project with multiple code files, such as the “browser-test-bench” project in the below screenshots.
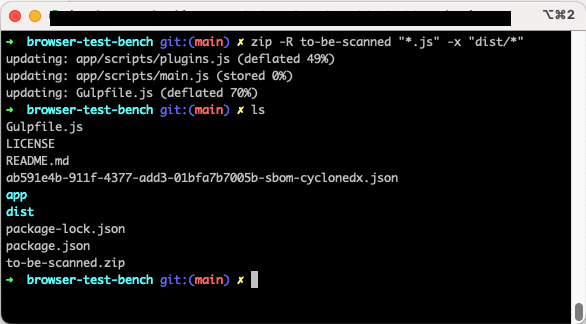
First, let’s zip the project’s JavaScript files. The zip command-line utility tool provides arguments for recursively searching through your project’s folders to find JavaScript files while also excluding certain folders, such as node_modules.
Run Command (from within your project folder):
zip -R to-be-scanned “*.js” -x “node_modules”
There are, of course, plenty of variations of this command that you could do to make the ZIP file:
- You could name it something other than “to-be-scanned.zip,” such as the day’s date or a company-specific format.
- Your project may not have a node_modules folder full of third-party libraries but may have a lib folder instead.
- Additionally, you may not want to do a recursive search through the project’s folders for JavaScript files. Instead, you might want to specify zipping only certain files instead.
Whatever your needs, the ZIP command’s man page (accessible in your terminal with the command man zip), and searching Stack Overflow are both great resources for learning about the ZIP tool’s options.
_Creating to-be-scanned.zip of project JavaScript files
_
Once the ZIP file of the project’s JavaScript files is created, you are ready to run the command to scan for vulnerabilities.
Run Command (from within your project folder): contrast scan
Contrast Security’s Scan product is a Static Analysis Security Testing (SAST) cybersecurity tool. This means that Scan examines static code files, as opposed to Contrast’s more dynamic analysis tools like Assess (an Interactive Application Security Testing [IAST] tool) and Protect (a Runtime Application Protection tool).
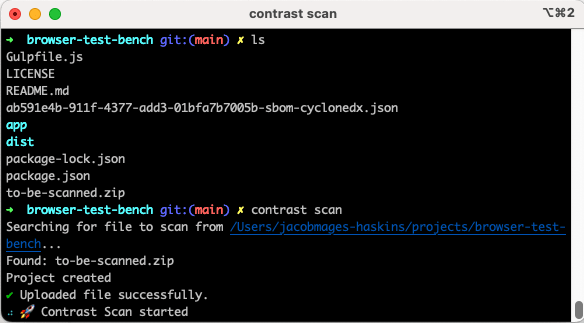
When the scan command starts, it looks for the ZIP file that we made earlier. Next, CodeSec uploads the ZIP file in order to analyze its JavaScript code files for vulnerabilities.
_In-progress cybersecurity analysis for JavaScript files
_
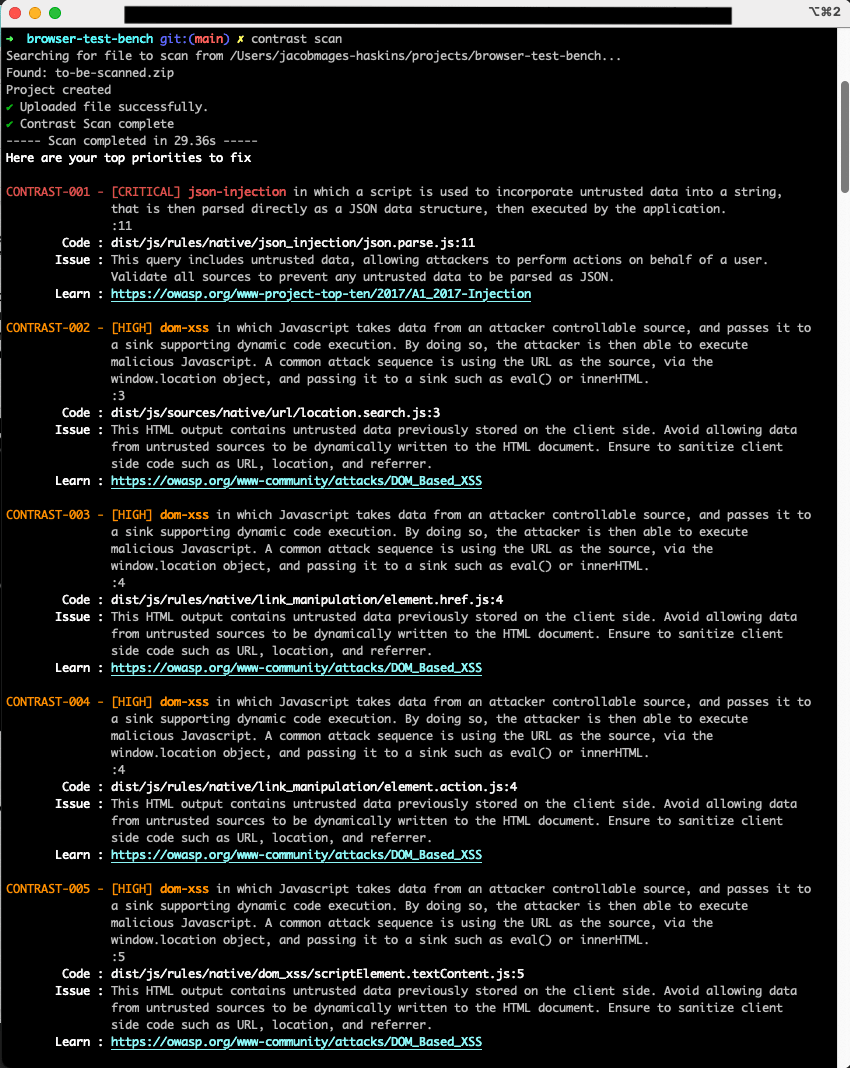
Once the Scan analysis is complete, CodeSec lists the vulnerabilities found. The vulnerabilities are sorted with the most critical-to-fix ones at the top and then descending in severity. Each vulnerability is described, has the file and line number of its occurrence listed, and provides resources for learning more about that cybersecurity risk. All of the information in the Scan analysis results can help you find and fix cybersecurity vulnerabilities before they become production-level incidents that your project’s support team needs to triage.
CodeSec’s Scan analysis results
Pro tip #1: Many modern front-end JavaScript projects minify their code for deployment in production. Minified JavaScript is not human-readable and, often, all on a single line, which means that the file and line number listing for a vulnerability in the analysis results won’t be very useful for you. Instead, try running contrast scan against your preminified code.
Pro tip #2: Because CodeSec is a command-line tool, you can incorporate Scan into your automated software processes, like we showed in our earlier article on using CodeSec with Git hooks.
Conclusion
CodeSec’s free vulnerability scanning support can help you find cybersecurity risks in your JavaScript project. CodeSec is a free way for developers to provide high-value software for this popular web technology choice.



Top comments (0)