👾 Ransomware attacks are among the most profitable for criminals and remain the most prominent malware threat today.
As digital assets increase in value (in some cases, being the most valuable assets a company owns), threats become more profitable to criminals too. The largest ransomware payout made by an insurance company ($40 million) to date happened in 2021, and the trend doesn’t show any signs of slowing down.
The major problem with attacks like these is that computers today are so fast and interconnected that malware can harness those resources to spread itself throughout the network and encrypt an enormous amount of files before the victim can respond.
Unfortunately, after the files have been encrypted, there is not much that can be done. Most modern ransomware has good, or at least good-enough implementation of encryption algorithms, all but guaranteeing that the victim won’t be able to recover their data.
How Ransomware Works
The first versions of ransomware were poorly implemented, and the victim stood a decent chance of recovering their files without paying the ransom.
Since the virus had to encrypt the victim’s files as fast as possible to increase the chances of a successful attack, it relied on a symmetric cipher, such as AES, as they encrypt data much faster than asymmetric ciphers.
The problem is that symmetric ciphers use the same key to encrypt and decrypt the files.
Symmetric cipher encryption
The bad actor would have to hard code the key into the malware and hope that the victim wouldn’t have the means to look for the keys in the code, or they would have to send a copy to a remote server which they controlled and delete the key on the victim’s computer. Neither option is very good for the attacker.
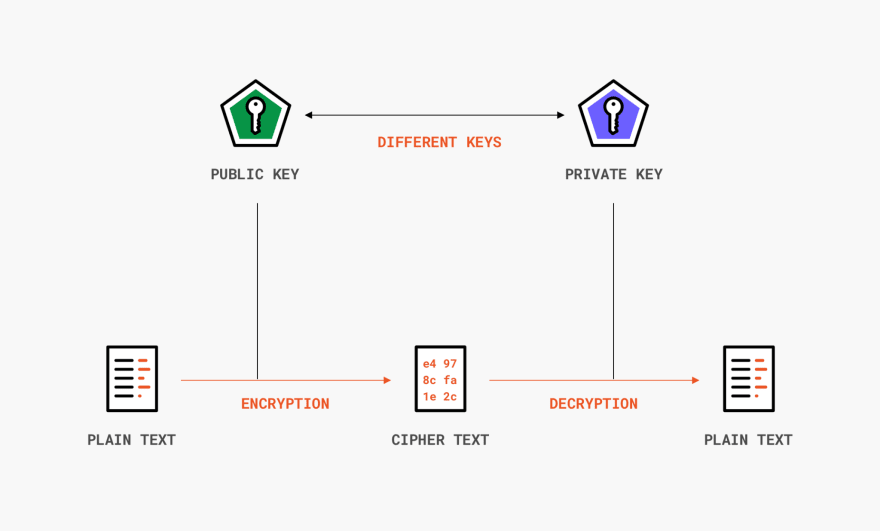
Most modern ransomware uses a hybrid encryption mechanism. While asymmetric ciphers are slow and not meant to encrypt huge amounts of data, using them to encrypt just the encryption key created by a symmetric cipher is not a problem.
Here’s how it works. Before the attack, the attacker generates an asymmetric key pair, and the public key is embedded into the malware. Once the malware is executed, it encrypts the victim’s files with a fast, symmetric cipher, and its key will then be encrypted with the public key from earlier.
To get their files back, the victim would need the attacker’s private key to decrypt the public key to then, finally, decrypt the files using the symmetric cipher key.
Asymmetric cipher encryption
(This is assuming the attacker went through the trouble of providing a way for the victim to get their data back. They could just encrypt everything with AES and delete the key with no intention of ever recovering the data.)
Other than that, the only “realistic” scenario to decrypt the data is by brute-forcing it. I use quotes because it’s not really realistic – we already went over the math behind it. You would need more time than the age of the universe to decrypt AES-128 even if you were using all the computational power available today.
How To Protect Against Ransomware
When it comes to ransomware, the best defense is being proactive instead of reactive. If you got hit by ransomware and didn’t already have a plan in place, your chances of ever recovering your files are slim.
With that in mind, the tips below will help you mitigate some of the risks before something bad happens.







Top comments (0)