Cloud workloads continue to grow as new digital innovations arise monthly in the worlds of IoT applications, cloud services, and big data analytics. However, the cloud's dynamic and often complex nature can make cloud application security challenging. This gap in cloud security readiness is a growing concern for organizations worldwide, with CISOs feeling the pressure.
61% of CISOs feel unequipped to cope with a targeted attack, and 68% expect such an attack within the following year. The question is not whether your organization may face a security threat but whether you're prepared to resolve it on time before disaster strikes.
What is Cloud Application Security?
Cloud application security involves measures and technologies that protect cloud-based systems, data, and infrastructures from cyberattacks, unauthorized access, and other threats. Essential for any organization leveraging cloud services, this security domain is more important than ever due to our increasing reliance on cloud infrastructure to store sensitive data. Key technologies include encryption, IAM management, and advanced intrusion detection systems.
Top Cloud Application Security Threats
1. Distributed Denial of Service (DDoS) Attacks
DDoS attacks overwhelm cloud resources with excessive traffic, aiming to disrupt service availability. They exploit the scalable nature of cloud services, leading to substantial bandwidth and resource consumption.
How to avoid a DDoS attack
- Employ DDoS mitigation tools with advanced network traffic analysis and adaptive thresholding like Cloudflare to identify and divert malicious traffic.
Leverage redundant network architecture and scalable cloud resources to absorb the impact of attacks.
Regularly conduct stress tests on your infrastructure to simulate DDoS scenarios and spot gaps.
2. Insecure APIs
Cloud services extensively use APIs to flow data between applications and cloud services. APIs are the gateway of the system to the outside world. When not adequately protected, they become a soft target for hackers. The root of vulnerabilities often traces back to weak authentication, lack of encryption, and uncontrolled access permissions.
How to avoid insecure APIs
Use API Discovery tools to comprehensively view all APIs in your cloud environment, including shadow APIs that are not adequately documented.
Implement robust authentication and authorization measures, such as OAuth and API gateways that control access.
Encrypt data in transit through SSL/TLS and conduct regular security assessments of all APIs.
Regularly schedule pentest sessions or implement automated pentest tools such as ZAP.
3. Cloud Infrastructure Misconfigurations
Security misconfiguration vulnerabilities in cloud settings are a leading cause of breaches and can impact cloud application security in many ways. For example, when access controls are not correctly set, default credentials remain, or security features are disabled. Considering the constant changes being made to cloud infrastructure, it's easy for simple errors to result in high-severity vulnerabilities -- such as forgetting to close an S3 bucket in a Terraform file.
How to avoid cloud infrastructure misconfigurations
Automate cloud configurations through Infrastructure as Code (IaC) to maintain consistent security postures.
Conduct config audits regularly to scan your IaC for security vulnerabilities.
Employ cloud security posture management (CSPM) tools to detect and rectify misconfigurations on time.
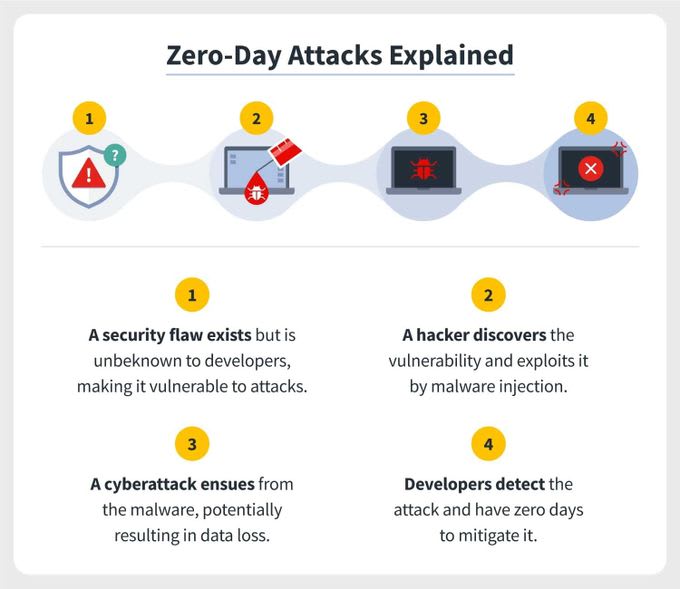
4. Zero-Day Exploits
Zero-day exploits target unknown or unpatched vulnerabilities in software or hardware. Attackers exploit these vulnerabilities before developers can release fixes, making them particularly dangerous.
How to avoid zero-day exploits
- Keep software up-to-date.
- Deploy intrusion detection and prevention systems (IDPS) that use behavior analysis and heuristics to identify abnormal activities. These abnormal activities can be indicative of a zero-day exploit.
5. Insider Threats
Insider threats arise from individuals within the organization who misuse their access to cloud resources, intentionally or unintentionally exposing sensitive data. Such threats are challenging to detect as they bypass external security measures.
How to avoid insider threats
Enforce strict access controls and the principle of least privilege to minimize risk.
Emply User and entity behavior analytics (UEBA) can help detect anomalies indicative of insider threats.
Implement regular security awareness training to prevent accidental exposures.
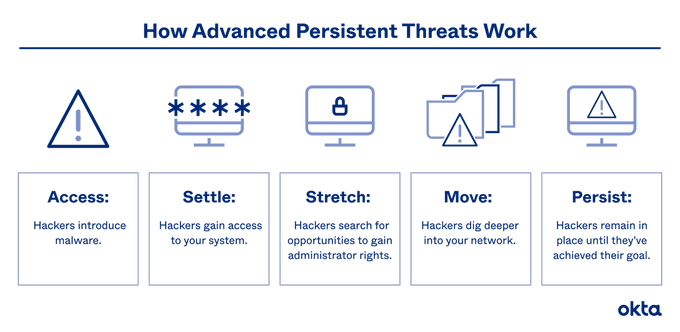
6. Advanced Persistent Threats (APTs)
APTs are sophisticated, prolonged campaigns where attackers gain unauthorized access to your network and remain undetected for extended periods. They often target cloud environments to steal data or monitor activity.
How to avoid Advanced Persistent Threats (APTs)
- Implement endpoint protection, encryption, network segmentation, and continuous network traffic monitoring for signs of unusual activity.
- Threat intelligence services can provide insights into emerging threats and actor tactics, techniques, and procedures (TTPs).
7. Injection Attacks
Injection attacks exploit vulnerabilities in the application's input-processing mechanisms. Attackers manipulate user inputs to access data or execute arbitrary commands to exploit your app further and compromise your network.
How to avoid injection attacks
Implement input validation and sanitize user inputs.
Ensure strict access controls via the principle of least privilege.
Regularly update and patch software components.
7 Best Practices to Secure Your Cloud Applications
Aside from the guidance we provided above to mitigate specific cloud threats, these are some crucial security practices you should look to implement:
1. Container Security Controls
To secure containerized applications, consider implementing controls across the container lifecycle, including image scanning for vulnerabilities, enforcing runtime security policies, and utilizing tools like Kubernetes native controls or third-party solutions like Trivy.
2. Strengthen API Security
Familiarize yourself with the OWASP API Security Top 10, a comprehensive guide to mitigating the most critical API vulnerabilities. Add further protection for your API gateways with Apigee or Kong. These tools offer features like rate limiting, IP filtering, and caching to protect against common API threats and analytics for monitoring your API usage patterns. You should also do regular pentesting with automated tools like ZAP or use a third-party company offering pentest services.
3. Encryption and Key Management
Automate the rotation of encryption keys at predefined intervals using solutions like AWS Key Management Services (KMS) or Hashicorp Vault. AWS KMS can integrate with other AWS services like S3, EBS, or RDS -- making key management more cohesive. You can also use AWS Secrets Manager CLI to store sensitive information safely in the cloud.
4. Threat Detection and Hunting
Machine learning and AI-driven tools can transform your approach to threat detection. Tools like Splunk or Elastic Security will hunt down potential threats and automatically send alerts if any usual activity occurs within your cloud environment. Configure these tools to alert security teams about possible threats and automate the initial incident response actions.
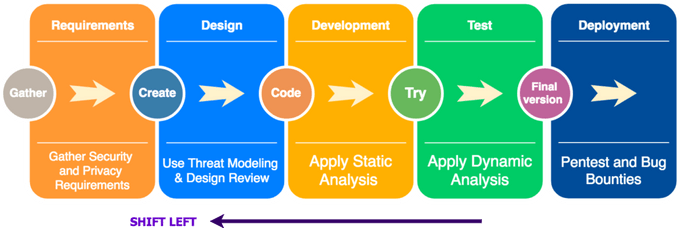
5. DevSecOps Automation
Integrate security practices directly into your CI/CD pipeline to ensure security considerations are addressed automatically and early in development. This way, DevSecOps can minimize vulnerabilities without slowing the development process.
Jit integrates seamlessly into GitHub and uses a Security as Code (SaC) approach to enable your team to define and automate its security policies. Through its automated security, Jit vets all code changes within pull requests before being merged, facilitating early detection and remediation.
Consolidate cloud application security controls like SAST, SCA, secrets detection, CSPM, IaC security, DAST, and more into one platform.
6. Cloud Infrastructure Misconfiguration Scanning
Establish continuous monitoring to detect vulnerabilities in your cloud infrastructure. Utilize tools like Jit for ongoing security posture assessment.
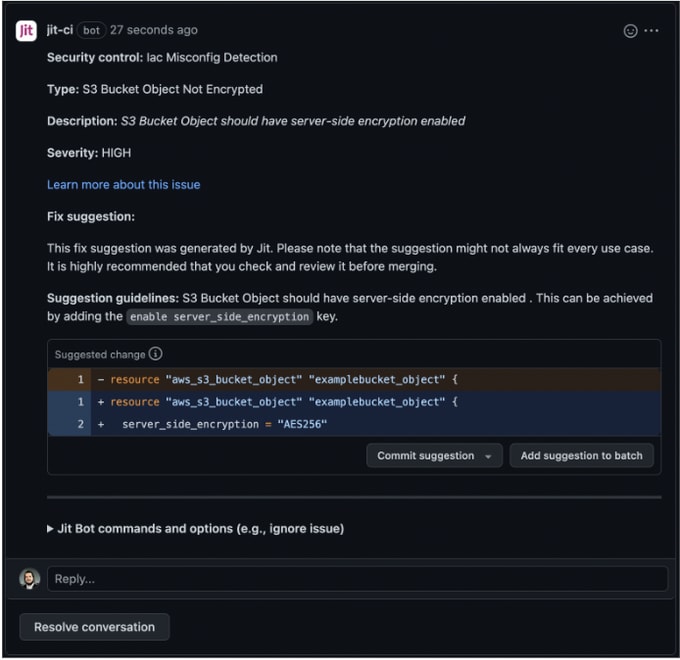
Jit scans your infrastructure-as-code (IaC) to surface vulnerabilities and provides auto-remediation for over 200 types of misconfigurations, which significantly reduces the time to respond to risks. The platform also scans the actual cloud infrastructure wherever it is deployed to ensure no drifts between the IAC and the actual deployment, effectively closing the loop in the cloud infrastructure scanning. The automated remediation suggestions under pull request comments provide clear instructions on mitigation.
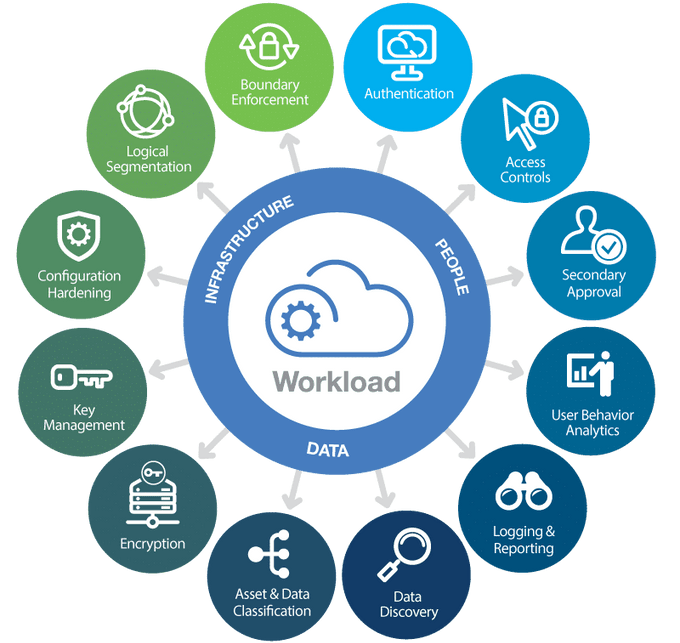
7. Zero-Trust Architecture
Embrace a zero-trust security model that operates under the premise that trust is never assumed -- for entities within or external to the network. Enforce strict access controls and micro-segmentation to minimize lateral movement within your cloud system.
Software-defined perimeter (SDP) or identity-aware proxies can also help establish a zero-trust environment, ensuring users and devices are authenticated and authorized before accessing cloud resources.
Securing the Cloud Horizon
The cyber threat landscape is constantly shifting, and cybercriminals have found the clouds of many organizations to be ripe for the taking. Establishing a robust, end-to-end security strategy for your cloud environment has never been more critical. Incorporating the cloud best practices we've covered is a great starting point to protect against the most common cloud application security threats.
As a platform designed to empower your DevSecOps initiatives, Jit automates security controls for your development environment by integrating directly into GitHub. Don't let your organization be an easy target. Explore Jit today.






Top comments (0)