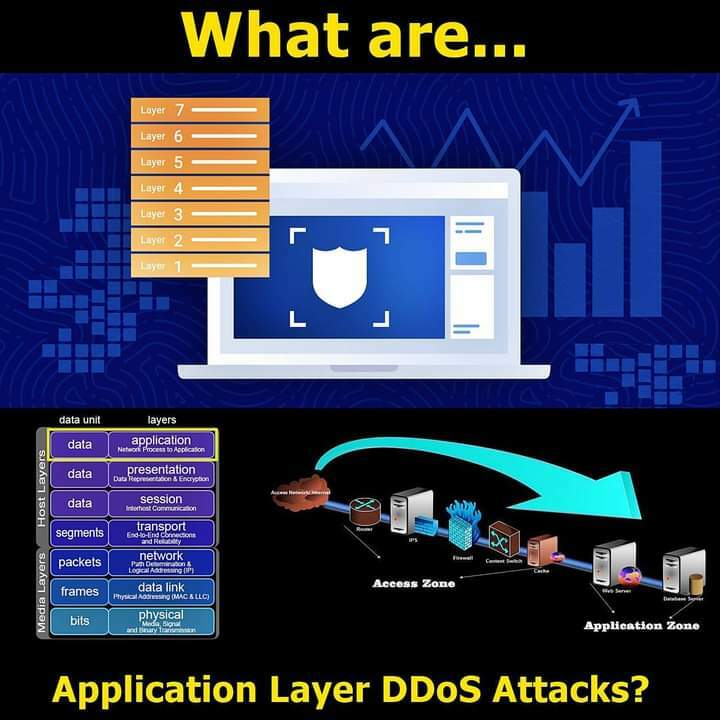
What are Application Layer DDoS Attacks?
The basis for this attack often targets applications like Web Servers (i.e., Windows IIS, Apache, etc…); however, application layer attacks have been evolving to application platforms like WordPress, Joomla, Drupal, Magento, and others.
The goal of application layer attacks is to take out an application, an online service, or a website.
These attacks are usually smaller than the ones we have seen before. Nevertheless, the consequence of an application layer attack can be nefarious, since they can go unnoticed until it is too late to react. That is why they are called “low and slow attacks” or even “slow-rate attacks”.
They can be silent and small, especially when compared to network-layer attacks, but they can be just as disruptive.
For example, a small VPS on Linode, Digital Ocean or AWS (Amazon) can easily handle a 100,000 to 200,000 packets per second SYN flood. However, the same server running on a WordPress or Joomla CMS can barely break 500 HTTP requests per second without shutting down. That is why application layer attacks can cause as much damage as a network application attack.
When you think about the amplification effect, even one HTTP request (which an attacker can perform without spending much money or resources) can cause a server to execute a large number of internal requests and load numerous files to create the page.
IMPORTANT NOTE:
These attacks are also harder to detect than network-layer attacks. Because when application layer attacks start, they look very similar to legitimate requests from users and can escalate.
The reason for that is that these attacks focus on the web application layer, which generally includes:
✔ Hitting the web server
✔ Running PHP scripts and
✔ Contacting the database just to load one web page.
Application-layer attacks (mostly known as Layer 7 attacks) can be part of attacks which not only target the application, but also the bandwidth and network.
One of the reasons why these attacks are on the rise is that they tend to be less expensive to implement by malicious actors. On an application-layer attack, the amplification is CPU, memory or resource based, not network based.
Most DDoS attacks today originate from a hacker-controlled botnet of vulnerable IoT devices. This includes internet connected security cameras, household appliances, smart TVs, home lighting systems, and even refrigerators.
The exponential growth of DDoS attacks is mostly due to the total lack of regulatory control over IoT devices, which makes them excellent recruits for the botnets. A hijacked group of IoT devices with unique IP addresses can be redirected to make malicious requests against websites, causing a DDoS attack.
Your devices, such as home Wi-Fi routers also, can be compromised and act as a botnet for DDoS attacks.
Guys, what do you think of this post about Layer-7 DDoS attacks?
Kindly leave me your thoughts in the comment section.
With thanks,
Hafiz Muhammad Attaullah
attaullahshafiq10@gmail.com







Top comments (0)