As everyday I go to bus station and use Busmap HaNoi(you can download on appstore and chplay, if you travel Ha Noi in Viet Nam and want to journey by bus) to check bus time comming.I will pick up 2 or 3 bus route to my company.
I have used SSH for remote my job but I can not explain detail information How it work. I am surfacing internet and as a post on dev.to, it is a detail explanation. So I want to note on my page:
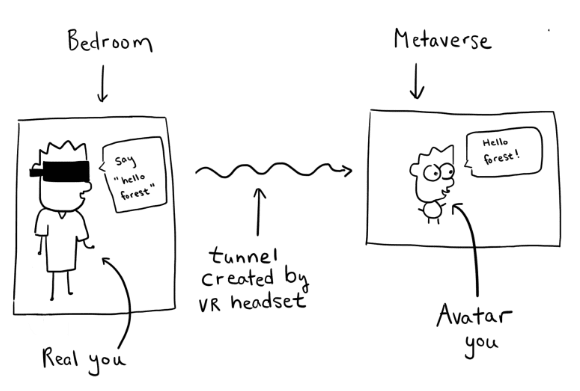
In real life, this is what the analogy translates to:
You == developer.
Your bedroom == your laptop, or whatever local machine you're typing on.
The Metaverse == a remote machine/server you are trying to access from your local machine.
The VR headset == the SSH tunnel that allows you to access the remote machine (Metaverse) from your local machine (bedroom).
Login screen == the SSH key pair that ensures only authorized parties can use the SSH tunnel. I'll explain this more thoroughly in a later section of this blog.

In layman's terms, SSH is like a secure, secret tunnel that lets you connect to another computer over the internet. It helps you do things on that computer as if you were sitting right in front of it.
Why do I need to use SSH?
a: Deploying Code
IBM BPM
I always use to deploy snapshoot on IBM BPM
Network:
I use to configure the network equipment
b: Updating a server configuration
other: config IoT gateway.....
*It was better for 2 main reasons.
*
Encrypting data
Let's say that part of the data being transmitted from my machine to a remote machine is the string "username: jesswang password: ?IamC00l!". Without encryption (so with older protocols like Telnet or FTP), a hacker would be able to read that string as you just read it. With encryption, the data they get back might look like "H23kLs*^!d8%PwZx0KsL!9B#N%u@i8". In reality, the encrypted data would be a different sequence of bytes that adheres to encrypted algorithmic standards (that I don't know much about), but this is just to give you an idea.
Authentication
Older programs like Telnet relied solely on password-based authentication. When you connect to a remote system using Telnet, the Telnet server prompts you to enter a username and password to login. However, Telnet transmits your passwords in plaintext, making it easy for hackers to read. SSH primarily uses a different (and better) approach called public-key authentication. I'll explain how it works below so you can understand how your information is better protected from hackers.
Source:https://dev.to/therubberduckiee/explaining-ssh-to-my-uber-driver-38a







Top comments (0)