This is a reviewed version of the same previously published article on my medium page
To allow an API Gateway to upload files directly to S3, you need to create an IAM role that can be assumed by the API Gateway and has the necessary permissions to write objects to S3.
Step 1: Create the IAM Role
- Open the IAM service in your AWS console.
- Navigate to “Roles” and click “Create role.”
- Select “AWS service” under “Trusted entity type,” then choose “API Gateway” under “Use cases for other AWS services.”
- Click “Next” to proceed.

Step 2: Set Permissions for the Role
- After creating the role, name it (e.g., “api-gateway-s3-upload”) and click “Create role.”
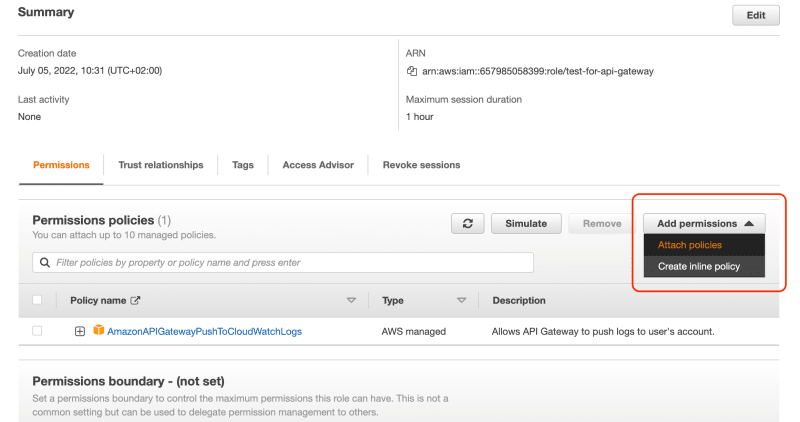
- To add permissions, open the newly created role from the IAM Roles list.
- Under the “Permissions” tab, click “Add permissions” -> “Attach policies.”
- Filter by “S3” and select AmazonS3FullAccess.

Note: While AmazonS3FullAccess grants full S3 access, it does not adhere to the principle of least privilege. Consider creating a custom policy that only allows the
PutObjectaction on the specific S3 bucket.
Step 3: Fine-Tuning the Permissions
To ensure compliance with the least privilege principle:
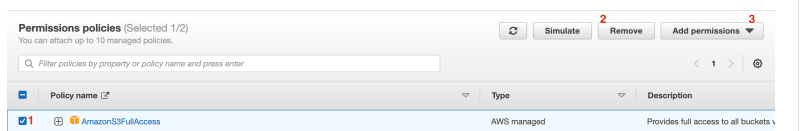
- Remove the AmazonS3FullAccess policy by selecting it and clicking “Remove.”
- Add a new inline policy by clicking “Add Permissions” -> “Create inline policy.”
-
In the JSON tab, insert the following policy:
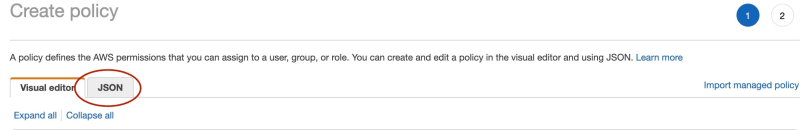
{ "Version": "2012-10-17", "Statement": [{ "Effect": "Allow", "Action": "s3:PutObject", "Resource": "arn:aws:s3:::your-bucket-name/*" }] } Review the policy, assign it a unique name, and create it.
Conclusion
You've successfully created an IAM role with a custom policy that allows API Gateway to upload files to S3 securely. In the next part of this series, we'll explore how to configure an API that leverages this role for S3 operations.





Top comments (0)