One of the most important and the first few services to learn on AWS cloud is AWS Identity and Access Management (IAM).
Amazon Web Services (AWS) offers Identity and Access Management (IAM) as a service, which enables users to manage access and permission to their AWS resources.
In this blog post, I will guide you through the process of creating an IAM user on AWS and configuring it on your computer.
Additionally, I will highlight the disadvantages of relying solely on the root user account for AWS resource creation and management.
Creating an IAM User on AWS
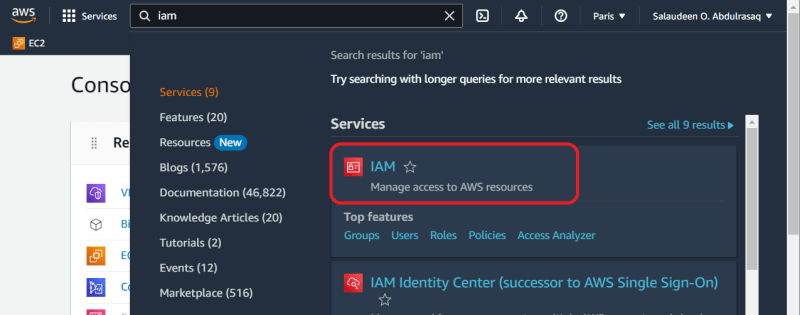
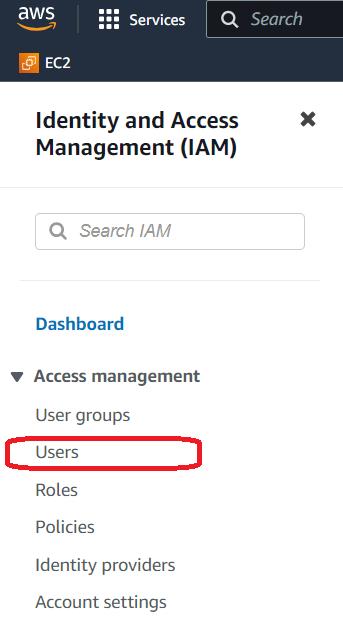
Sign in to your AWS Management Console or create an account
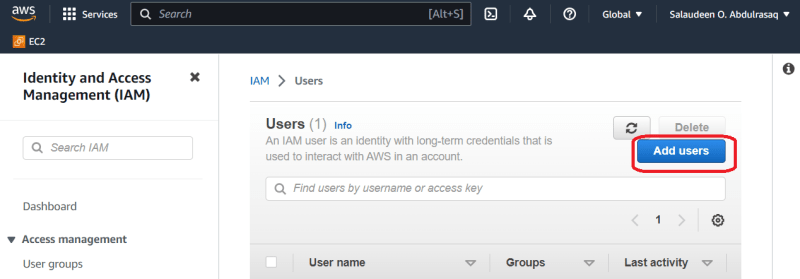
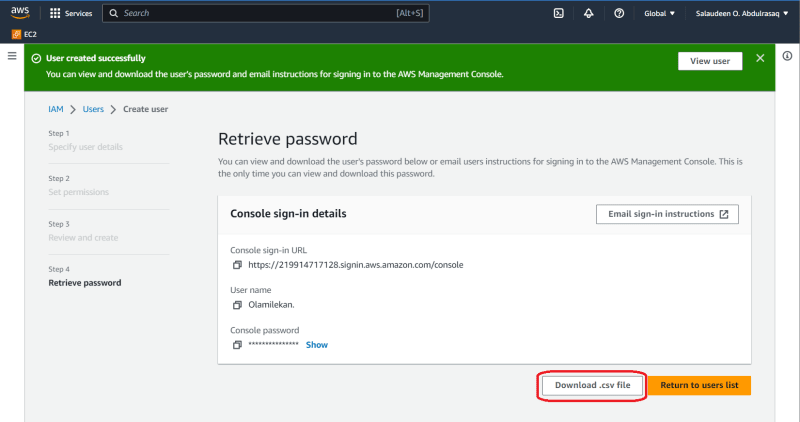
Provide a name (Olamilekan in this case) for the user an access type (programmatic access, AWS Management Console access, or both).

Configure password for the user to be used at console sign-in.

Set permissions for the user by attaching policies. AWS provides predefined policies or allow you to create custom policies to define access. In this case, AdministratorAccess was granted to the user Olamilekan

Click "Download .csv file" to download the Programmatic access credentials i.e (AWS Access Key ID & Secret Access Key ID).
Configuring the IAM User on Your Computer
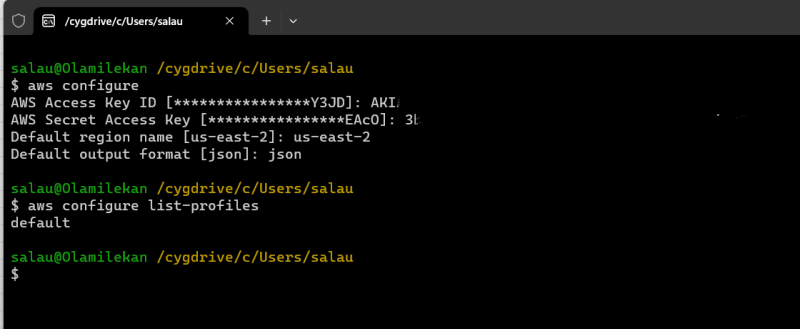
Install AWS Command Line Interface (CLI) on your computer.

Open a terminal or command prompt.
Run the command aws configure and provide the Access Key ID and Secret Access Key of the IAM user you created.
Specify the AWS region you want to use and the default output format.
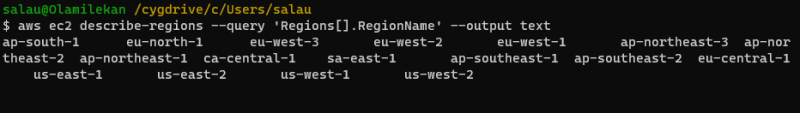
Verify the configuration by running a simple AWS CLI command, such as "aws ec2 describe-regions --query 'Regions[].RegionName' --output text" to display the available regions.
In conclusion, sharing the root user credentials across multiple team members can pose security threats, complicates management and creates operational challenges. Revoking or rotating credentials becomes a cumbersome task, impacting security best practices.
IAM can be leveraged to provide appropraite permission to individuals or teams and reduce several risks associated with the root user account.








Top comments (0)