Ransomware is an epidemic that adversely affects the lives of both individuals and large companies, where criminals demand payments to release infected digital assets.
In the wake of the ransomware success, Ransomware-as-a-Service (RaaS) is being offered as a franchise model that allows people without programming skills to become active attackers and take part in the ransomware economy. This is a way of democratizing crime, giving ordinary people and smaller players an easier way into the criminal market, while reducing the risk of exposure for the ones on top of the value chain. For instance, a dissatisfied employee might decide to partner up with a RaaS developer to effectively infect an organization from the inside and then splitting the profit.
Wait a minute, this sounds like SaaS (Software as a Service) with the exception of mal-intent and ‘R’ prefix instead of ‘S’ ?
Yes, these organized cybercrime groups have been known to offer 24/7 technical support, subscriptions, quality assurance, affiliate schemes, and online forums just like legitimate SaaS companies. They know that offering a quality service to their (admittedly) criminally-minded clients will help both sides of the venture to become wealthy at the expense of victimized individuals or organizations that they prey upon.
What led to the inception of RaaS ?
The first ransomware, known as AIDS ( Aids Info Disk or PC Cyborg Trojan), was observed in the wild already in 1989, spreading through the exchange of floppy disks. Following AIDS ransomware, number of ransomware families were quite low for more than two decades, especially the ones with sophisticated destructive capabilities. However, this all changed with the advent of stronger encryption schemes in the ransomware code and especially the availability of cryptocurrency as a payment method which is fairly difficult to track by law enforcement. In the wake of the ransomware success, ransomware-as-a-service (RaaS) has become an entry point for criminals with little programming skills to participate and earn money from ransomware.
Is there an underpinning supply-chain that benefits a RaaS provider?
Contacting ransomware service providers using dark-net markets, prospective and existing criminal networks can cheaply obtain tailor-made ransomware ready to be used on their prospective victims. In addition to the creation fee, the service providers may take a 20–30% revenue share of the ransom as well.
RaaS can have different delivery formats,
- such as source code that the buyer compiles themselves,
- pre-compiled binaries or an interactive interface where the buyer inputs information about the victims.
- Quality testing weaponized source code or per-compiled binaries to ensure that it operates as expected (usually tested on low risk victims)
This collaborative strategy is a way of achieving a faster rate of infections with a lower risk of getting caught.
Who are the stakeholders in such a ransomware based supply chain?
The stakeholders involved in the underground economy have different responsibilities and expose themselves to different types of risks. They defined several roles, including
- virus writers (developers),
- website masters/crackers,
- envelope (account) stealers,
- virtual asset stealers/brokers and
- sellers and players (buyers)
- mixers and tumblers (money laundering post-transaction)
What is the economics of such an attack from offender and victim’s point of view?
Similar to a SaaS pricing and distribution model, a victim is profiled and targeted based on their business domain, market share, clients that they serve and WTPR (willingness to pay ransom). The amount of a single ransomware can be of a fixed price or discriminated based on several factors (basis associated with complexity of vulnerability the malware is exploiting).
Who is REvil and why are they relevant to this conversation?
REvil (also known as Sodin and Sodinokibi) is a ransomware-as-a-service (RAAS) enterprise that first came to prominence in April 2019. Their claim to fame is based on the employed tactics and techniques which include and not limited it
- Their ideal victim profile (like ideal customer profile in SaaS) range from home users to F500 companies
- Known to successfully extort far larger payments from large corporate companies
- Execute methodical workflow to exfiltrate data prior to encrypting for ransomware (apply additional pressure to leak if victim chooses to restore from backup and not pay ransom)
- Yes, REvil has its own web presence (a web site) and often release/update a so-called “Happy Blog” listing their victims, sample of exfiltrated data and a “trial” decryption upon sample subset as a proof-of-decryption (this almost sounds like a SaaS activation, acquisition and retention funnel)
- A timer countdown is often pinned to a victim’s profile in order to pressure for response/payment.
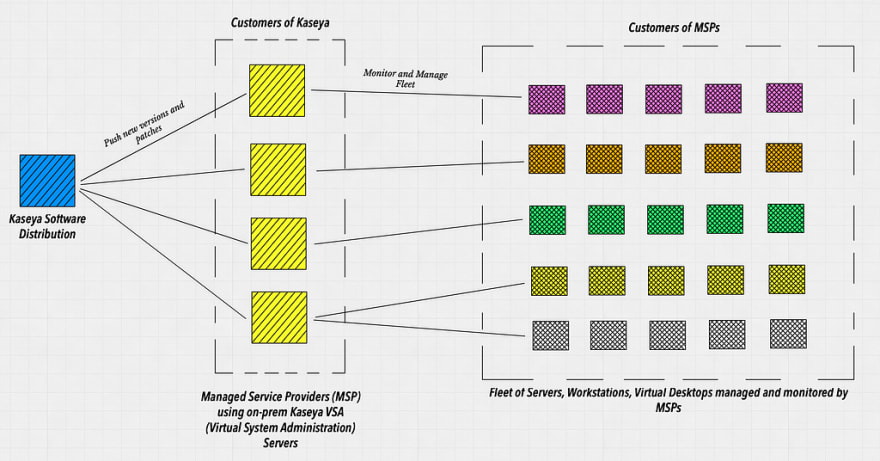
Who is Kaseya and why are they relevant to this conversation?
Kaseya sells unified IT monitoring & management software for MSP (Managed Service Providers) and IT reams (multi and single site). The MSPs in turn sell monitoring and management services to their customers. Let’s visualize the supply chain distribution of Kaseya software
How did REvil victimize Kaseya?
Kaseya’s VSA server v9.5.6 had multiple vulnerabilities that were responsibly disclosed by Frank Breedijk. The vulnerabilities including and not limited to
- SQL command injection — patched April 10th, 2021
- Local File Inclusion — patched May 8th, 2021
- Credentials Leak — unpatched (CVE rating 10/10) leading to Request Forgery token bypass
- a 2FA (2 factor authentication) bypass on limited API scope — unpatched (CVE rating 9.9) leading to Authentication bypass + Code Injection. The 2FA logic only protected the VSA dashboard but not Live Connect
- Having more than 1 tab open in Live Connect, with remote-connect into a fleet PC/virtual desktop/workstation & rebooting it would cause it to reconnect from the last opened tab instead (cross connect within and across fleet instances)
- a reflected XSS upon a authenticated API path — unpatched
During the month of June/July 2021, REvil discovered the exposed VSA servers (possibly via recon) and further on, discovered the unpatched vulnerabilities. REvil took credit for launching one of the farthest reaching ransomware attacks on record beginning July 2 and demanded $70 million in Bitcoin in exchange for a universal decryption routine.
- The unpatched vulnerabilities on the exposed VSA servers were exploited to introduce a malicious script that was sent to all computers managed by the server, thereby transitively reaching all the end clients. The script further on encrypted the systems.
- Trustwave discovered that the malware won’t execute on systems that have Russian, Ukrainian, Belarusian and Romanian default languages set and former Soviet bloc nations in Central Asia, Caucasus as well as Syria.
Why did Kaseya fail to address these inherent security issues?
As per the latest Bloomberg article,
Among the most glaring problems was software underpinned by outdated code, the use of weak encryption and passwords in Kaseya’s products and servers, a failure to adhere to basic cybersecurity practices such as regularly patching software and a focus on sales at the expense of other priorities, the employees said.
One of the former employees said that in early 2019 he sent company leaders a 40-page memo detailing security concerns and was fired about two weeks later, which he believed was related to his repeated efforts to flag the problems.
Another employee said Kaseya rarely patched its software or servers and stored customer passwords in clear text — meaning they were unencrypted — on third-party platforms, practices the employee described as glaring security flaws.
Some engineers and developers at the company said employees quit over frustration that new features and products were being prioritized over fixing problems. Others were laid off in 2018, when Kaseya began moving jobs to Minsk, Belarus, where it recruited more than 40 people to do software development work that had previously been carried out in the U.S., according to two of the former employees familiar with the matter. Four of the ex-workers said they viewed the outsourcing of work to Belarus as a potential security issue, given the country’s close political allegiance with the Russian government.
Should we (as SaaS and software vendors) be concerned ?
As U.S. Army Gen. Keith Alexander , aptly paraphrased — “ Either you know you’ve been hacked, or you’ve been hacked and you don’t know you’ve been hacked ,”
If you are authoring and distributing software as COTS or SaaS (agent, runtime observability, management-monitoring, transactions based, web-based, etc) you should concerned and stay on top of measuring your supply chain’s security posture.
What should we (as SaaS and software vendors) be measuring ?
- Detecting Vulnerabilities (OWASP/NIST/MITRE ATT&CK) in your application source code (severity does not matter as a low severe vulnerability can be chained with a logic flaw to initiate an attack sequence)
- Detecting Business logic flaws in your application — example IDOR (Insecure Direct Object Reference)
- Detecting sensitive data, secrets and token leaks that can be weaponized to infiltrate your hosted applications.
- Detecting vulnerable OSS (open source software) that are exploitable on an exposed path
- Detecting risk of insider attacks — identify use of suspicious APIs and code flows that can be weaponized in an attack sequence
These detection capabilities should not occur in isolation as context is lost if not correlated.
What should we do and how can ShiftLeft help?
Let’s collectively examine the how we can protect ourselves from this situation
- Pay attention to every vulnerability reported (critical or non-critical) and determine if it can become a candidate of an attack chain. Even a simple vulnerability can be weaponized by a RaaS vendor in the dark-net.
- Classify your sensitive data and secrets and then determine its lineage, provenance and exposure/leak across all points in your software stack.
- Apply the same rigor/discipline of vulnerability discovery and disclosure with all sites of software development (multi-office, offshore development) and vendors that you partner with.
- Identify insider attacker risk, as a dissatisfied employee might decide to partner up with a RaaS developer to effectively infect an organization from the inside and then splitting the profit.
- Identify and regularly update open source libraries that are vulnerable and can be exploited on exposed API endpoints.
- Protect ALL endpoints using 2FA (not just a subset) and operate at heightened level of security
We at ShiftLeft have been studying and provisioning advanced detection policies using code property graph since mid 2019 (that includes OWASP based vulnerabilities, sensitive data leaks, insider attacks, exploitable open source based vulnerabilities, exposed API endpoints). Speak to us and we can help assess and recommend more efficient processes and procedures.







Top comments (0)