How to help devs write code, learn security, and fight attackers
Securing software is friggin complicated.
Supply chain attacks, the OWASP top ten, ransomware, insider attacks, and plain old typos. As software development becomes increasingly fast-paced, the potential threats that can compromise security don’t stop. If anything, the likelihood of releasing vulnerabilities into production increases as we push out more and more software each day.
Developer education is key to reducing security risks
Security is a team effort by everyone: application security engineers, system administrators, managers, architects, and analysts. But when dealing with application security, developers are the ones who write vulnerabilities into code, and developers are the ones who have to fix vulnerabilities when they are found.
More and more so, developers need to perform a majority of application security work. However, not all developers feel prepared to deal with security issues. In fact, a GitLab survey found that 70% of developers shared that they struggle to write secure code and need better guidance.
So as developers, we need to educate ourselves and teach fellow developers about security and how it is relevant to our work. If we as developers can learn about the common pitfalls of application security and secure development, we can prevent vulnerabilities from being introduced into the code base, saving ourselves and our colleagues time and headache down the line.
When, where, and how?
So security education for developers is not so much a question of “why,” but rather: when, where, and how do we introduce developer education?
Developer security education needs to be efficient, engaging, and easy to absorb. So the best time to introduce security education is immediately after a security issue is found in a developer’s code when the code is still fresh in their mind. We should also integrate security education into the security tools developers use to limit context switching and friction introduced by the training.
To help developers write secure code, we also need to show how security impacts their users. Beyond standard security training that teaches developers about technicalities like XXS, SQLi, and insecure deserialization, we need to introduce security training in a way that is relevant to everyday development work. By highlighting vulnerabilities in a developer’s code, we can provide the context of the security issue and demonstrate the real-life importance of best practices.
By incorporating security education into the development process, we can make learning easy. And by providing security training with context, we can make it clear why developers should care.
Learn at ShiftLeft
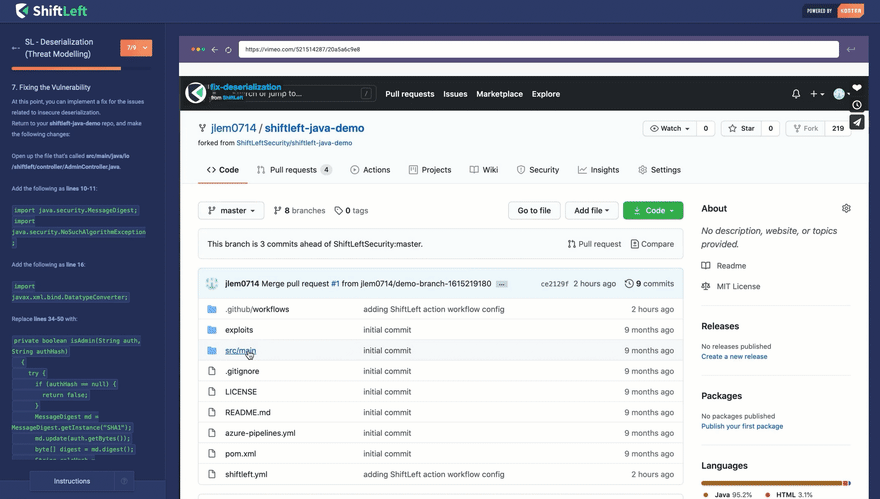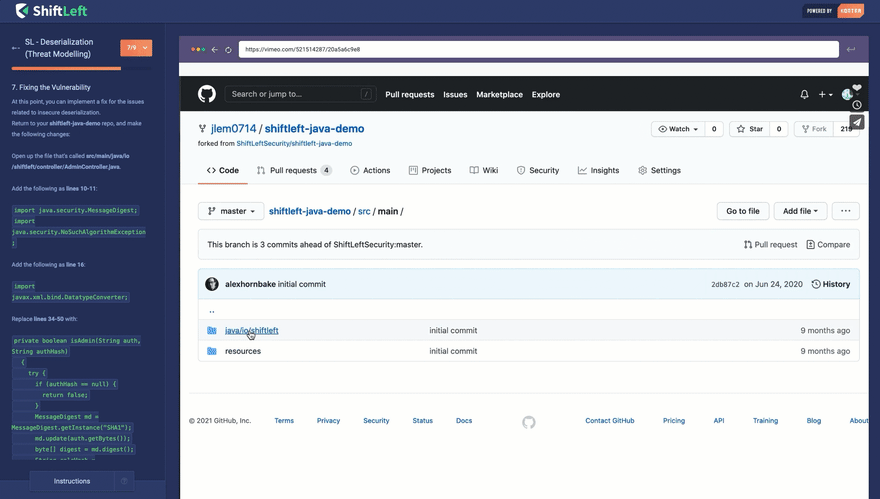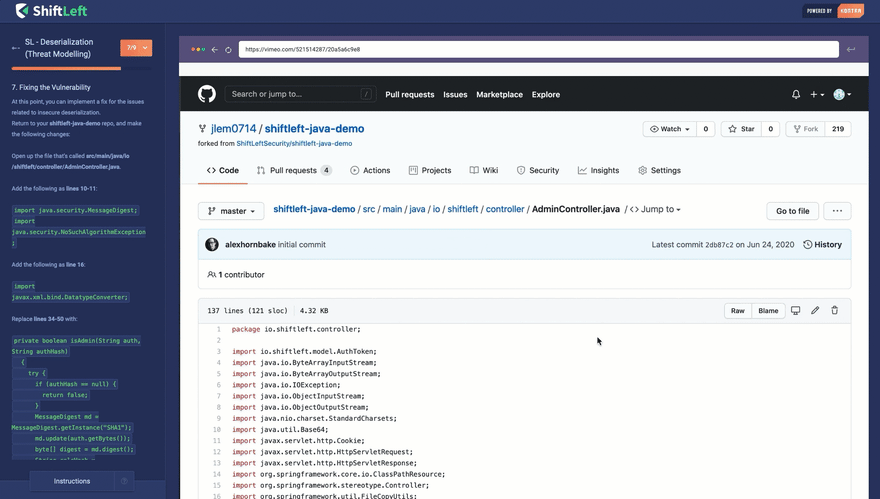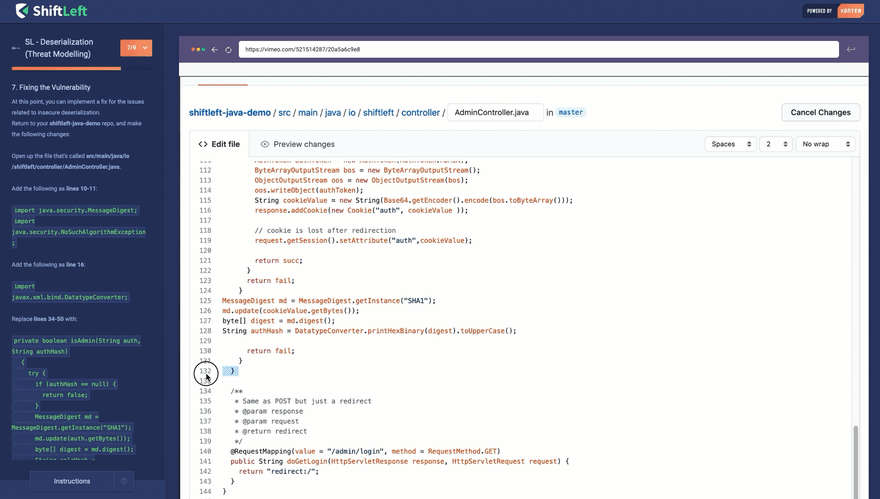
If you are a developer who wants to learn about security, check out our free security training site at: https://www.shiftleft.io/learn/. Here, we explain how a type of vulnerability happens, why it happens, how attackers can exploit it, and how to mitigate it. Our training utilizes real codebases and tools, showing you how you realistically mitigate a vulnerability once it's found in your code.
Thanks for reading! What is the most challenging part of developing secure software for you? I’d love to know. Feel free to connect on Twitter @vickieli7.







Top comments (0)