Recently, one of my colleagues invited me to an AWS live stream talk she was giving about building secure GraphQL APIs, using Auth0. She’s been doing a number of these AWS events of late – both live stream and in-person – and as this one was going to essentially be on the topic of Delegated Authorization, she asked me to come along and share some of my experience from an Auth0 perspective 😎
Auth0 – the SaaS platform that powers the Okta Customer Identity Cloud – is a great example of an off-the-shelf OAuth 2.0 Authorization Server. It isn’t the only one that’s out there, for sure, but it is one that I’ve been working with for more than 5 years now to deliver real value for developers 😄 In the context of OAuth 2.0, an (OAuth 2.0) Authorization Server is the thing that fundamentally enables a large part of the workflow behind Delegated Authorization.
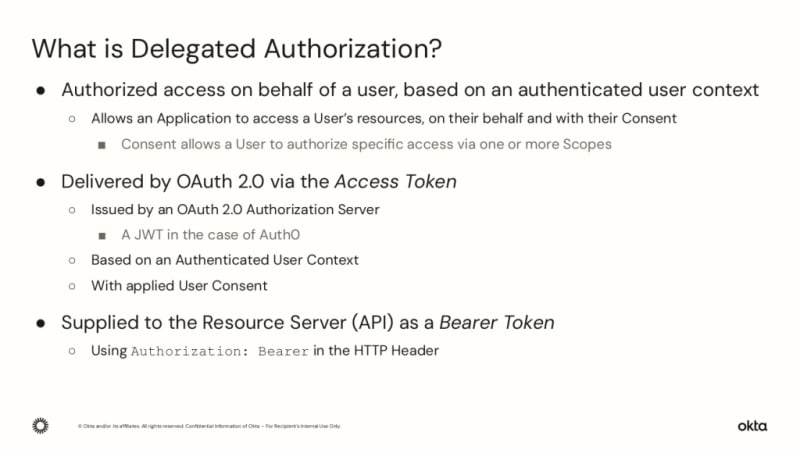
What is Delegated Authorization?
Delegated Authorization is a mechanism that allows a third-party application to act on behalf of a user when accessing the protected resources for that user (typically via an API). Delegated Authorization also introduces the notion of Consent, where a user agrees to the Scope of access an application desires. In the case of OAuth 2.0, Delegated Authorization results in the generation of an Access Token which is typically consumed by an API as a Bearer Token. And an Access Token is typically generated by the Authorization Server upon successful verification of a users’ credentials (et al), using one of a number of “flows” – the most common being Authorization Code Flow and Authorization Code Flow with PKCE. You can discover more about Delegated Authorization, and what Auth0 provides to support this, at https://a0.to/do/apiz.
The thing wot we presented
I decided to present on three topics related to securing API access: Delegated Authorization, obviously, Attack Protection and Access Control; the latter I sub-divided into Role Based Access Control and Relationship Based Access Control. You can discover more about each of those other topics at https://a0.to/do/protect, https://a0.to/do/rbac and https://a0.to/do/fga respectively. Below are some screenshots of the slides I used as part of my presentation 😊
If you missed us live, then you can always catch our recording here on Twitch TV. I would highly recommend it, as my colleague – Pradheepa – goes into a really good demo of using both AWS AppSync and Amazon Bedrock! She definitely does the much more exciting part of the show! 😂
This was my first live-stream with AWS, and it was great fun to be part of. In fact, it was my first live-stream in quite some time! It’s always a pleasure working with Pradheepa, and Stuart – the show host from AWS – did a fantastic job at putting everyone at ease and setting the tone for the whole piece. I hope to do more of these in the near future, and from this one I will take away the following “fun” fact: I really need to invest in a better mic! 🤦🏻♂️
I hope you enjoy the recording, and I also hope you have a very enjoyable time over the festive season wherever you are 🤗






Top comments (0)