This exploit disclosure was originally published by Chaitin Security Emergency Response Center.
Overview
Next.js is a modern web application framework developed by Vercel, based on React, and supports full-stack development. It is widely used for Server-side Rendering (SSR) and Static Site Generation (SSG). Next.js supports both traditional Node.js execution and an Edge Function mode, the latter being optimized for lightweight, high-performance service logic.
In March 2025, security researchers disclosed an authentication bypass vulnerability in Next.js (CVE-2025-29927).
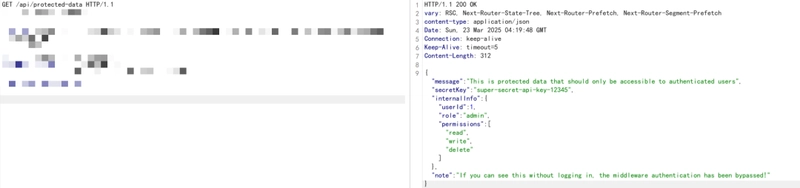
The vulnerability arises from a special request header, x-middleware-subrequest, which is intended to mark recursive middleware requests. However, this header can be forged by attackers, leading to the bypass of middleware processing chains. As a result, critical security mechanisms such as authentication and redirection that rely on middleware can be compromised.
Given the widespread adoption of Next.js, Chaitin Security researchers have confirmed that this vulnerability affects certain popular AI applications. Affected users are advised to assess their risk and apply the necessary patches immediately.
Vulnerability Description
Root Cause
Next.js does not strictly validate the source of the x-middleware-subrequest header and instead blindly trusts its value. This header was originally designed for internal subrequest management but lacks restrictions preventing external users from injecting it. Attackers can exploit this to manipulate middleware behavior.
Exploitation Conditions
- The application is built using the Next.js framework.
- Middleware contains security-related logic (e.g., authentication/authorization mechanisms), making it vulnerable to bypass.
Impact
- Authentication Bypass: Attackers can access protected resources, such as admin panels and user information APIs, without authentication.
- Security Policy Failure: Security mechanisms such as CSP settings and header injections may fail, potentially leading to XSS risks.
- Bypassing Other Security Filters: If security filtering logic is implemented in middleware, it can also be bypassed.
Severity
- Priority: High
- Vulnerability Type: Logical flaw
- Impact Level: High
- Trigger Method: Remote network exploit
- Authentication Required: None
- System Configuration Requirement: Default settings (Edge Middleware is enabled by default)
- User Interaction Required: None
- Exploit Maturity: Proof-of-Concept (PoC) available
- Fix Complexity: Low (official patches provided)
Affected Versions
- 11.1.4 ≤ Next.js ≤ 13.5.6
- 14.0.0 ≤ Next.js ≤ 14.2.24
- 15.0.0 ≤ Next.js ≤ 15.2.2
Fixed Versions
- 14.2.25
- 15.2.3
Solution
Temporary Mitigation
If an immediate upgrade is not feasible, consider the following measures:
-
Remove Malicious Headers: Strip the
x-middleware-subrequestheader from all external requests at the proxy layer. - Header Filtering: Use a CDN gateway, WAF, or other security devices to filter or block the header.
Permanent Fix
Next.js has released a security advisory and fixed versions 14.2.25 and 15.2.3. Affected users should upgrade as soon as possible.
Reproduction Steps
Timeline
- March 23 – Public disclosure of the vulnerability.
- March 23 – Chaitin Emergency Security Lab successfully reproduced the vulnerability.
- March 24 – Chaitin Security Emergency Response Center issued a security notice.



Top comments (0)