When I got started with AWS, after creating an EC2 instance, I was given keys with instructions on how to log in from my local machine, and I was amazed at how everything worked. In this writeup, we will see how you can get your servers (web, email, files, database etc) running on your local system using Virtual Machines (VMs) and how you can create users, assign permissions and enforce SSH key-based authentication the same as found on AWS.
SSH key-based authentications are proven to be more secure and easy to use. They offer convenience as a user is not required to remember passwords to login. Let's configure. Okay, let's see how they work.
Step 1: Install and configure Virtual Box and Vagrant for your platform. Confirm that it is correctly installed by running vagrant -v.
Step 2: If you do not have one already, create a VMS directory for keeping all your boxes. Inside the VMS directory, create a sub-directory and initialize an Ubuntu VM in the directory using this command
mkdir keybased-auth && cd keybased-auth && vagrant init ubuntu/trusty64.
This should create a Vagrantfile in the directory. You can open the Vagrantfile and customized the IP address, size and ports depending on the server you are building. In the Vagrantfile, look for this line
# config.vm.network "forwarded_port", guest: 80, host: 8080, host_ip: "127.0.0.1"
and uncomment it by removing the preceding #. This will simply allow us to be able to access our server on port 8080 from our system.
Step 3: Now it's time to bring up our box. Run the command vagrant up and wait for the machine to download and install Ubuntu 14 OS on the machine. If all went well, you should have your VM up and running. Confirm that by running vagrant status, it should show running.
Step 4: Log in to the VM and update packages. Let's log into the machine by typing vagrant ssh. This should log the default user vagrant into the machine. Your terminal should read something like this vagrant@vagrant-ubuntu-trusty-64:~$.
We can now update our packages by running sudo apt-get update && sudo apt-get upgrade.
Step 5: Now we will create a new user, assign permissions and log in with the new user. Using the currently logged in vagrant user, type sudo adduser <username> substituting <username> to any name you want your new user to bear, in my case, tvpeter. This will create a new user
and group tvpeter, add the user to the group and creates the users home directory. Next, you will be prompted to set the users password, full name, room number, home phone, and others. You can choose to leave it blank by hitting the return key successively.
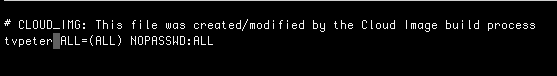
At this point, our new user can log into the system but does not have permission to run administrative commands. Let's rectify that by adding the user to the subdoers group. Run the command sudo cp /etc/sudoers.d/vagrant /etc/sudoers.d/tvpeter to make a copy of the user vagrant's permissions as tvpeter in the sudoers.d directory. Let's modify the file using nano. Type sudo nano /etc/sudoers.d/tvpeter to open the file. On the second line, change vagrant to tvpeter (same as shown below), save ^o and exit the file ^x.
Next, log out the vagrant user by typing exit and log in with our new user by typing ssh tvpeter@127.0.0.1 -p 2222 or ssh <newUsername>@<privateIPAddress> -p 22 if you used a private IP address. Supply the password set for the user when prompted.
Step 6: Generating login keys and connecting our new user: As we stated in the introductory part of the writeup, using SSH key-based authentication improves server security and makes it easy to log into without having to remember passwords.
From your local system, run ssh-keygen and supply a file name to save the generated keys. This will generate two files with the supplied name one ending with .pub and saved in the .ssh subdirectory of your home directory /users/<username>/.ssh/. In my case, I used keyauth.
View the content of the file that ends with .pub using cat /users/<username>/.ssh/<fileName.pub>.
Back to where our new user is logged in on the server, we will create a new directory and a file in the directory. Run the command cd && mkdir .ssh && touch .ssh/authorized_keys to create authorized_keys file. Open the file using sudo nano .ssh/authorized_keys and copy the content from /users/<username>/.ssh/<fileName.pub> and paste in the authorized_keys file on the server.
Next, we will restrict other users from having access to the user's .ssh directory and authorized_keys file. Run the command chmod 700 .ssh and chmod 644 .ssh/authorized_keys. We are all done setting our keys. Type exit to log the user out. Next, we will re-login using the ssh keys.
Step 7: Login user using ssh keys and disable password-based logins: Having configured our server to use ssh keys to login, we will login with the user and disable logins into the server using passwords. login using the command ssh <username>@<ipAddress> -p 2222 -i ~/.ssh/<localKeyName> or -p 22 for private IP address, which in my case will be ssh tvpeter@127.0.0.1 -p 2222 ~/.ssh/keyauth.
Next, we will disable logins using passwords. Open the sshd_config file with nano using the command sudo nano /etc/ssh/sshd_config and search for PasswordAuthentication yes, change the yes to no (as seen below) and restart ssh service using sudo service ssh restart.
Your server is now configured to use only SSH Key-based authentication. You can then proceed to set up your setup as web, email, database or whatever purpose bearing in mind it is now more secure.
Your comments/observations are welcome. Thanks for reading.



Top comments (0)