It is a lovely summer afternoon. Emilia, an online Italian language tutor, decided to work from a cafe. Trying to save a few quid, she logs on to the free Wi-Fi available. Before she could access the service, a login page popped up asking her to register or accept some terms and conditions which we often ignore. That right there happened because of a transparent proxy.
So what is a Transparent Proxy?
A transparent proxy is a proxy that serves as an intermedial agent between a client’s computer and the internet. It intercepts the outbound information on a network before it reaches the internet. It can also be called a forced proxy, inline proxy, or intercepting proxy.
This proxy is termed “transparent” because it carries out its function of redirecting clients’ requests and responses without any modification in contrast to a non-transparent proxy. Since only a server configuration is required, they remain undetected on a network by leaving clients’ computer proxy settings intact.
How Does a Transparent Proxy Work?
In using a transparent proxy, the traffic is usually redirected into a proxy at the network layer, without altering the computer’s configuration. For example, Emilia, after registering on the Wi-Fi, might request to continue reading an article she started at home on soax.com. However, without her knowledge, the article is delivered not from soax.com server, but rather from a transparent proxy running on the public network. Although her experience is exactly the same, her activity can now be monitored.
Setting up a transparent proxy requires two new components. The first is a redirection mechanism that reroutes a TCP connection meant for a server on the internet to a listening proxy server. This usually takes a form of a firewall on the same host as the proxy server. When a redirected connection is received by the proxy, it sees a plain HTTP request that lacks host specificity.
Now the second component comes to play. It is a host module that queries the first component for the original destination of the TCP connection.
What are the Main Transparent Proxy Settings?
Interception
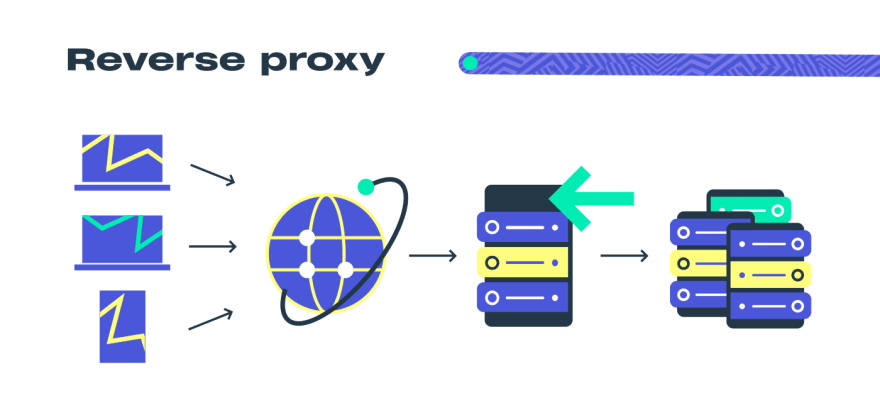
a transparent proxy should intercept traffic, at the operating system level or at the router levelReverse proxy
a proxy can be placed after a web server to increase performance for clients It receives initial HTTP connection requests like the actual endpoint.
Authentication
provides the server with the same credentials as the users behind the proxyCaching
determines if the proxy servers should store webpages for returning usersData Streaming
configures proxy to provide restricted access to certain protocols or ports
Examples of Transparent Proxies’ Uses:
Modifying or Blocking Network Traffic by Gateway Proxies
Proxy servers often carry client requests through a firewall. The firewall allows the transmission of traffic between an internal network and the internet. The traffic however can be blocked if it goes against certain rules that have been set.
- Preventing Access to Certain Websites by Filtering Proxies You can use a transparent proxy to filter out undesired content as defined via the data streaming proxy settings. If Emilia requests a specific website at the cafe, let’s say a torrent site that had been blacklisted, the proxy can refrain from forwarding the request to the web server while it intercepts the connection and displays an error page to her.
- Creation of Copies of Data that is Stored on the Server by Proxy Caches It serves as an optimizer for slow internet speed by increasing efficiency in low bandwidths through caching. The proxy server creates copies of the data and stores them on the server to serve them as a cache to subsequent users. This reduces the strain on the web service by having the proxy provide the content instead of the service itself.
These servers are often employed to optimize low bandwidths or to filter contents
Advantages and Disadvantages of Transparent Proxies
Advantages:
- A transparent proxy provides higher bandwidth and reduces transmission latency thus, improving the quality of the service.
- No configuration is needed on the user’s network or computer settings.
- It allows businesses to selectively deny access to their network services. In addition, before users are permitted to use the internet, confirmation of identity and a term and condition agreement is required.
- A user’s web browsing quality is improved through the frequent use of cache, and they can easily add websites that they want to visit to a favorite’s list that usually takes a long time to be loaded due to congestion in the network.
- Websites can be protected against DDoS attacks and can up the efficiency of servers used for streaming videos.
- It shapes the way users connect to the internet and simply adds functionality to the internet provider without adding inconvenience.
Disadvantages:
- If poorly configured, the redirection and caching of web traffic may cause problems with the internet connection, especially when there is a need for authentication to connect to the internet.
- User traffic is being intercepted and can be tampered with.
- There is a risk of user data or information breach It keeps all your information: the proxy server stores user details which might raise privacy concerns.
Users do not have control over transparent proxies as they are forced on them. This is a disadvantage to users who are not comfortable with caching and would want to avoid it.
There are both benefits and risks associated with the use of transparent proxies. Usually, advantages outweigh possible risks; however, it all depends on the situation. Ultimately, transparent proxies serve data faster through caching and effectively filter out unwanted information, providing organizations with good control over their networks with minimal interference, which makes them a great tool to consider.
Originally published on SOAX proxies blog





Top comments (0)