“Can you imagine proving to someone your identity without providing any proofs?”. Sounds crazy & impossible, right? Right? NO! This is indeed the future we are going to step into!
Most applications around us use some form of authentication technique. The most prevalent authentication mechanism is password-based authentication. In this mechanism, the identity prover (user) gives a password, which is subsequently validated by the identity verifier (the server). If the authentication is successful, the user is allowed access to execute specified operations. Otherwise, the user is denied access to the services.
Password-based authentication has been around for decades and has proven to be effective. However, there is an inherent problem with this method: Password Theft. No matter how securely the verifier and prover hold the password, an eavesdropper can always get the password while the verifier and prover converse for authentication!
Can we improve this flaw of password-based authentication? Apparently, YES!
The issue here is that the password must be sent over an unprotected channel. We can fix this problem if the prover can somehow demonstrate to the verifier that it has the right password without sending it over the unprotected channel.
But, how can we achieve this? Zero-Knowledge Password Proofs (ZKPP) is the answer!
Secure Remote Password (SRP) Protocol
The Secure Remote Password (SRP) protocol, created by Tom Wu in 1998, is a cryptographic mechanism that provides a zero-knowledge proof-of-knowledge. It allows a client to demonstrate knowledge of a password or any other data without exposing what that data is!
There are a number of advantages that SRP offers -
- The server never need to know the password of a client.
- Replay attacks are not possible.
- SRP provides perfect forward secrecy. The shared secret derived is different each time, and no private keys are needed that could be stolen.
- Even if the server is hacked and the password verifiers are stolen, an attacker can’t use the verifiers to authenticate as a client without an expensive brute force search.
Let us now understand the protocol at high level…
Two Step Protocol
There are two phases to the SRP protocol — the Setup/Registration phase, and the Authentication phase.
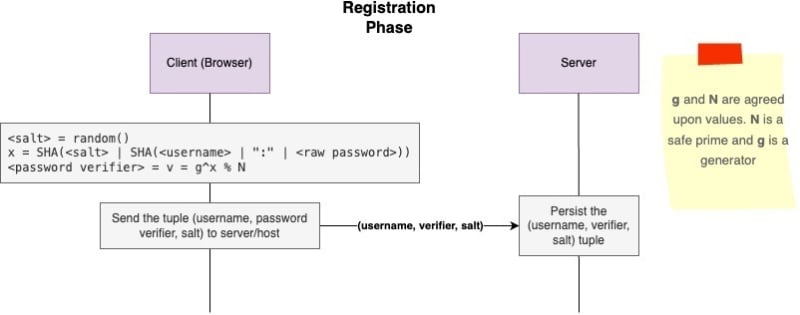
Setup/Registration Phase : The Setup/Registration phase has to be performed once for each client before actual authentication. In this phase, the client chooses a password and calculate a verifier, which it sends to the server. The verifier is not password equivalent, like a hash, and thus it cannot be used for authentication even if compromised.
This verifier would be used in the authentication phase to actually authenticate the client.
The diagram below summarises the algorithm in more technical details.
Authentication Phase : This is the phase where actual authentication takes place. To authenticate, the client send its username to the server. The server responds with the salt recorded against that username. If the password is correct, the SRP protocol derives a strong shared secret between the client and the server through a process similar to a Diffie-Helmann key exchange.
This process, in technical depth, is described in the image below.
SRP Implementations
It takes meticulous attention to detail and a solid grasp of the underlying cryptographic principles to implement the SRP protocol. Nonetheless, a number of frameworks and tools are available to make the process simpler. Here I list some of them -
With this we reach the end of this blog. If you reached till here, congratulations!
Hope you enjoyed this article. Follow for more interesting article on tech!








Top comments (0)