Thanks to /u/TrollW00t on Reddit for bringing Mozilla Observatory to my attention. In a previous article I talked about improved security ratings from Qualys SSL Labs, but I did not go far enough!
My rating for simplecto.com from Mozilla Observatory was an F!
The creators of Firefox certainly know a lot about browser security, so their Observatory app is a welcome tool. Here we will go step-by step and outline the changes to my config that took it from F to a B.
A ratings are possible but only with Content-Security-Policy, but that can wait for another post.
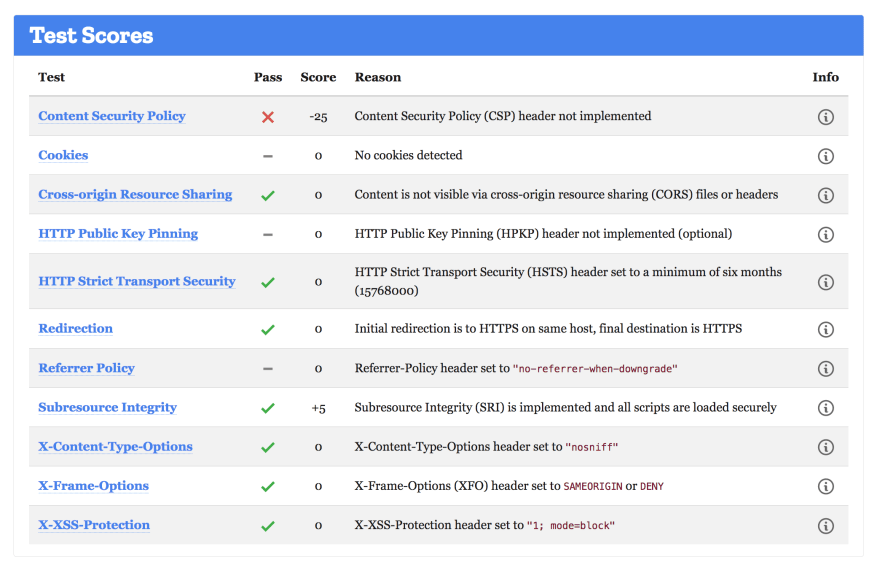
Mozilla Observatory's 11 tests
Below are the secure headers settings I use now in my deployments:
# Adding in secure headers
- traefik.http.middlewares.securedheaders.headers.forcestsheader=true
- traefik.http.middlewares.securedheaders.headers.sslRedirect=true
- traefik.http.middlewares.securedheaders.headers.STSPreload=true
- traefik.http.middlewares.securedheaders.headers.ContentTypeNosniff=true
- traefik.http.middlewares.securedheaders.headers.BrowserXssFilter=true
- traefik.http.middlewares.securedheaders.headers.STSIncludeSubdomains=true
- traefik.http.middlewares.securedheaders.headers.stsSeconds=63072000
- traefik.http.middlewares.securedheaders.headers.frameDeny=true
- traefik.http.middlewares.securedheaders.headers.browserXssFilter=true
- traefik.http.middlewares.securedheaders.headers.contentTypeNosniff=true
The settings above instruct the browser to make it harder for XSS attacks, SSL downgrade attacks, and prevent the iFrame-ing of content into other pages.


Top comments (0)