Before you can start create the SSO Client, you would have to get SSO service up and running. Do read my post on the SSO User & Access Management Service.
While SSO service takes care of authentication, SSO Client is in charge of authorizations.
Here are some mechanism to manage the authorizations.
- JWT session key for API calls
- Role & Policies Management.
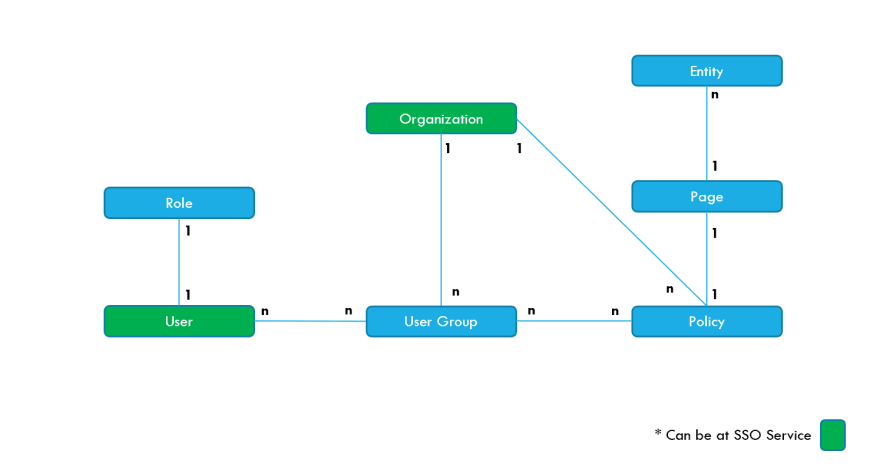
Role & Policies Management
Here is how I organize my entities and relationship:
Here are some of the underlying activities that is going on after the user successfully get AUTHENTICATED from SSO (All these are handle by the IAM service):
- Upon successful login. The Landing Page will do the follow:
- If he is “ROOT” role, no policies will applies.
- If he is of “IAM_USER” role, the server will retrieve the Organizations and its policies if any. He will then choose the organization he wants to access. The respective organization’s policy will apply.
- Next he will brought to the home page. The Menu he can access will be calculated and generated to his policies.
- He can switch organization while in the application.
- In every page access, the USER ID, PAGE and ENTITIES will be passed to IAM service to determine the rights for every entities on the page. Default action for each entity is USE, CREATE, VIEW, UPDATE & DUPLICATE.
Here are some of the nice features I have implemented:
- Timeout of 5 mins of inactivity.
- After inactivity timeout, a further 20 seconds countdown to automatic logout. User can click continue to restart the timeout counter.
- Prohibits concurrent sessions for same user.
- Every time a successful user login, the session key will be store in the local cookie and database at server side.
- It means the latest session key will overwrite the older session key of user. The latest browser login will render the older browser session invalid.
- Every time a page calls a API (attach the session key in cookies), the API will compare session key to the database session key. If unmatched, means the session is invalid.
- The Page will revoke the session and logout automatically is session key is invalid.
- Role and Policy management.
- Audit Logs with retaining policy of at least 360 days.
- User session key that will expire < 8 hours.
I have implemented all these SSO Client services using NODEJS with Express, REDIS & MongoDB as cornerstone back-end stack. Front-end I use a Core UI bootstrap admin template as base.


Top comments (0)