products versions - {webMethods Developer Portal 10.11 & above}
Introduction
In this tutorial, we are going to see how we can secure the elastic search shipped along with the Developer portal installation.
Pre-requisite
Install Developer Portal version 10.11 or higher.
Steps to follow
Create tmp folder
[sv@daeapiportal08rh Install]$ mkdir es
[sv@daeapiportal08rh Install]$ cd es/
Create instance yaml file
Create a file with following details (Note: node here refer the machine name)
[sv@daeapiportal08rh es]$ vi instance.yml
instances:
- name: ‘daeapiportal08rh’
dns: [‘daeapiportal08rh.eur.ad.sag’]
Generate CA and server certificates
Navigate to the elastic search folder (e.g : ES location /InternalDataStore/) run the following command
[sv@daeapiportal08rh InternalDataStore]$ bin/elasticsearch-certutil cert --keep-ca-key --pem --in ~/Install/es/instance.yml --out ~/Install/es/certs.zip
Unzip the certificates & copy to ES folder
Unzip the certificates using the following command
Create a folder inside ES folder & copy the certificates to it
[sv@daeapiportal08rh config]$ mkdir certs
[sv@daeapiportal08rh config]$ cp ~/Install/es/certs/ca/* ~/Install/es/certs/daeapiportal08rh/* certs/
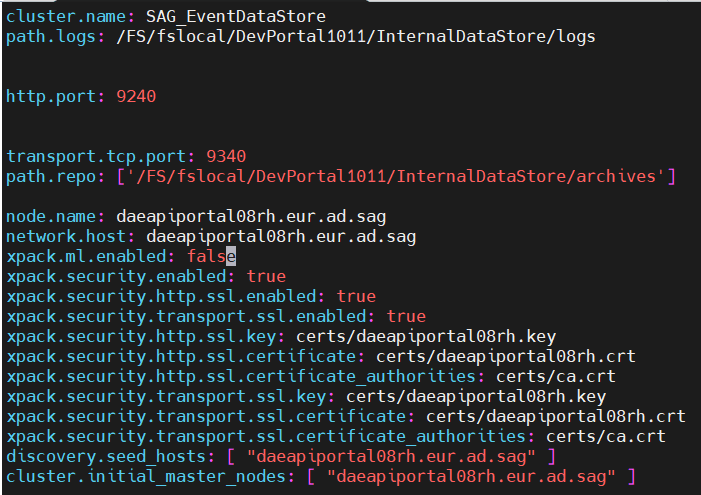
Configure elasticsearch.yml
Add the following lines to your elasticsearch.yml file and remove the duplicate entries
node.name: daeapiportal08.eur.ad.sag
network.host: daeapiportal08.eur.ad.sag
xpack.ml.enabled: false
xpack.security.enabled: true
xpack.security.http.ssl.enabled: true
xpack.security.transport.ssl.enabled: true
xpack.security.http.ssl.key: certs/daeapiportal08.key
xpack.security.http.ssl.certificate: certs/daeapiportal08.crt
xpack.security.http.ssl.certificate_authorities: certs/ca.crt
xpack.security.transport.ssl.key: certs/daeapiportal08.key
xpack.security.transport.ssl.certificate: certs/daeapiportal08.crt
xpack.security.transport.ssl.certificate_authorities: certs/ca.crt
discovery.seed_hosts: ["daeapiportal08.eur.ad.sag"]
cluster.initial_master_nodes: ["daeapiportal08.eur.ad.sag"]
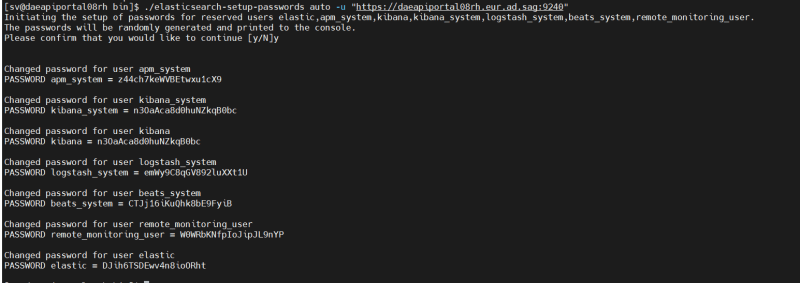
Start & Set built-in user password
[sv@daeapiportal08rh bin]$ ./startup.sh
Run the following command once the ES is started, secure the password somewhere we will need it later.
./elasticsearch-setup-passwords auto -u "https://daeapiportal08rh.eur.ad.sag:9240"
Access _cat/nodes API via HTTPS
curl --cacert ~/Install/es/certs/ca/ca.crt -u elastic 'https://daeapiportal08rh.eur.ad.sag:9240/_cat/nodes?v'
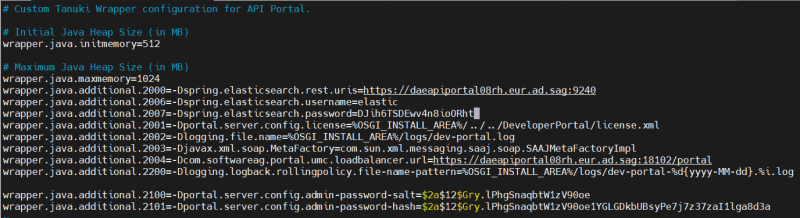
Add the elastic search https url & Basic Auth details in Developer portal config file
Add the following details in the config(/profiles/CTP/configuration/dpo_wrapper.conf) file
wrapper.java.additional.2000=-Dspring.elasticsearch.uris=https://daeapiportal08rh.eur.ad.sag:9240
wrapper.java.additional.2006=-Dspring.elasticsearch.username=elastic
wrapper.java.additional.2007=-Dspring.elasticsearch.password=m8XnkjtqoyOLVgnU9qU5
Once the file is saved, restart the CTP server(/profiles/CTP/bin).
Now you should able to access the Developer Portal UI without any issue.
Useful links | Relevant resources
Configuring SSL, TLS, and HTTPS to secure Elasticsearch, Kibana, Beats, and Logstash | Elastic Blog








Top comments (0)