A computer connects to the Internet using an IP address assigned by ISP (internet service provider). This IP address handles outgoing requests and incoming traffic.
A proxy acts as another computer sending and receiving requests on a user’s behalf. Users connect to the Internet, forward traffic to a web server through a proxy (masking the real IP address), and receive a response also through a proxy.
An HTTP proxy acts the same way as any other type of Internet-facing proxy: it routes requests coming from a user on the network, filters incoming traffic, blocks any anomalies, and supports data caching, thereby lessening the bandwidth.
What is HTTP Proxy?
Without a widely adopted protocol — an HTTP — we would not have been able to send audios, videos, images, and other files over the Internet. An HTTP allows one to send requests and communicate with web servers.
A user can access the Internet directly. An HTTP proxy, however, acting as a mediator between a user and a web server, communicates with websites on users’ behalf, thus maintaining users’ anonymity as a security precaution, granting access to restricted content, accelerating caching files, and more. As you might remember there are both free or paid proxies.
What’s the Difference between HTTP Proxy and HTTPS Proxy?
An HTTP proxy is a server that sits in front of another computer and forwards requests for data from one location to another. This means that all traffic coming into a user’s network passes through a proxy first.
HTTPS is also used for transferring data over a network. The difference between an HTTP and HTTPS proxy is that HTTPS proxies encrypt the connection between a user and a proxy server.
The main benefit of using HTTPS proxy is to protect users from man-in-the-middle attacks. While HTTP has no built-in security features, HTTPS provides encryption to secure communications between browsers and servers. This means that all data sent between the browser and server is encrypted, which makes it harder for hackers to intercept the information.
How Does HTTP Proxy Work?
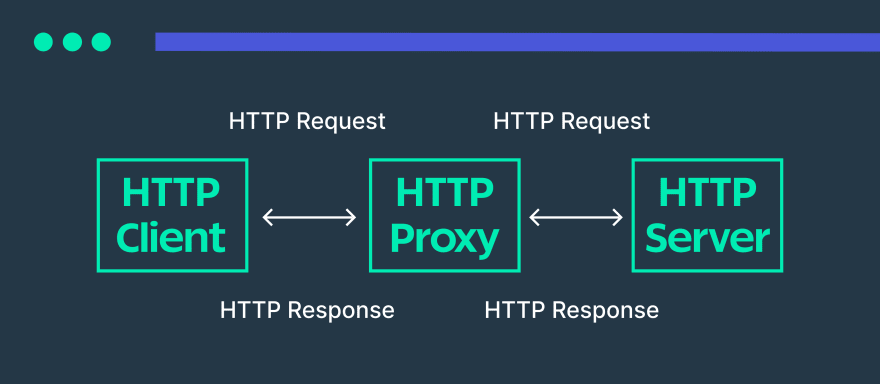
An HTTP Proxy serves both as an HTTP-Client and as HTTP-Server performing security, management, and caching functions. Simply speaking an HTTP proxy is a gateway that transfers files over the internet, establishing the communication between a user and a web server.
A user makes a request to a web server. Instead of accessing the server directly, the request is reached first by an HTTP proxy, which masks the true IP address before sending the outcoming request to the target web server. Acting as an HTTP-Client a proxy protects a user’s computer or an office network by filtering traffic: it allows only authorized requests to reach their destination. Concurrently, acting as an HTTP-server, a proxy analyzes the incoming traffic and blocks any suspicious packets with malware that can delete files from a web server or infect it with viruses.
The Use of HTTP Proxy
The main reason to use an HTTP proxy is to protect users’ data by hiding the true IP address and depersonalizing browser activity.
An HTTP proxy also works as a tunnel that connects to the Internet network devices with restricted access.
- Keep connections anonymous
As mentioned earlier HTTP proxies are used to reroute traffic through a proxy hiding the true user’s IP address. So the target website sees only a proxy’s IP and forwards to it query results. The true IP and the identifying information are concealed.
- Filter content
An HTTP proxy filters and analyzes traffic that reaches it. It checks if the data configuration satisfies the initial request, examines for any malice, spyware, or other security dropouts, and stops the non-authorized files to be downloaded on a computer.
- Enhance security
An HTTP can examine HTTP/S headers verifying traffic sources. A header is a part of a data packet containing information about content, its length, and other characteristics. Acting as a firewall an HTTP proxy protects a user’s computer. An HTTP proxy also examines data packets for any abnormalities that go against security/access policies. This feature is useful for large companies because it allows them to add an extra layer of security. Setting up between the local network and a public webserver an HTTP proxy block attempts to store unauthorized files.
HTTP Proxy Advantages
An HTTP proxy is recommended for several reasons:
to bypass content restrictions in the local network (based on the source domain, pathname, file name, or URL extension);
to bypass websites’ security protocols, geo-blocks, and access policies whether at school or at work;
to enable simultaneous access to the same connection for a few users thereby enhancing the connection speed;
to save the bandwidth by caching files, thus reducing the workload on a web server.
Acting as a gateway between a user and a source server, an HTTP proxy compresses and caches the most frequent requests on a proxy server. The result is lower traffic, better speed, browsing performance, and user experience.
However, as an HTTP proxy does not encrypt traffic coming in and out, data caching can lead to information abuse. In case the cache is hacked sensitive data, login credentials and passes can be used for illegal activities.
An HTTP proxy enables a user to connect to the internet in a more reliable way. We use an HTTP proxy when we want our browser to request a source from another computer. An HTTP proxy acts as an intermediary between a computer and the remote host, providing a higher level of anonymity.
The most common use for an HTTP proxy is to filter unauthorized incoming traffic and block access to websites protecting a network device from malware, spam, or other unwanted content.
An HTTP proxy can help to get around website content restrictions such as firewalls. This is exactly the way you can use proxy for web scraping and web crawling tasks.
An HTTP proxy allows lessening bandwidth by utilizing caching function. When addressing the website that a user has already visited, an HTTP proxy sends the response from the cache instead of routing it to the Internet thus making a network device or a browser run faster and more efficiently.
This post was originally published on SOAX blog.




Top comments (0)