A proxy is an all-in-one tool used by anyone from individuals and small companies to large businesses. It helps to extract data from websites, prevent an IP from getting blocked while scraping, protect a computer from malware, balance traffic, etc. With such a versatile functionality there must be different IP types.
What are Proxy Servers?
A proxy server (or a proxy) is a mediator between the device connecting to the Internet and a targeted website. A proxy masks the user’s IP address, thus hiding their identity.
How a proxy server works
When a user makes a request it goes to a proxy server. The proxy checks if the data configuration satisfies the initial request, analyzes traffic for any malice, and sends the retrieved data back to the user. No target website sees the user’s real IP.
Why do we use Proxy Servers?
A proxy serves different purposes. It provides an extra level of security by filtering the traffic and an extra level of anonymity for a user by masking the true IP address and the user’s physical location.
A proxy also improves load balance, compresses and caches files to make devices run faster and more efficiently.
Also, a proxy allows avoiding captchas, bypassing geo and firewall restrictions.
Price aggregation, SEO monitoring, data scraping, etc. would be much harder without a proxy.
What are the Main Types of Proxy Servers?
Based on Price
Before we delve into the technical details of proxy types we need to define if you either pay for your proxies or use them for free.
Free
You do not pay for free proxies. However, you do not know who is behind the open proxy server. Hackers collect everything from credit card details and passwords to social media and bank accounts, so your private information is in danger when you use free proxies.Paid
There is no other option to avoid any security issues than to pay for proxy services. Moreover, a reliable proxy provider offers you 24/7 account support.
Also, paid proxies provide better speed, uptime ratio, and overall performance.
Based on Service
These proxy types are based on proxy exclusivity.
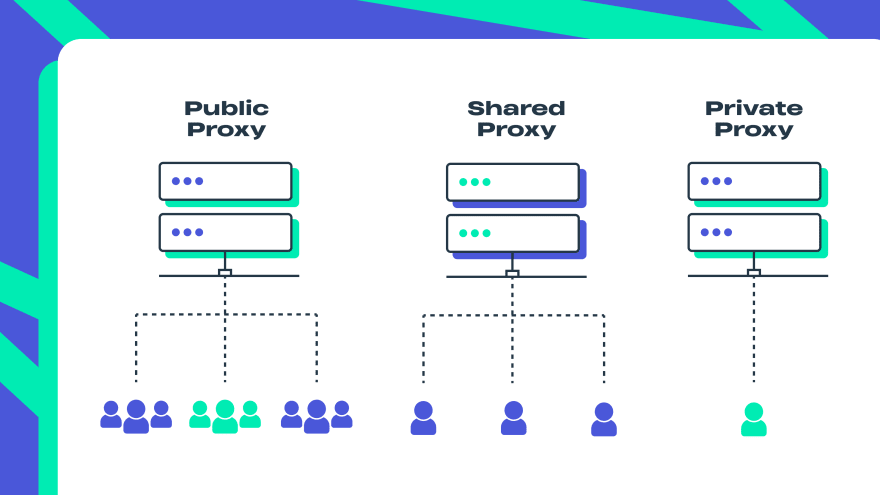
Public
A public proxy is open for everyone. It is usually easy to set up. The biggest disadvantage however is its vulnerability. A public proxy is risky and speed is usually slow due to it being used by multiple users at a time. There is also no guarantee that you will have access to the target content by using it, as such proxies are often banned on popular websites due to their high activity.
It is also almost impossible who the owner of these proxies is and chances are pretty high that some public proxies are out there just to gather you personal information for further illegal activity.Shared
A shared proxy is used by several people at a given time but the number of users is limited unlike in public proxies. Through sharing costs with other users these proxies are more affordable; however, the performance might be subpar due to multiple sessions at a time. As the same IP is shared between several users simultaneously some search engines might trigger captcha messages more often than you would prefer.Private (dedicated)
A private proxy is used by a single client at a time, so this proxy is more reliable, fast, and secure. The best thing about a private proxy is its high speed. A private proxy hides your true IP address and geolocation, so you can have access to the geo restricted content while keeping your personal data safe. You can surf, stream, scrape, search and download as much as you want. Also, you will never experience the bad neighborhood effect. But such exclusivity comes at a price. A private proxy performs the best and costs the most.
Based on Location
A proxy placed in the internal network separates two subnetworks, whereas a proxy placed between the public and internal network, separates a user and the global network. This leads to two types of proxies.
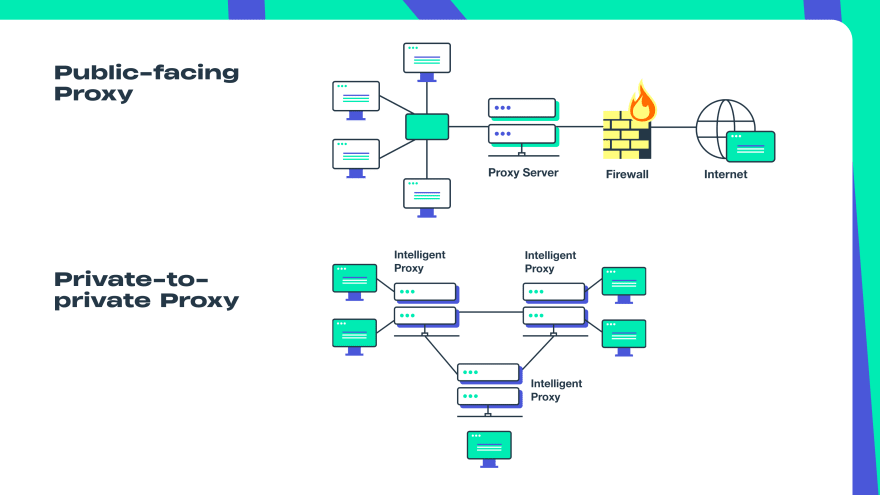
Public-facing Proxy
A public-facing proxy is located between the internal network and the web servers on the Internet. It filters both incoming and outgoing traffic and retrieves data from a specific source. It also controls access to the backend server on a private network for its protection.Private-to-private Proxy
Private-to-private proxy improves security in complex internal college and university networks. It improves networks’ security and limits websites that users can access.
Based on Protocol
There are four main types of proxy based on a protocol they use to set up the connection.
FTP Proxy Server
An FTP proxy handles FTP traffic. It is used to intercept and render files from one computer to another on a corporate network. It controls access to the websites and ensures no malicious files are downloaded.SSL (HTTPS) Proxy Server
An SSL proxy encrypts the inbound or outbound traffic, so neither a user nor the web server detects the proxy presence.
An SSL proxy encrypts all connections. These can not be intercepted and even if it happens the hacker would have no chance to read the information.HTTP Proxy Server
An HTTP proxy is compatible with many websites. That is why it is popular.
The weak point is that an HTTP proxy does not encrypt requests, so be careful with your private information using this type of proxy.SOCKS proxy
SOCKS is a protocol that sends data through a firewall without reading and encrypting it. A SOCKS proxy does not filter the traffic in any way.
It is mostly used for video calls and streaming, torrenting, gaming, and traffic-extensive scraping.
Based on Rotation
Whether you need to change an IP with every new request or not you choose between static or rotating proxies.
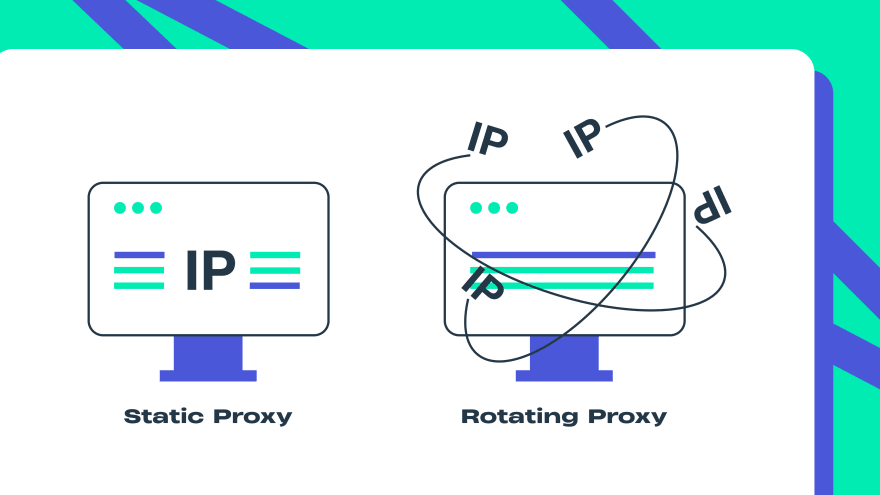
Static Proxy
A static proxy never changes and it works the best when you want to keep the same identity for an extended period of time, e.g. for managing social media accounts. As static proxies do not change very frequently you easily avoid suspension and blocks and get fewer requests for account verification and authorization.Rotating Proxy
A rotating proxy swaps your current IP to another so you never use the same IP more than once. A rotating proxy changes an IP address with every log-in and log-out session or after some time, usually 1-30 minutes making it difficult for websites to detect suspicious activity from a device and to block an IP.
Based on Traffic Flow
This type of proxy determines the relationship between the user and the server. It’s either a user or a server who benefits from a proxy service.
Forward Proxy
A forward proxy determines the relationship between a client and the external web. It is used by a client to bypass firewall restrictions to visit websites that are blocked in a specific country.Reverse Proxy
A reverse proxy controls access to the server on a private network. It prevents users from having direct access to sensitive data stored on a server. A reverse proxy also balances traffic load by spreading requests between several backend servers on the intranet.
Based on Versions of the IP address
Proxies are characterized by the IP version they use. There are two types of IP addresses:
IPv4
IPv4 for quite some time was the only existing IP protocol. IPv4 is a 32 bit address, so once humanity started to use a lot of devices that need a network connection (those are not only laptops or mobile phones, but household appliances like smart TVs or security systems as well), IPv4 variations started to run out quickly. In 2015 it was announced that IPv4 protocols were in shortage and IPv6 was introduced.
IPv4 is supported by all websites and apps. To work with them you need to have an IPv4 proxy.IPv6
IPv6 is the newest generation of IP addresses. IPv6 is a 128 bit address, which allows much more variations and chances are they won’t run out as quickly as IPv4 addresses.
IPv6 proxies are considered to be more versatile and easy to work with. They cost several times lower than IPv4 and you can buy the whole subnets of data center IPs.
Based on Anonymity Level
The basic function of a proxy is to make a user anonymous. Based on this, proxies can be anonymous or transparent.
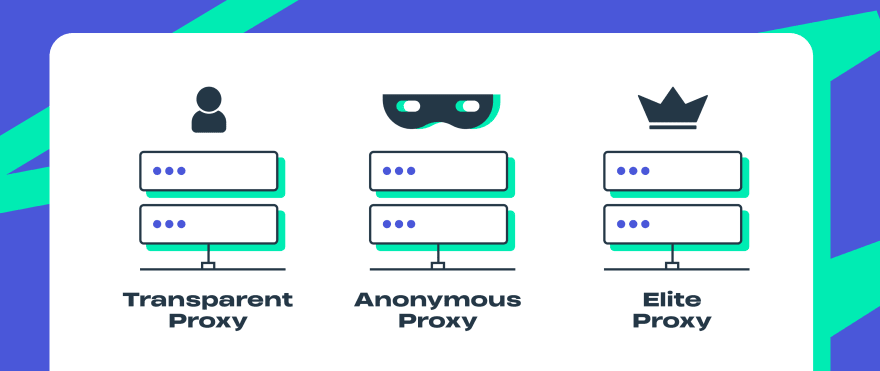
Transparent Proxy
A transparent proxy gives you no privacy protection at all. Many companies use them to route traffic and control which websites their employees can address and which cannot. Schools and libraries enable their users with access to paid digital services or block access to websites with disturbing content using transparent proxies.Anonymous proxy
An anonymous or a semi-transparent proxy does not reveal the true IP. Although it informs the target service that you use a proxy. In case you do not want to see the targeted ads or you hide your location an anonymous proxy is your choice. A semi-transparent proxy is not fully secure. If you want to be completely safe go for an elite proxy.High-Anonymity Proxy (Elite)
An elite proxy is the most secure one. It neither passes any information about a user nor identifies itself as a proxy. They mask themselves as real users. If you want to stay completely untraceable this is the best option.
Based on Versions of IP reuse
Virgin proxy
A virgin proxy has not been previously used. It is almost impossible to find a virgin IPv4 proxy. Most of IPv4s were recycled. However, there are billions of virgin IPv6 data center proxies. They are not associated with any account, or illegal activities and have no history.Used proxy
All IPv4s proxies have been used in the past and have their history because their number is finite. Residential proxies are the ones rented by real users, so they are used by default.
Based on IP Source
The traditional way to obtain an IP is through a data center. As proxy services evolved the residential and mobile proxies appeared.
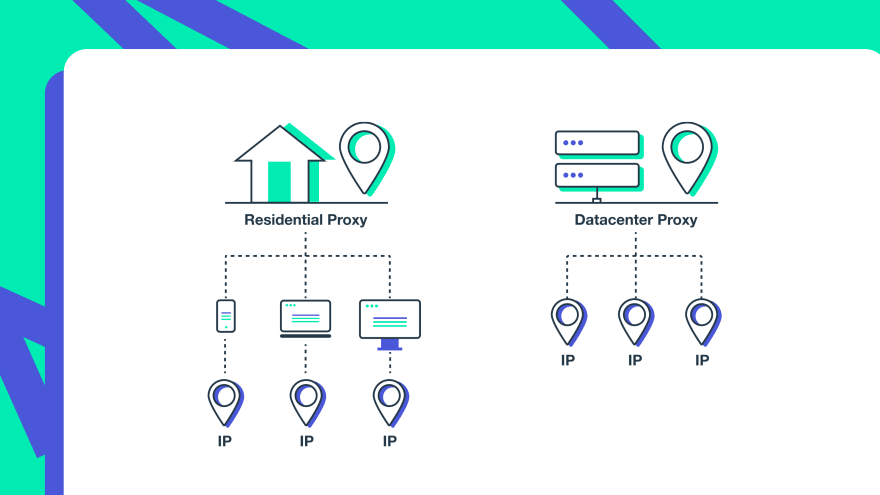
Data Center Proxy
A data center proxy is created artificially by a computer and is not attached to a real device. The biggest advantage of a DC proxy is its speed and low price. One cloud server hosts hundreds of DC proxies and they share similar IP addresses. A DC proxy is used primarily for web scraping on less regulated websites.Residential Proxy
A residential proxy belongs to real mobile and desktop devices. It mimics real people and that is why it is rarely getting blocked. A residential proxy is the best proxy for most tasks, but it is not cheap.Mobile Proxy
Mobile proxies are allocated to portable mobile gadgets by mobile operators and are used by real users. These proxies are hard to track and block because operators share the same IP address among hundreds of people. So they produce real user traffic and that is why they are the most expensive.
Based on Presentation
You can get proxies either in the form of extended IP lists or getaway addresses.
Proxy lists
In a proxy list, you can see all features the proxy obtains. These lists (usually HTML files) can be copied and pasted into web scraping or SEO tools.Backconnect proxy
A backconnect proxy opens for you a gateway to a pool of IP addresses. So you use multiple IPs through one address without managing them manually. The backend server rotates IPs by itself. You do not pay for a proxy package, you pay for bandwidth. So the price for backconnect proxies is higher.
Conclusion
Proxies are not so simple as they might seem at a first glance, one might even say there is a whole proxy kingdom out there! Different types of proxies work well for different tasks and have different features. Proxies can be open and cost nothing or can be private, confined to an individual, or shared among the group of users who pay for them. They can reveal all information about users or hide their identities. Proxies can also be situated in a physical device or located in a cloud. They can change your location regularly or stick with one that was chosen. Finally, they can utilize different protocols.
Once you are familiar with different types of proxies, their applications, and their pros and cons you can make more informed decisions because a proxy can either make or break the task you set.
Originally published on SOAX proxies blog



Top comments (1)
Great breakdown of proxy types—this is a must-read for anyone in data scraping or digital marketing. For those looking for reliable residential proxies, I've been using NodeMaven. They offer clean, long-session IPs with global coverage, making them ideal for tasks like web scraping, managing multiple accounts, or bypassing geo-restrictions. Their service is compatible with both HTTP and SOCKS5 protocols, ensuring seamless integration with various tools and platforms. If you're seeking a proxy provider that offers both performance and reliability, it's worth checking ou nodemaven.com/