Description 📝
In Azure, a data management landing zone is a pre-configured environment that provides a secure and compliant foundation for managing large volumes of data. It is designed to meet the requirements of enterprise-grade workloads and support various data processing and analytics scenarios.
The landing zone typically includes a set of Azure services and best practices that help organizations build a data lake, a data warehouse, or a big data analytics platform in a scalable and cost-effective manner.
It also provides a framework for managing data governance, security, and compliance, while enabling self-service data access and exploration.
The key components of a data management landing zone in Azure include:
Networking infrastructure: A secure, isolated network that spans multiple availability zones to ensure high availability and fault tolerance.
Data storage and processing: A set of Azure services that support various data storage and processing scenarios.
Data integration: Tools to move and transform data between different Azure services and on-premises systems.
Security and compliance: A set of policies and controls to ensure data security, access control, and compliance with industry and regulatory standards.
Monitoring and management: A set of tools to monitor resource usage, track changes to resource configurations, and enforce compliance rules.
By using a data management landing zone, organizations can accelerate their time-to-market for data processing and analytics workloads while minimizing the risk of security breaches, compliance violations, and data loss.
Network Topology
The topology of the network that this architecture uses is hub and spoke. Both these entities are deployed in two separate virtual networks that are connected through peering. One of the advantages of this architecture is that is minimizes direct exposure of Azure resources to the public internet.
The central point of the architecture will be the Hub Network. All the connections will first come in the Hub layer and then pass to the Spoke layer. The hub will contain an Azure Firewall connected to firewall policies that will be configured based on the need of the organization, a gateway for VPN connectivity, and a Jump host where connections will pass through to Spoke.
The spoke Vnet consists of an AKS Cluster, a Mysql Flexible server and a KeyVault.
Architecture components 🏛️
Resource Groups: Two Azure Resource Groups are defined, resource-group_hub and resource-group_spoke, to organize and group the Azure resources.
Virtual Networks: Two Azure Virtual Networks, virtual_network_hub and virtual_network_spoke, are created for network isolation and segmentation.
Virtual Network Peering: A Virtual Network Peering resource, virtual_network_peering, is set up to enable connectivity between the two virtual networks.
Subnets: Multiple Azure Subnets are defined within the virtual networks:
subnet_firewall in the virtual_network_hub.
subnet_jumphost in the virtual_network_hub.
subnet_vpn in the virtual_network_hub.
subnet_pe in the virtual_network_spoke.
subnet_cluster in the virtual_network_spoke.
subnet_ag (Application Gateway Subnet) in the virtual_network_spoke.
subnet_database in the virtual_network_spoke, which also includes a delegation to a MySQL flexible server.
Azure Firewall: An Azure Firewall resource, firewall, is provisioned with a specific configuration in the resource-group_hub.
Public IPs: Two Azure Public IP resources, public_ip_app and public_ip_vpn, are created for use with the firewall and VPN gateway, respectively.
Firewall Policy: An Azure Firewall Policy, firewall_policy, is created and associated with the firewall.
Firewall Policy Rule Collection Group: A rule collection group, firewall_policy_rule_collection_group, is defined under the firewall policy.
Virtual Network Gateway: A Virtual Network Gateway, virtual_network_gateway, is configured for VPN connectivity.
Linux Virtual Machine: A Linux Virtual Machine, linux_virtual_machine, is set up, presumably for administration or testing purposes.
Network Interface: A Network Interface, network_interface, is provisioned for the Linux VM.
Application Gateway: An Azure Application Gateway, application_gateway, is configured in the resource-group_spoke.
MySQL Flexible Server: An Azure MySQL Flexible Server, mysql_flexible_server, is provisioned for database services.
Private DNS Zone: A Private DNS Zone, private_dns_zone, is created for MySQL server.
Private DNS Zone Virtual Network Link: A link, private_dns_zone_virtual_network_link, is established between the DNS zone and the virtual network.
Kubernetes Cluster: An Azure Kubernetes Service (AKS) Cluster, kubernetes_cluster, is deployed in the resource-group_spoke.
Key Vault: An Azure Key Vault, key_vault, is set up for secure storage of keys, secrets, and certificates.
Private Endpoint: A Private Endpoint, private_endpoint, is created for secure and private access to the Key Vault.
How to use the architecture
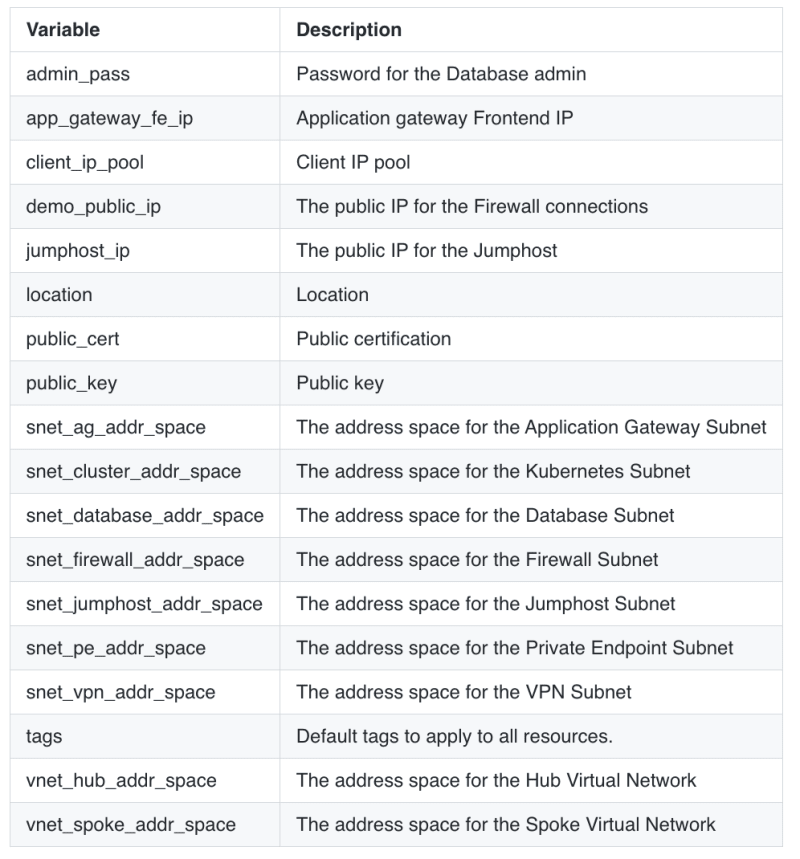
Go to the templates and clone the architecture. Modify the following variables according to your needs:
Use this architecture here 👉 https://app.brainboard.co



Top comments (0)