Focus on Security, Compliance, Visibility and Permission management to get the best out of cloud while staying safe.
To handle the changing market demands and customer needs, digital transformation is becoming a necessary step for any business to adapt and survive.
Cloud technologies provide various benefits such as:
- Unlimited scalability
- Pay-as-go model(only pay for what you use)
- Ability to create resources within minutes
- Global reach
- Zero downtime with redundancy
- Organization and permission management
This makes Cloud computing one of the greatest catalyst to achieve digital transformation for businesses of any size.
With the need to provide focus towards migration to the cloud, it is also very important to understand how security in the cloud works and how to secure your resources/data in the cloud, you are not safe just by moving to the cloud.
The entire section talks about the business model in the public cloud (AWS, Azure, GCP)
The Security model
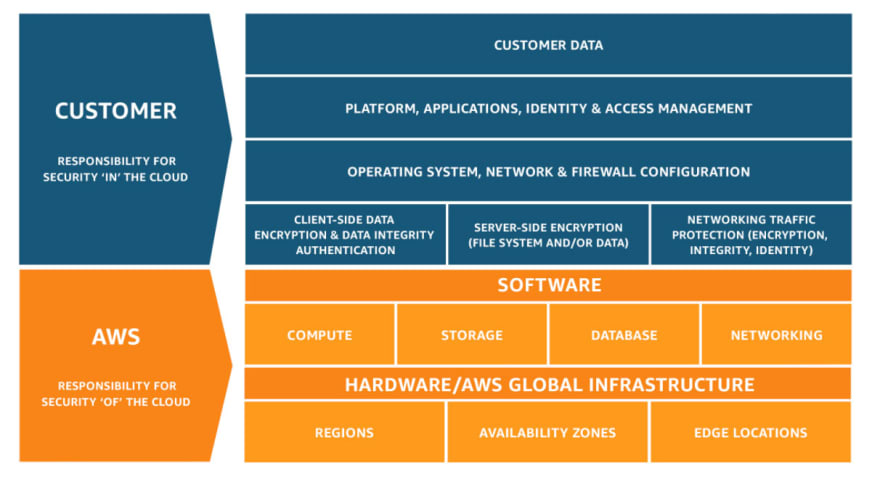
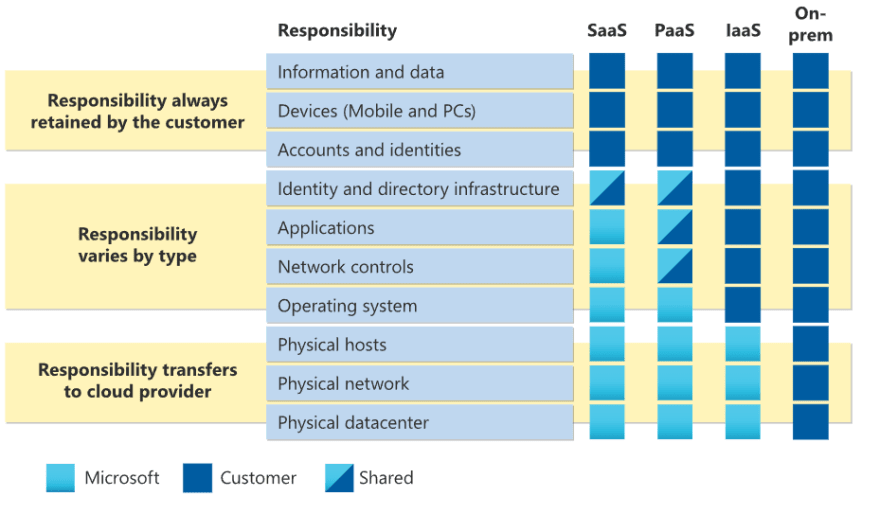
With any public cloud vendor (AWS or Azure or GCP) the Security model is split into two layers Security of the Cloud and Security in the Cloud, usually termed as the shared responsibility model/security model.
The Shared Responsibility model defines the boundaries between what the Cloud vendor promises to safeguard and what the Customer of the Cloud is expected to safeguard.
Security of the Cloud:
Security of the Cloud refers to the Security of components and infrastructure that makes up the cloud
- Security of physical hardware
- Cloud facilities
- Host operating systems
- Network and storage capabilities
- Regions/locations
All of these are protected by the cloud provider with compliance.
Security in the Cloud:
Security in the Cloud refers to the proper and secure usage of services in the Cloud.
The cloud providers do not take responsibility for managing the security in the Cloud, this includes various features such as:
- Access controls
- Permissions
- Software usage
- Firewalls
- Data and encryption
- Storage settings
- Security groups
The ability to perform so much in the cloud also comes with the risk of a single misconfiguration leading to huge loss (such as data leak, hacks, open network etc).

Various organizations have had huge cloud security breach's leading to loss in millions, legal issues, losing their reputation and trust. It is important to take Cloud security as a necessity before its too late.
How to solve the problem
To improve Cloud security, the primary focus should be mainly around:
- Configuration Errors: Misconfigurations in cloud (networking ports, firewall permissions, improper usage of services)
- Visibility and monitoring in the Cloud: monitor and alerting mechanisms to identify and promptly alert any threats and vulnerabilities.
- Permissions and Access management: Least privilege policy, proper onboard/offboarding, permission boundaries.
Understanding & making efforts to ensure Cloud security, visibility, monitoring and access management is a very important step for any business to adapt to the Cloud model.



Top comments (0)