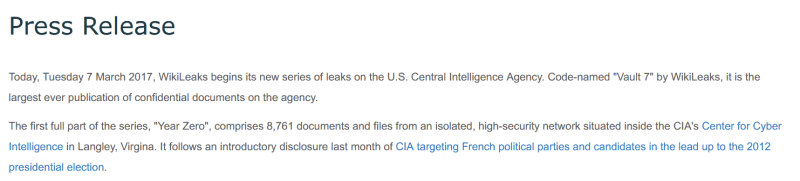
WikiLeaks just released internal documentation of the CIA’s massive arsenal of hacking tools and techniques. These 8,761 documents — “Vault 7” — show how their operatives can remotely monitor and control devices like phones, TVs, and cars.
And what’s worse, this archive of techniques seems to be out in the open, where all manner of hackers can use it to attack us.
- “The CIA lost control of most of its hacking arsenal, including malware, viruses, trojans, weaponized “zero days” exploits, malware remote control systems and associated documentation. This extraordinary collection, which amounts to over several hundred million lines of code, gives its possessor the entire hacking capacity of the CIA.” — WikiLeaks.
WikiLeaks has chosen not to publish the malicious code itself “until a consensus emerges on… how such ‘weapons’ should be analyzed, disarmed and published.”
But this has laid bare just how many people know these devastating hacking techniques.
- “This archive appears to have been circulated among former U.S. government hackers and contractors in an unauthorized manner, one of whom has provided WikiLeaks with portions of the archive.” — WikiLeaks.
Disturbingly, these hacks were bought or stolen from other countries’ intelligence agencies, and instead of closing these vulnerabilities, the government put everyone at risk by intentionally keeping them open.
- “[These policy decisions] urgently need to be debated in public, including whether the CIA’s hacking capabilities exceed its mandated powers and the problem of public oversight of the agency.” — the operative who leaked the data
First, I will summarize three takeaways from today’s Vault 7 release that every American citizen should know.
Then, I’ll give you actionable advice on protecting yourself from this illegal overreach by the US government and the malicious hackers the government has empowered through its recklessness.
Takeaway #1: If you drive an internet-connected car, hackers can crash it into a concrete wall and kill you and your family.
Crazy, but it’s real.
- “As of October 2014, the CIA was also looking at infecting the vehicle control systems used by modern cars and trucks. The purpose of such control is not specified, but it would permit the CIA to engage in nearly undetectable assassinations.” — WikiLeaks.
We’ve known for a while that internet-connected cars could be hacked. But we had no idea of the scope of this until today.
Like other software companies, car manufacturers constantly patch vulnerabilities as they discover them. So, if you have an internet-connected car, always update its software's latest version.
As Wikileaks makes more of these vulnerabilities public, car companies should be able to patch them and release security updates quickly.
Takeaway #2: It doesn’t matter how secure an app is — if its operating system gets hacked, it is no longer secure.
Since the CIA (and probably many other organizations now) know how to compromise your iOS and Android devices, they can intercept data before it even reaches the app. This means they can grab your unencrypted input (microphone, keystrokes) before Signal or WhatsApp can encrypt it.
One important way to reduce the impact of these exploits is to open source as much of this software as possible.
- “Proprietary software tends to have malicious features. The point is that when the users don’t have the source code with a proprietary program, we can never tell. So you must consider every proprietary program as potential malware.” — Richard Stallman, founder of the GNU Project.
You may be thinking — isn’t Android open source? Its core is open source, but Google and handset manufacturers like Samsung are increasingly adding closed-source code on top of this.
In doing so, they’re opening themselves up to more ways of getting hacked. When code is closed source, there’s not much the developer community can do to help them.
- “There are two types of companies: those who have been hacked, and those who don’t yet know they have been hacked.” — John Chambers, former CEO of Cisco
By open-sourcing more of the code, the developer community will be able to discover and patch these vulnerabilities much faster.
Takeaway #3: Just because a device looks like it’s turned off doesn’t mean it’s really turned off.
One of the most disturbing exploits involves making Smart TVs look turned off but leaving their microphones on. People all around the world are literally bugging their own homes with these TVs.
The “fake-off” mode is part of the “Weeping Angel” exploit:
- “The attack against Samsung smart TVs was developed in cooperation with the United Kingdom’s MI5/BTSS. After infestation, Weeping Angel places the target TV in a ‘Fake-Off’ mode so that the owner falsely believes the TV is off when it is on. In ‘Fake-Off’ mode, the TV operates as a bug, recording conversations in the room and sending them over the Internet to a covert CIA server.” — Vault 7 documents.
The leaked CIA documentation shows how hackers can turn off LEDs to make a device look like it’s off.
Do you know that light that turns on whenever your webcam is recording? That can be turned off, too. Even the director of the FBI — the same official who recently paid hackers a million dollars to unlock a shooter’s iPhone — is encouraging everyone to cover their webcams.
Just like how you should always treat a gun as though it were loaded, you should always treat a microphone as though it were recording.
Webcomic by XKCD
What can you do about all this?
It’s not clear how badly all of these devices are compromised. Hopefully, Apple, Google, and other companies will quickly patch these vulnerabilities as they are made public.
There will always be new vulnerabilities. No software application will ever be completely secure. We must continue to be vigilant.
Here’s what you should do:
- Don’t despair. You should still do everything you can to protect yourself and your family.
- Educate yourself on cybersecurity and cyberwarfare. This is the best book on the topic.
- Take a moment to read my guide on encrypting your entire life in less than an hour.
The Vault 7 leaks revealed just a portion of the CIA's hacking capabilities as of 2017. It's safe to assume their tools and techniques have advanced significantly in the past 6 years. While some of the specific exploits revealed may have been patched, the general capabilities likely remain.
Some key developments since 2017:
- Increased use of zero-day exploits - Undisclosed vulnerabilities that the CIA and other agencies stockpile and use for hacking before they become public. This remains highly controversial but continues.
- Advances in compromising encrypted messaging - Reports indicate the CIA has developed techniques to hack encrypted chat apps by targeting the OS and endpoints, as the Vault 7 docs revealed. Signal and WhatsApp may remain relatively secure but cannot fully protect against compromised devices.
- Expanding IoT ecosystem provides more targets - With more Internet-connected devices like cars, TVs, and home assistants, the attack surface has grown exponentially. These likely remain ripe targets for intelligence agencies.
- Supply chain attacks - Rather than attacking devices directly, injecting malware into hardware and software supply chains allows hacking on a mass scale. The SolarWinds hack used this to compromise government agencies and corporations.
- AI-enabled hacking - While AI can bolster cybersecurity, it also empowers hacking by automating tasks and allowing more sophisticated social engineering. There are surely classified efforts by the CIA and others to use AI for offensive hacking.
- Increased funding and prioritization - The federal cybersecurity budget has ballooned to over $10 billion in 2021, with billions more on classified programs. The CIA and NSA have elevated cyber ops as a top priority. Their capabilities have certainly grown proportionally.
While cybersecurity has improved for major tech companies and individuals following best practices, the capabilities of sophisticated state-level actors like the CIA have likely advanced even faster.
The Vault 7 revelations were just the tip of the iceberg for what offensive hacking agencies are working on today. Maintaining vigilance and advocating for oversight and accountability of these groups remains important.
If you find this post exciting, find more exciting posts on the Learnhub Blog; we write everything tech from Cloud computing to Frontend Dev, Cybersecurity, AI, and Blockchain.
This article was culled from Quincy Larson's post on Medium and published on Learnhub Blog.




Top comments (3)
These were released around 7.5 years ago?
It's started clearly in the article that from 2017 what has the CIA been doing, are they more transparent?
That's the whole idea.
I was just confused, as you open your post with (emphasis mine):