In a traditional data center you create one perimeter, secure them by installing firewall, WAF, SIEMS etc. and have 100% confidence that the data center is secure. However, when you migrate to cloud then your VPC or Virtual Network is not 100% secure you have to not only secure your perimeter however, inside of perimeter you have to take care of security. Since it’s a public cloud you have to be more cautious and make sure whatever workload or source code you are moving to is cloud aware. There are various best practices at each level you have to take care of in order to secure your cloud.
What is Defense in-depth?
There is a concept of Defense in-depth which makes sure that at each level there is security in-place which makes your cloud data center almost 100% secure. However, it needs continuous awareness, assessments and audits. In this article let’s explore how Azure helps us to secure data centers in the cloud.
Defense in-depth design of azure services and capabilities to help you secure, manage and monitor your cloud data, infrastructure, compute Azure offers unified security management and advanced threat protection for your cloud, on-premise data centers or both.
When you want to secure your cloud you should think of securing from the physical layer till your data layer.
Defense In-depth security layers are as follows:
- Physical Security ( within your data-center )
- Policies and Access / Identity and Access Management
- Perimeter
- Networking
- Virtual Machines/Compute
- Applications
- Data
Microsoft Azure Security Center
In Microsoft Azure all resources and services are designed to keep Defense in-depth in mind.
Azure Advisor in Azure helps us to maintain our workload to follow well-architected-framework guidelines by showing overall score. Similarly Azure Security Center helps us to do defense-in-depth and it shows the all score of your cloud security health.
Security center has a lot of practical recommendations and quick fixes to keep our workload protected.
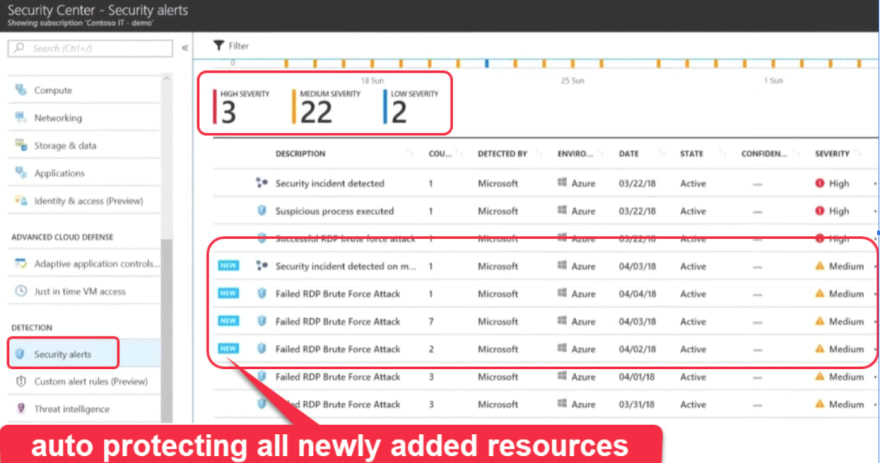
Azure Security center provides unified visibility, control and adaptive threat protection to the resources. So if you add any new resource they will be automatically under threat protection and detection policies. So they are secured from all network attacks.
Additionally Azure Security Center has Intelligent Threat Detection response.
Let’s understand how we would set up defense in-depth in the cloud starting from physical layer security up to data layer security.
Physical Security
For physical security of cloud Infrastructure cloud providers are responsible. Therefore as a customer we should not be worried about securing physical data centers, racks, wire etc. Azure data center security is at high top priority. Cloud providers like Azure or AWS or Google Cloud are responsible for “Security of the Cloud” - Azure is responsible for protecting the infrastructure that runs all of the services offered in the Azure Cloud. This infrastructure is composed of the hardware, software, networking, and facilities that run Azure Cloud services.
Policies and Access
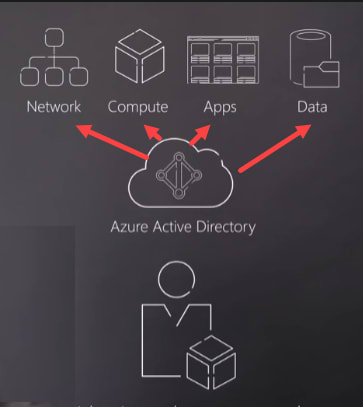
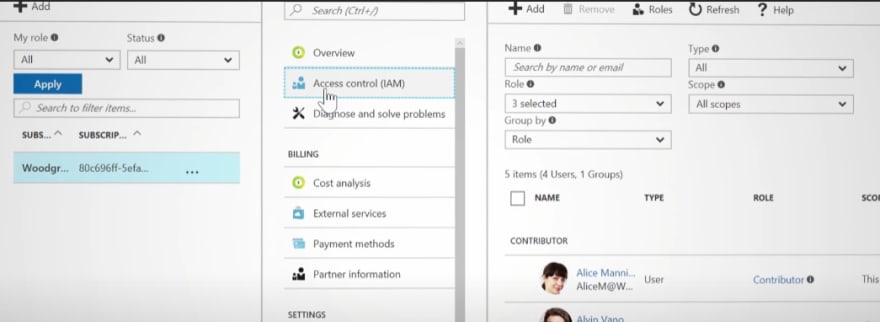
In Azure everything starts with Identity and Access. All Azure resources ( Network, Compute, Apps, Data etc.) are governed by Azure Active Directory. You can also add policies and Role based access control for each individual resource in your cloud.
Azure has a separate service to manage security policies and access to resources. Weather accessed by people or programs by REST API calls to your resources. This can control which processes can access your application files or data and granular access is delegated.
These controls are the front door of your environment. Your IT can make developers as contributors, marketing users as readers and so on by applying role based access control (RBAC). Role could be owner, contributor or reader and many other in-built roles are available.
Perimeter Security
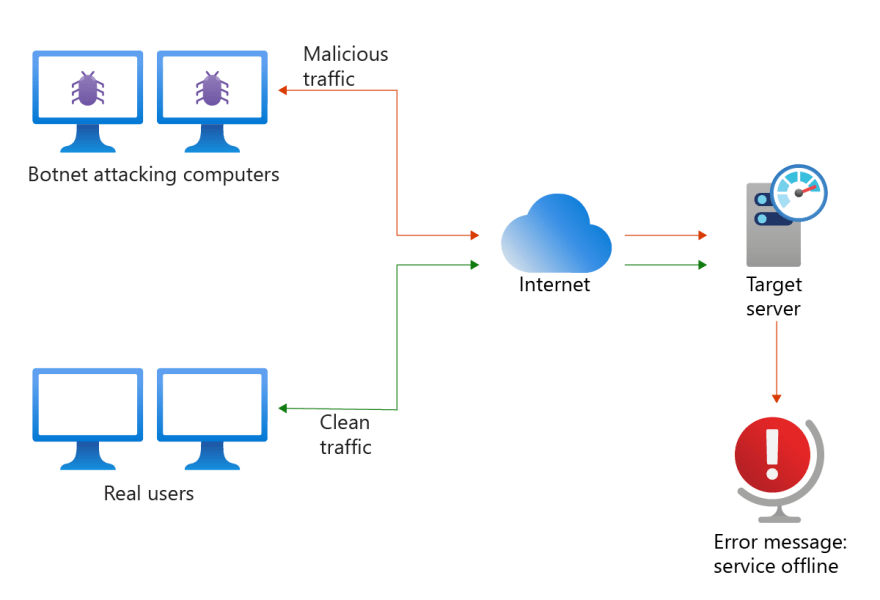
Perimeter networks in the cloud enable secure connectivity between your cloud networks and your on-premise or physical datacenter network. Perimeter network is also called a demilitarized zone or DMZ. The number of DDoS (Distributed Denial of Service Attacks) over 100 GB/s in volume increased 776 percent in Q1 2020. In a DDoS attack, a perpetrator intentionally floods the system, like a server, website, or other network resource, with fake traffic.
In order to secure your perimeter in the cloud you must set up a Firewall. You may want to also install IPS (Intrusion Prevention Systems) & IDS (Intrusion Detection Systems ) to detect and prevent unwanted traffic and block not requiring ports and IPs.
Also you must protect your perimeter from Distributed denial of service (DDoS) attacks. Every property in Azure is protected by Azure’s infrastructure DDoS (Basic) Protection at no additional cost.
Layer-7 DDoS protection can be achieved by using Azure’s DDoS Protection for protection against DDoS attacks.
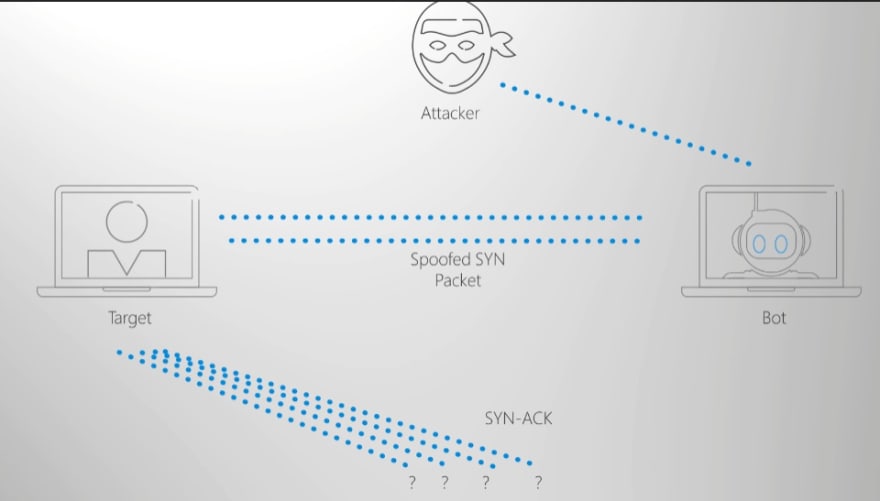
Azure DDoS protection will save from protocol attack where the attackers tries to find and exploit weaknesses in layer 3 (Network) and 4(Transport) stacks.
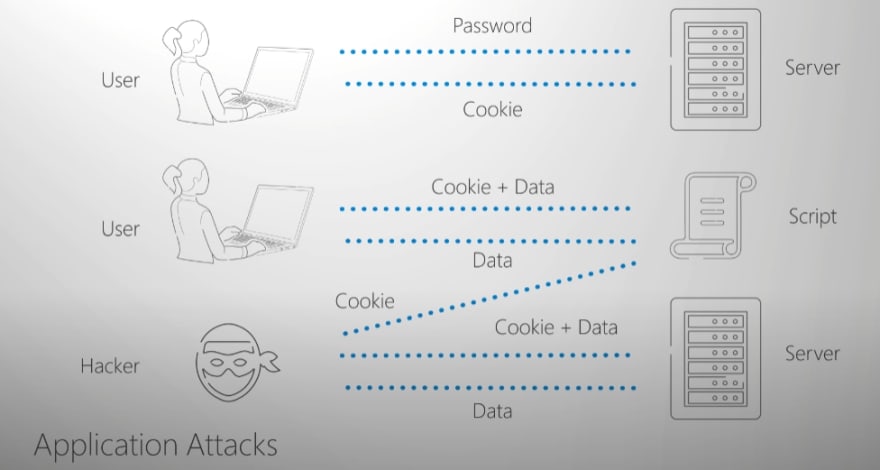
Application attack where the application packets are used to disrupt transmission of data between hosts like cross-site scripting or HTTP protocol violation attacks.
Network Protection
Azure Security center will report on potential network and security issues related to open ports and firewall settings and Network Security Groups (NSG). You can enforce logical network boundaries and limit permissions to NSG.
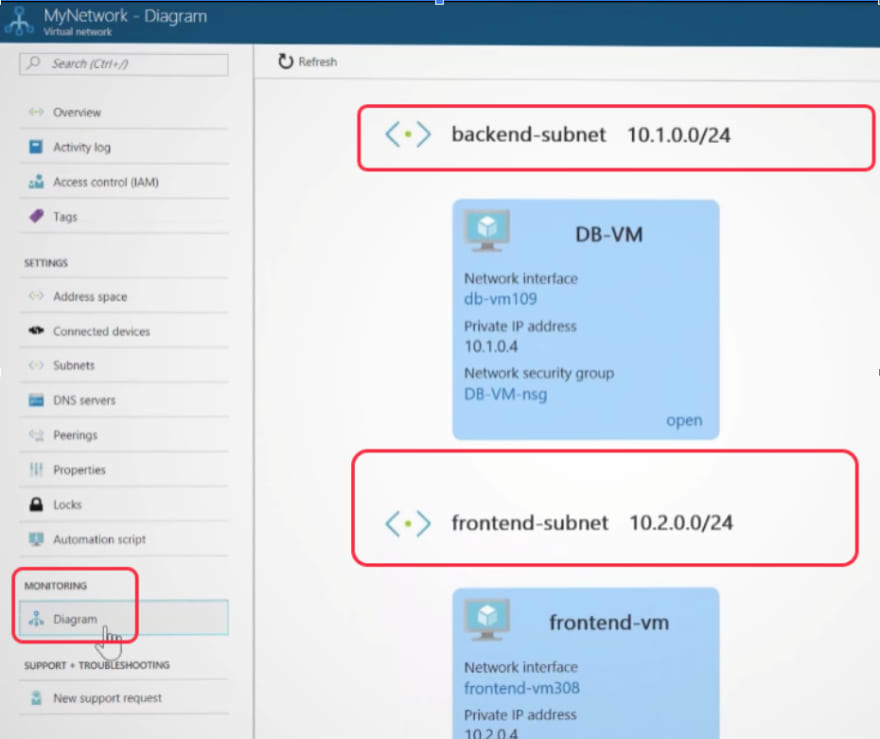
With enabled network watchers you can quickly go to the my network diagram page and check the diagram for the selected virtual network, select the desired subnet and open/close port or block IP addresses.
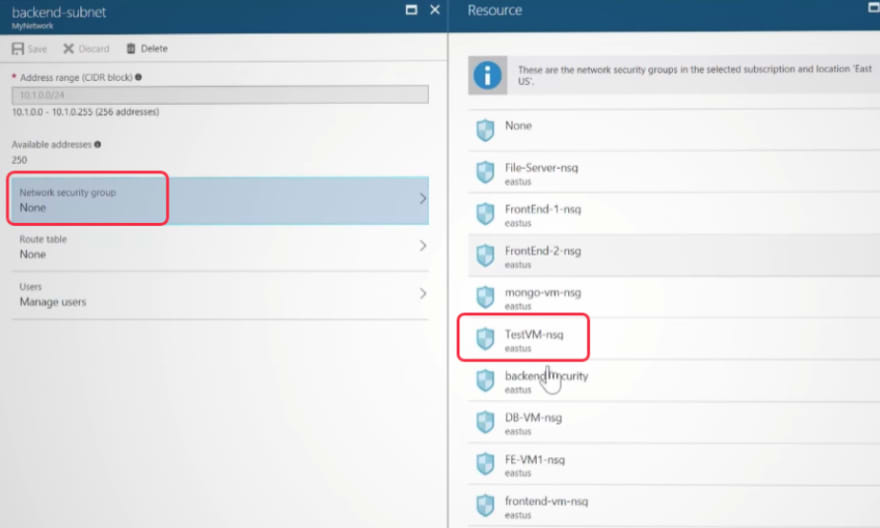
If I select the backend subnet and then I can see all of the network security group (NSG) and identify the desired NSG to analyze.
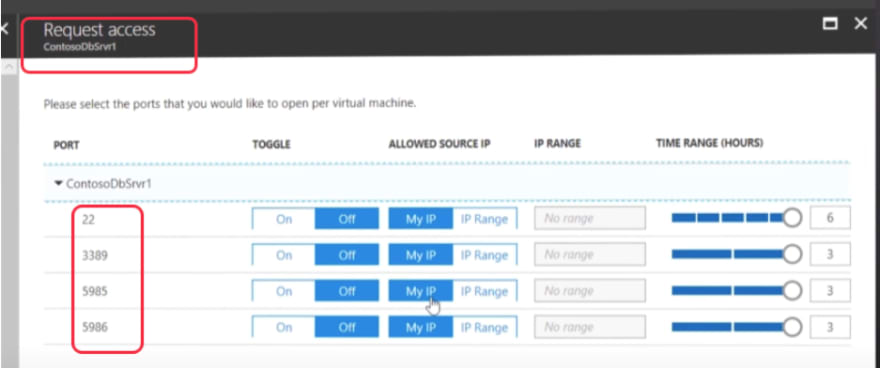
Once I get into the NSG page for a desired subnet then I can manually enable/disable ports or range of IP addresses. You can also enable just in time port access for your virtual machine and manage open ports.
With intelligent recommendations to reduce exposure to brute force attacks.
Additionally, your network in the cloud can be protected by enabling monitoring, encryption and network segmentations.
Compute Protection
Compute means your Virtual Machines and such (IaaS) things in the cloud. Azure Security Center will also provide an actionable item list for your virtual machines. Tell you what the patches are pending with their severity using machine learning.
You should set up NSG on the Virtual machine NIC (Network Interface Card ) and secure it by disabling port or IP addresses if required. So that it will keep unwanted traffic out of the host.
Make sure you have installed proper antivirus in the Virtual Machines. Microsoft Antimalware for Azure is free real-time protection capability that helps identify and remove viruses, spyware, and other malicious software, with configurable alerts when known malicious or unwanted software attempts to install itself or run on your Azure systems.
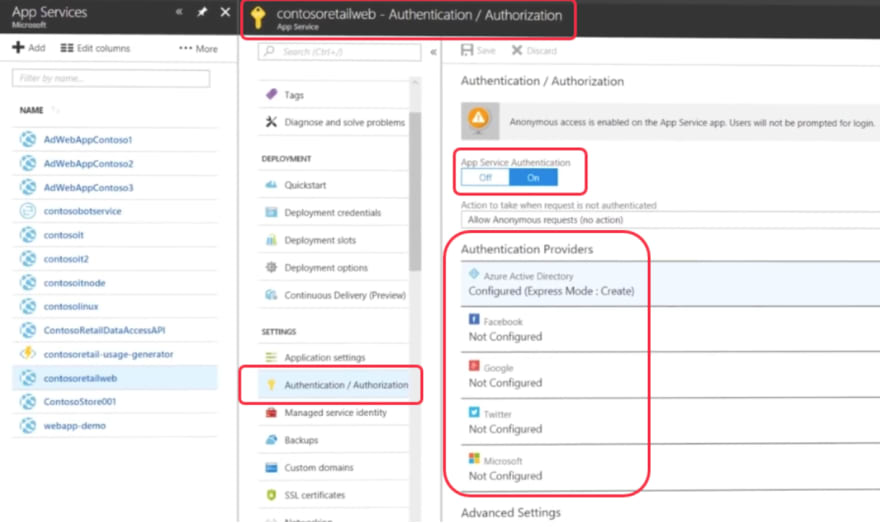
Single SignOn is another feature that prevents users from entering passwords and protects us from various security attacks. Use Azure Active Directory authentication and Managed identity that includes System or User Defined Identities to auto authenticate other processes trying to access your virtual machines.
Virtual Patching is another workaround that we should use to protect existing legacy applications installed on cloud virtual machines. Legacy applications are not cloud ready and they have various vulnerabilities. Most of the time we do not have permission/bandwidth/budget to modify them. At that time to protect them in the cloud we can use virtual patching. Many 3 party extensions are available from azure marketplace for that. Virtual patching works with WAS and WAF together. It uses WAS( Web Application Scanning) to scan installed applications in the virtual machine and whenever it finds a threat it creates an automatic rule in the Web Application Firewall (WAF). This security option is best for many lifts and shifts of legacy virtual machines or physical machines.
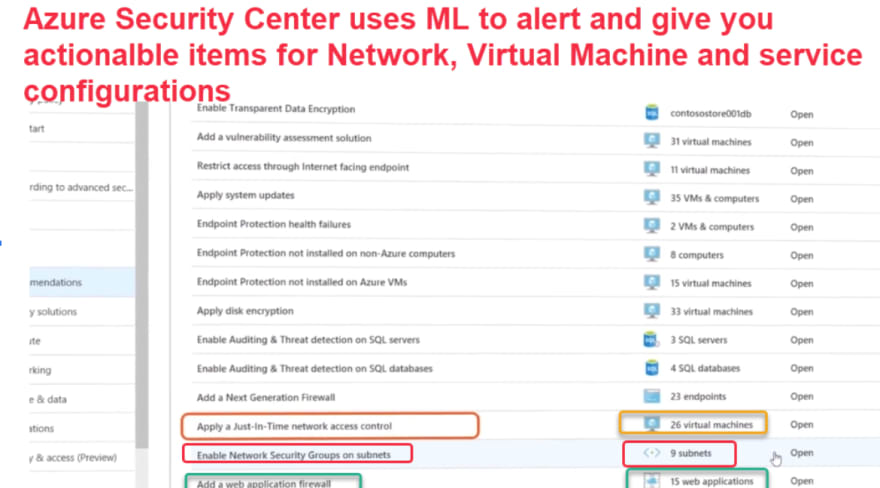
The Azure Security center uses machine learning to continuously assess security and vulnerability levels of your Virtual Machines, Networks and service configurations. It also gives you actionable recommendations to prevent exploits before they occur.
Example of Virtual Machine recommendations by Azure Security Center are as below:
- Apply a Just-In-Time network access control
- Enable NSG
- Apply Disk encryption
- Apply System updates
- Restrict access through internet facing endpoint
Azure Security Center has Adaptive Application Control that dynamically applies both allow and block lists to keep unwanted traffic out of your virtual machines.
If you are using Hybrid Cloud still you can leverage the Azure Security Center features for your on-premise or 3rd party cloud resources. Because Azure Security Center gives many features for your VMs in other clouds and in your data center.
You can implement Intelligent Threat Detection and Response.
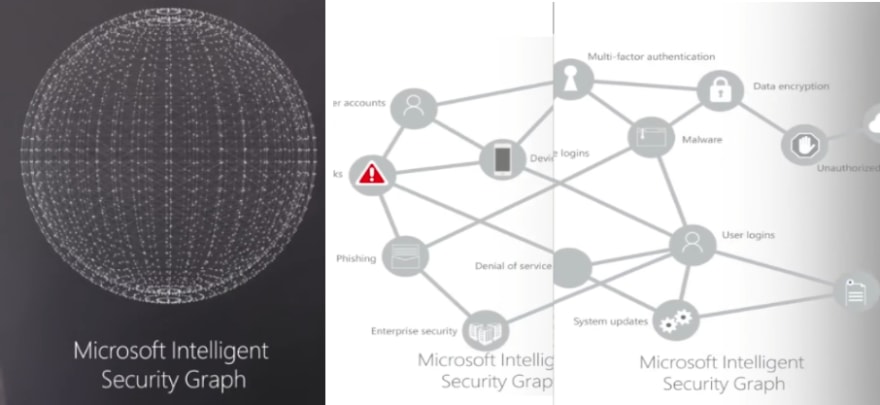
The security center leverages the Microsoft Intelligent Security Graph to discover and take action against attacks. It combines cyberintelligence that Microsoft collects across all of its services and industry data to block known attack patterns. You can also prioritize alerts and incidents that are important to you.
You also get a unified view for forensics analysis and the ability to search across all of your compute resources.
You can also configure the sys log, setting the advanced threat analytics.
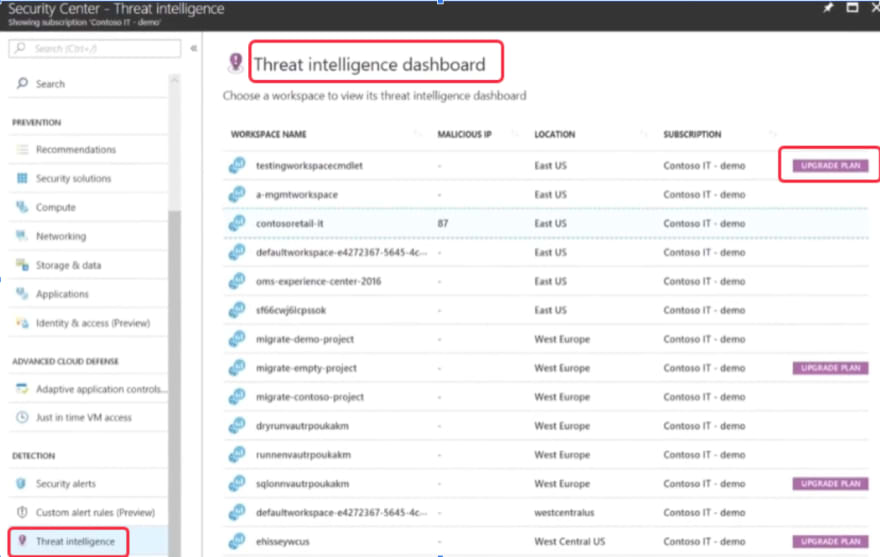
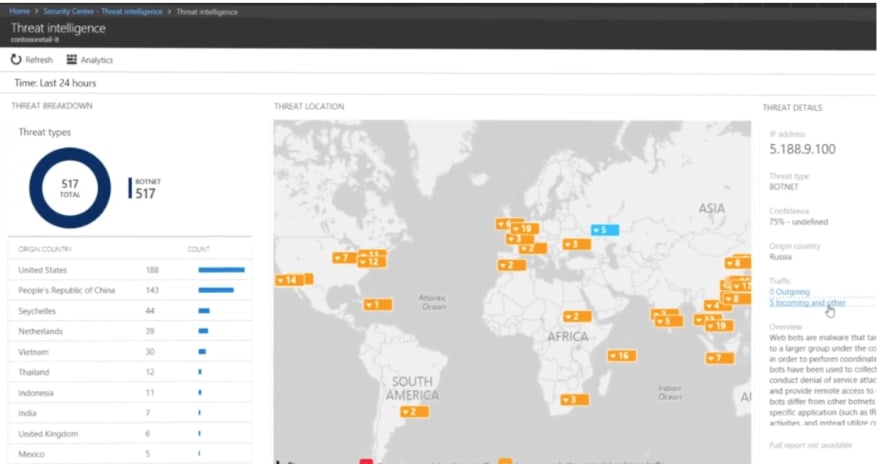
You can even visualize threat intelligence
Threat Intelligence Log Search will show you the tracing for even most trending attack techniques and the geographic regions affected.
Application Protection
Applications are right on top of the data. Therefore, securing applications is a high priority. Maximum attackers are looking to attack applications only. We can do below things to protect our applications
- SSL/TLS, HTTPS
- Single Sign On
- Application integrity ( adhering to the policies like following NIST guidelines )
- Vulnerability Scans
Applications installed or used in Azure cloud for accessing and presenting data. Application securities are governed through data, Virtual Machines or compute (IaaS) and platform (PaaS) services in Azure. Web applications can use azure Managed Service Identities to streamline secure communications with other services in Azure connected to Azure Active Directory.
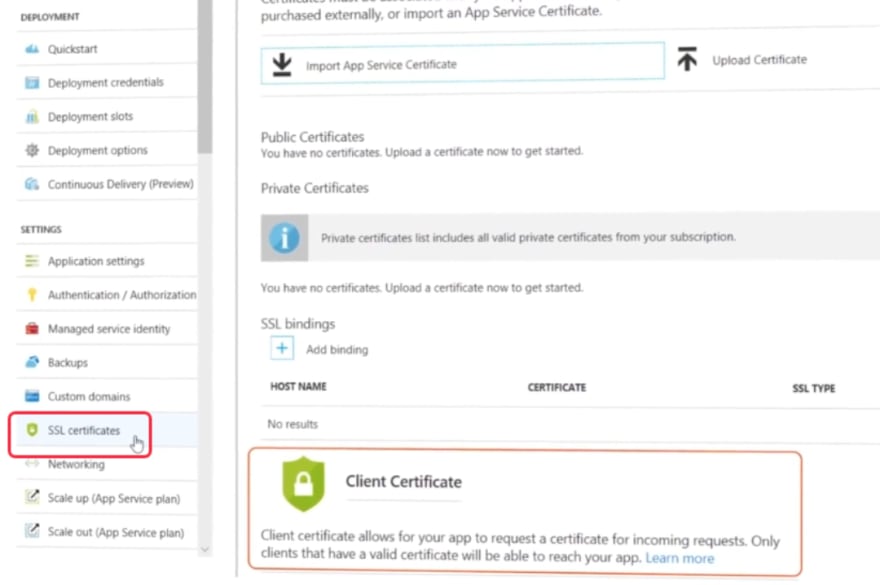
For your applications to make your data-in-transit encrypted you must enable SSL/TLS. From Azure Web apps you can manage SSL certificates and your app can request a valid certificate for all incoming requests.
Data Protection
Data protection is the most critical thing. Because it is at the core of your applications and services layer. You must secure your data at rest and in-transit. You can use encrypted volumes to get protected by underline infrastructure.
Regardless of structured or unstructured data their protection is built-in out of the box over Azure cloud.
Structured Data Protection
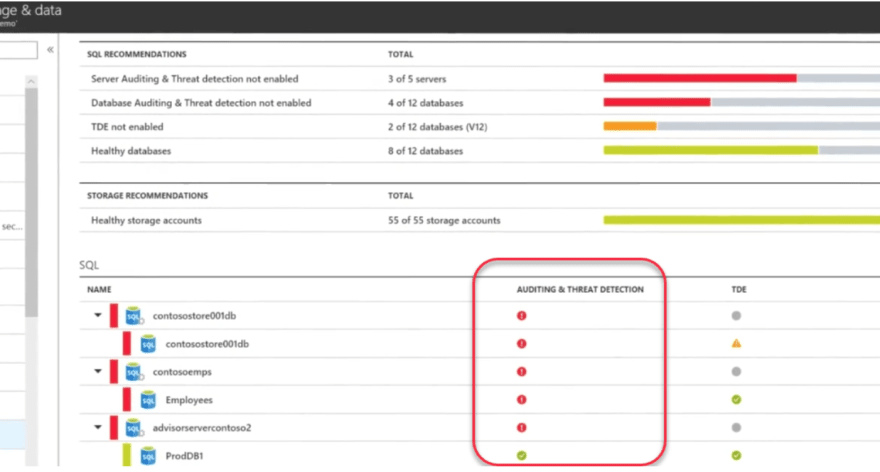
For structured data, all data is encrypted at rest. And you can use machine learning already built-in Azure security center to proactively look for and alert you on potential security vulnerabilities.
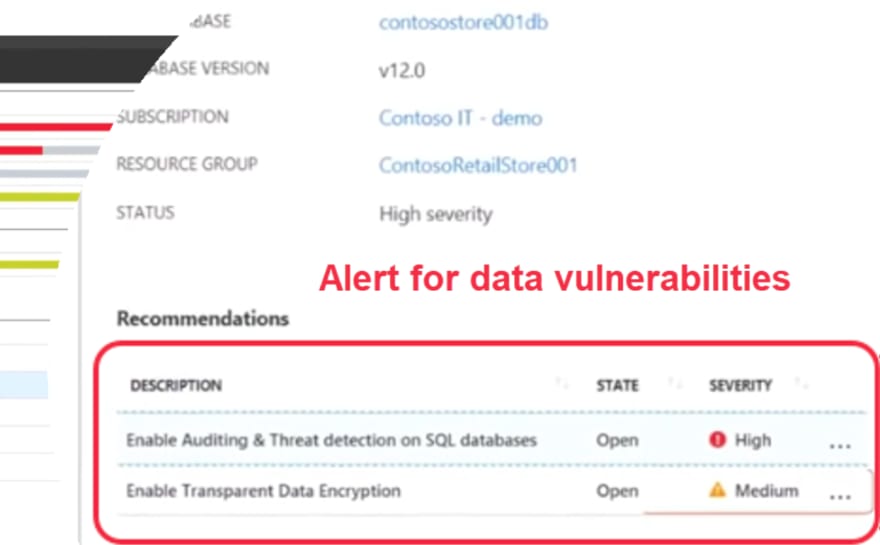
- Enable Auditing & Threat detection on SQL databases
- Enable Transparent Data encryption
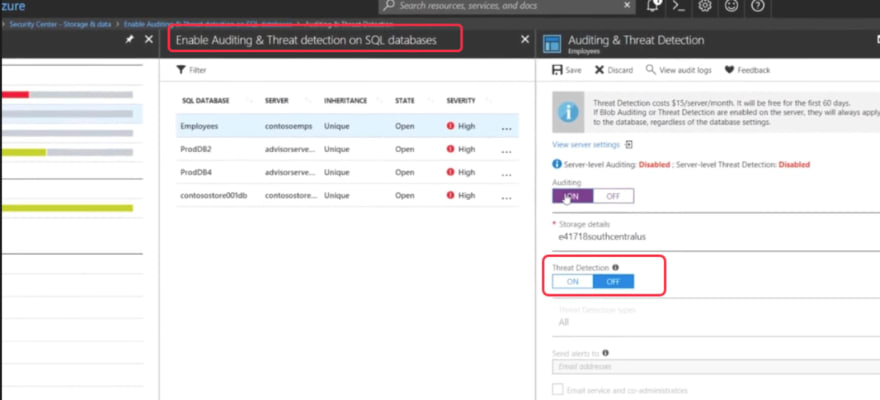
In SQL server which stores structured relational data. You can enable threat detection on database level or entire server level. Threat detection can be related to data encryption, enabling in-security telemetry.
In the SQL Database service itself there is vulnerability assessment where you can get extensive capabilities to recommend and enable sensitive information discovery and classification.
Azure SQL database service does dynamic data masks to obscure data fields and more.
Database service just needs to enable these threat protection then Azure security Center will alert you for any vulnerabilities found.
Non Structured Data Protection
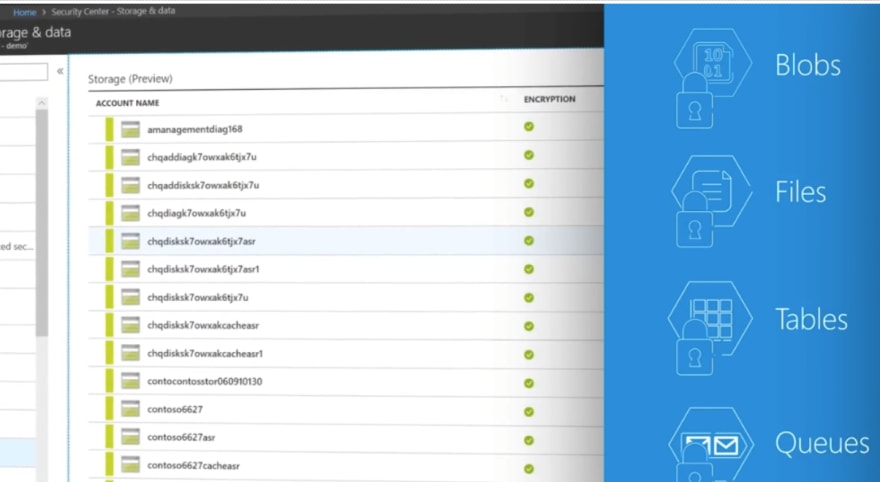
Non structured data like blobs, files, tables and queues are also encrypted at rest in azure cloud and each account is geo-redundant.
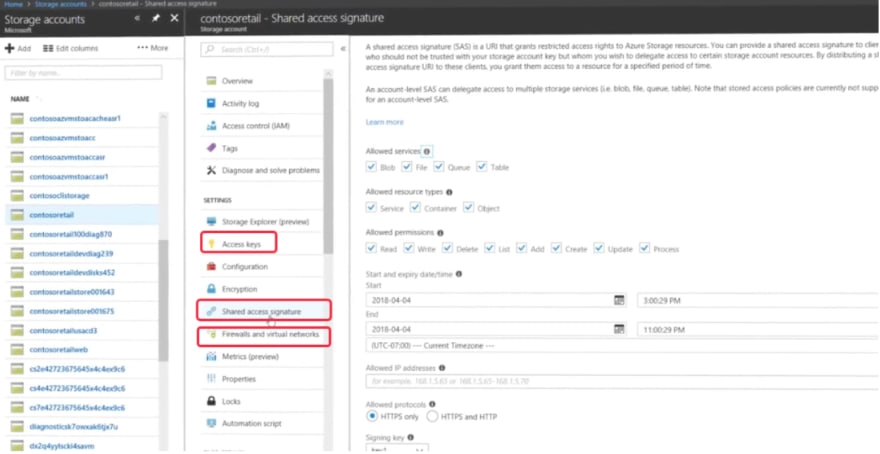
You can use access keys to control authentication, Shared access signature for secure delegate access and granular firewall controls to restrict public network access.
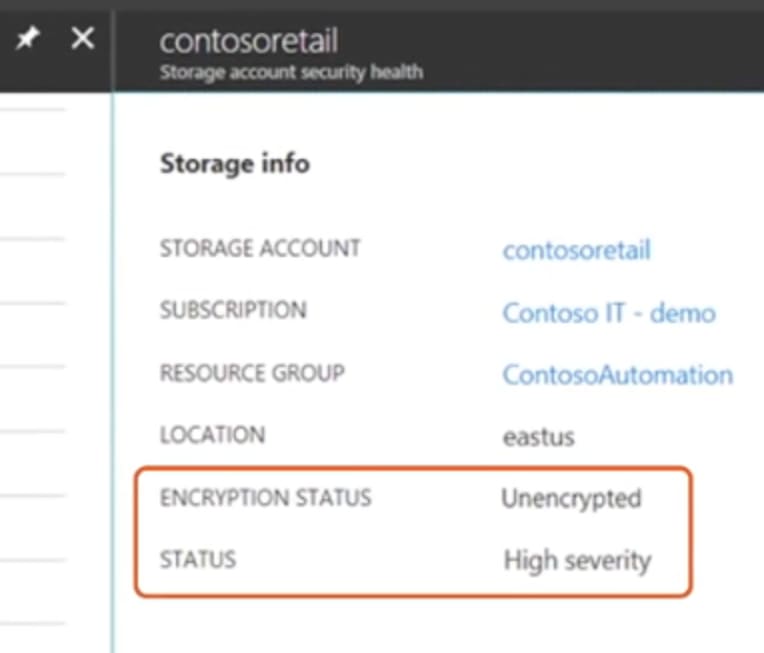
Azure Security Center will report its findings whenever security at risk or protections are disabled by your admin.
Summary
The idea behind the defense in depth approach is to defend a system against any particular attack using several independent methods. Defense in depth is in-built in Azure cloud and it facilitates keeping the security in multiple layers of your architecture. I am also sure the same kind of facilities are available in other cloud environments like in Amazon AWS & Google Cloud. So it’s a matter of awareness and making your cloud secure by properly utilizing the services given by you cloud provider.
Thanks for reading my article till end. I hope you learned something special today. If you enjoyed this article then please share to your friends and if you have suggestions or thoughts to share with me then please write in the comment box.
💖 Say 👋 to me!
Rupesh Tiwari
Founder of Fullstack Master
Email: rupesh.tiwari.info@gmail.com
Website: RupeshTiwari.com
























Top comments (1)
Azure is too expensive, difficult to work with, and has weak technical support. I switched from them to G-core labs, and connected a VM and DDoS protection, all of this comes out to be cheaper by $150 per month than Azure services. And the sup is available in an online chat, and not through stupid contact forms. It's crazy to wait several days for answers from support, Microsoft can work better with their capital.