There are over 50+ tools and solutions available in the market for performance testing your application and services. Now it is time to check out Ddosify, high-performance load testing tool which offers free and commercial features to test web applications and services over HTTP(S), HTTP/2, and other protocols are on their way. In this blog article, let us deep-dive into Ddosify tool and see whether it satisfies a typical performance engineer or not.
Before we see Ddosify, let us try to understand the name of the tool. Ddosify contains Ddos term. DDoS stands for Distributed Denial of Services. Below is the Wikipedia entry for Denial of Service:
In computing, a denial-of-service attack is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the Internet.
An attacker targets a machine and tries to disrupt its services. The term distributed stands for multiple sources. Instead of attacking a system from one source, attacker uses multiple sources.
If you try to fit the DDoS capabilities for good intent, you will get Ddosify.
What is Ddosify?
Ddosify is a high-performance load testing tool written in Golang. It comes in two flavors: open-source and commercial.
It supports HTTP(S), HTTP/2 protocols (as of now); other protocols are on the way.
JSON support for creating scenarios.
Supports various workload models.
Getting Started
As Ddosify is Golang based, the prerequisite is to install the latest and stable version of Golang if you want to build from the source, else you can download the binaries to get started. Head to https://golang.org/dl/ to install the Golang.
To install Ddosify, you can leverage Docker or install it from source.
docker run -it --rm ddosify/ddosify
go install -v go.ddosify.com/ddosify@latest
After successful installation, you can verify Ddosify by issuing the below command.
ddosify -versionQuick Start
Let us start a quick load testing, targeting the demo app. I am running a sample Jetty app locally on the port 8080. To begin the testing using Ddosify, you can issue the below command.
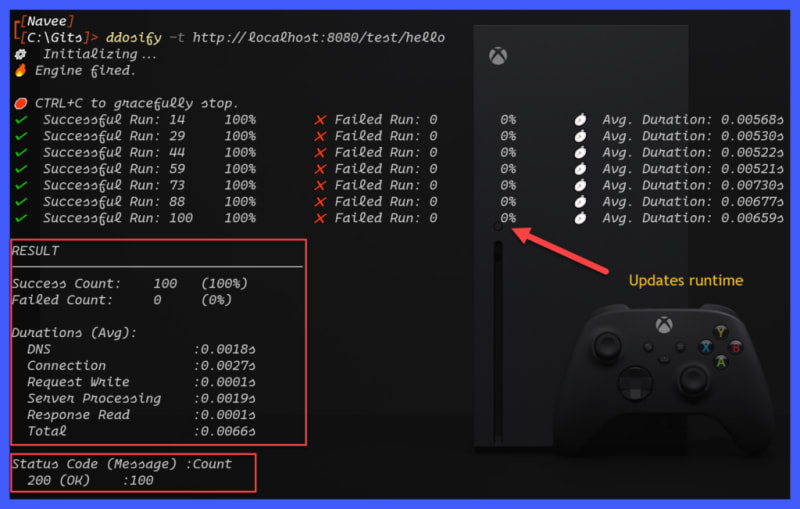
ddosify -t http://localhost:8080/test/helloThe above command sends 100 requests in 10 seconds. Below is the output. During the test, Ddosify displays the status runtime. Once the test is done, it will display the results with DNS, Connection, Request Write, Server Processing, Response Read time and Total time in seconds.
To terminate the test, you can press Ctrl + C.
Scenario Design
Now let us design a quick scenario to test the demo app in JSON. Copy and paste the below JSON and save it as config.json.
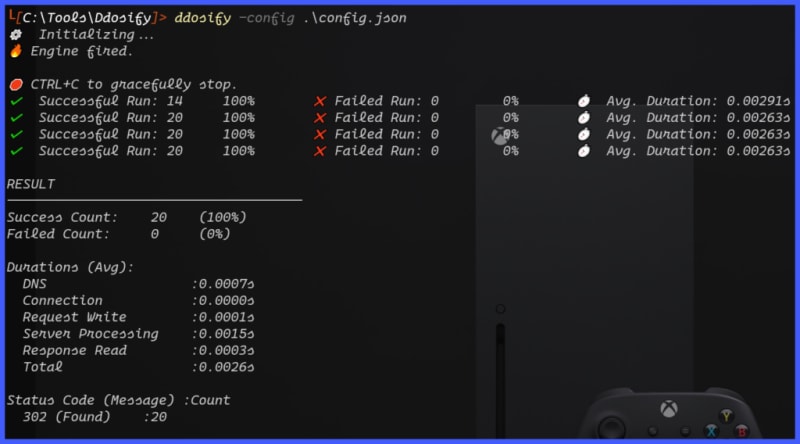
To start the test, issue ddosify -config .\config.json.
{
"request_count": 20,
"load_type": "linear",
"duration": 5,
"output": "stdout",
"steps": [
{
"id": 1,
"url": "http://localhost:8080/test/session/",
"protocol": "http",
"method": "POST",
"headers": {
"ContenType": "application/xml",
"header1": "header2"
},
"payload": "Name=test&Value=test&Action=Set",
"timeout": 3,
"others": {
"keep-alive": true,
"disableCompression": false,
"h2": true,
"disable-redirect": true
}
}
]
}The above scenario throws 20 requests (iterates) over the period of 5 seconds. Below is the output.
Below are the various flags available for Ddosify at this time of writing.
| Flag | Description | Type | Default | Required? |
|---|---|---|---|---|
-t |
Target website URL. Example: https://ddosify.com |
string |
- | Yes |
-n |
Total request count | int |
100 |
No |
-d |
Test duration in seconds. | int |
10 |
No |
-p |
Protocol of the request. Supported protocols are HTTP, HTTPS. HTTP/2 support is only available by using a config file as described. More protocols will be added. | string |
HTTPS |
No |
-m |
Request method. Available methods for HTTP(s) are GET, POST, PUT, DELETE, UPDATE, PATCH |
string |
GET |
No |
-b |
The payload of the network packet. AKA body for the HTTP. | string |
- | No |
-a |
Basic authentication. Usage: -a username:password |
string |
- | No |
-h |
Headers of the request. You can provide multiple headers with multiple -h flag. |
string |
- | No |
-T |
Timeout of the request in seconds. | int |
5 |
No |
-P |
Proxy address as host:port. -P http://user:pass@proxy_host.com:port' |
string |
- | No |
-o |
Test result output destination. Other output types will be added. | string |
stdout |
No |
-l |
Type of the load test. Ddosify supports 3 load types. |
string |
linear |
No |
-config |
Config File of the load test. |
string |
- | No |
-version |
Prints version, git commit, built date (utc), go information and quit | - | - | No |
Workload Models
At this moment, Ddosify supports three workload models: Linear, Incremental, and Waved.
Linear helps to inject the load consistently over the period of time.
Incremental injects the load gradually increasing.
The wave pattern injects the load like peaks and valleys.
How many requests you can send from your system?
To determine, how many requests you can generate on the system, purely depends on the CPU, memory, and other parameters. You need to run benchmark tests and conclude your findings.
I have two cores with 16 GB RAM. Golang is based on a lightweight thread managed by Go runtime called goroutines. Golang has better concurrency than other languages. You can easily spin up hundreds of threads using minimal resources.
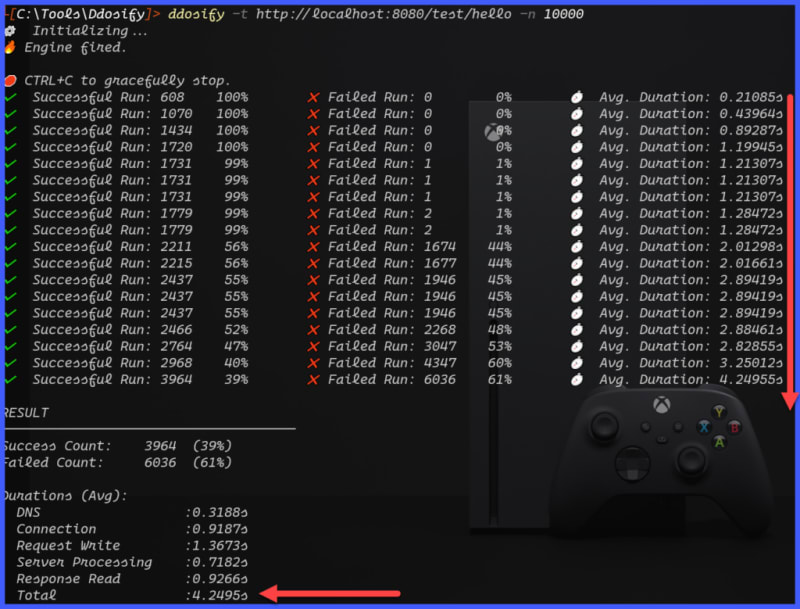
I executed a test with 10000 requests. As you see, the load is proportional to the time.
When I injected with 10000000, I observed high CPU and memory on ddosify.exe and the test took a long time to complete. I have to terminate the exe file. It is not DDosify issue, it is my system configuration. I have an under-powered config which cannot be useful for running very high load.
Overall
Ddosify might be a good fit if you want to run a very high load quickly with minimal configuration. It is still in the very early stages, and a lot of features are missing (parameterization, logical actions, scripting to name a few). The commercial version is yet to be released.; I am on the waiting list. I hope Ddosify team will develop the features which will satisfy typical performance engineers eventually. I urge you to try Ddosify to ddosify your app.




Top comments (0)