Reflecting on the technological advancements of 2023, it was a remarkable year for software developers. Notably, the introduction of tools like Co-pilot has exponentially expedited development speed, while AI agents and vector databases have been effectively processing massive amounts of data for meaningful insights. Moreover, frontend clouds have revolutionized the deployment process, enabling full-stack applications to be launched in mere minutes.
Building on these advancements, our prediction for 2024 is a continued focus on security and reliability. Specifically, we forecast the implementation of robust features that will secure and support the evolution of these remarkable trends into our applications.
In the following article, we will delve into one of the most fundamental areas in user experience and security, access control, and find the five new features we should implement in 2024 to benefit the most from the amazing capabilities of applications nowadays.
Passkeys Authentication
Passwords have not been considered a secure method to verify identities for many years now. Not only have brute-force techniques become easy to apply even for complex passwords with modern methodologies, but the nature of users using one key for all their applications also makes it a bad pattern for secure applications.
Over the last decade, Multi-Factor Authentication (MFA) has attempted to address the security issues associated with passwords by requiring users to verify their identity using an additional factor. While MFA initially held great promise, by 2023, MFA fatigue attacks had become a significant attack surface, and MFA was no longer considered the most secure method.
Besides the security issues, passwords with MFA are also considered a bad user experience. They need to remember multiple passwords (or have weak security), insert them many times, and use a device as another factor for authentication. Passkeys authenticate users with a method that proves their identity with biometrics or physical devices.
In 2023, WebAuthn, an open standard for passkeys and biometric authentication, was adopted by all the main application platforms, including all modern browsers and mobile devices. The WebAuthn standard paved the way for every application developer to adopt passkeys as an authentication method.
Using open-source tools like Hanko.io can help you implement passkeys into any application in a matter of minutes. With WebAuthn and Hanko, you can ensure your application provides an amazing and secure experience for all your users in 2024.
Fine-Grained Authorization
The amount of data we process in our applications is growing exponentially every day. One of the challenges with data of any size is managing who can perform operations on it, or in other words, authorizing users in our applications.
The complexity of authorization with large amounts of data has two aspects
- From the decision-making perspective, much more data is involved in our decisions. For example, to decide the permissions of a subset of data, we need to consider the time it was created, the users who are related to it, and more. All of that makes authorization decisions more complex than ever.
- From the permissions perspective, we need to obtain high granularity on the permission levels we get on the data. For example, we want to give someone access to file metadata, but not to its content.
While the traditional Role-Based Access Control (RBAC) used to be the de-facto authorization capability of applications, the amount of data and the challenges we encounter cannot fit into the simple roles we assign to users. This is where Fine-Grained authorization comes into the picture.
Fine-grained authorization combines advanced approaches such as Relationship-Based Access Control (ReBAC) and Attribute Based Access Control (ABAC) to provide the granularity that modern applications with complex data deserve.
Please Support Us
If you find this post helpful,please give OPAL a star on GitHub! Your support helps us make access control easier and motivates us to write more articles like this one.
For example, ReBAC leverages the relationships between data entities to evolve the static RBAC model into a dynamic one, deriving permissions between entities. In ABAC, we use data attributes to construct conditions that enable detailed decision-making for authorization.
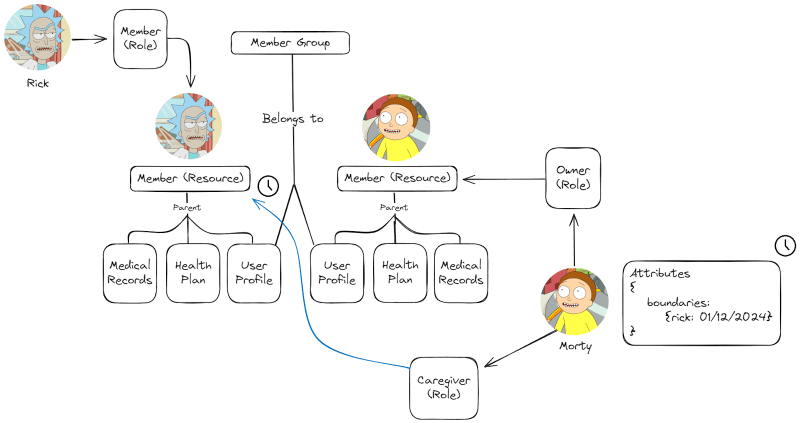
Example of RBAC/ABAC/ReBAC usage in one healthcare permissions model 👇🏻
Implementing fine-grained authorization has become essential for every application, and you should prioritize it in 2024.
Decouple Policy from Code
The most trending cloud-native field in 2023 was the "frontend" cloud. Services for edge computing, such as Vercel Edge and Railway, provide an efficient way for developers to deploy comprehensive full-stack web applications to a fully managed cloud environment in record time. This trend is simply a continuation of our application's nature to exist in small, autonomous environments, separate from each other.
While the separation of concerns and modern distributed architectures are great for rapid development, it's challenging to ensure our security standards are streamlined across all applications. To assist with the authorization aspect, we need to decouple policy from code.
In the decoupling pattern, instead of using imperative code to write authorization conditions in the application code, we use dedicated languages or standards to declare centralized policy rules in one policy store. All the distributed applications enforce their permissions using these streamlined policy rules.
Another approach that has been gaining traction lately is using policy as a graph. This is similar to the concept of Policy as Code, but incorporates a graph DB into the mix. This graph DB contains all the nodes as resources and users, while the edges determine the dynamic permission derivations. This approach is primarily relevant to the ReBAC model we discussed earlier.
In 2023, AWS announced its first application policy language, Cedar, which paved the way for giants to join the party and use the decoupling pattern as the best practice for application authorization. Cedar allows application developers to adopt Policy as Code and implement fine-grained authorization into their applications without the hassle of creating complex policies.
Here's an example of how Cedar code combines RBAC and ABAC. 👇🏻
permit(
principal in Role::"writer",
action in [Action::"post", Action::"put"],
resource in ResourceType::"article"
) when { principal.karma > 1000 || (context has published && context.published == false) }
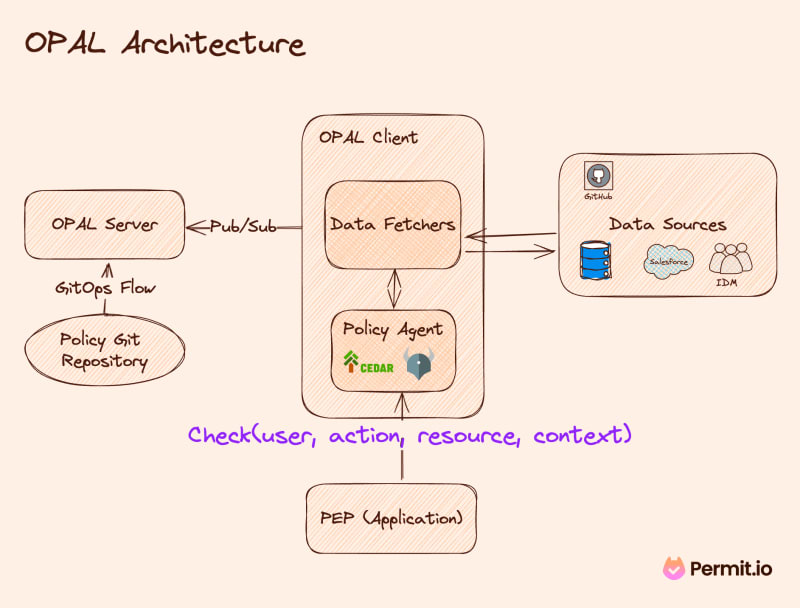
Another tool that can help you deploy a Policy as Code-based solution in 2024 is OPAL, the Open Policy Administration Layer. OPAL is an open-source project that provides a comprehensive policy-based service for applications. With one click, you can deploy a full architecture of a Git-based centralized policy store with decentralized policy engines running as a sidecar with your applications. OPAL also provides a unified architecture to sync all the data you need with the policy engines.
Better Audit Logs
2023 was a year of diversity, not only in the workforce but also in our application identities. Besides users, our application now has access to many computer-based identities, such as AI agents, bots, and more. Even our application code is accessible by co-pilots, CI/CD automation, etc.
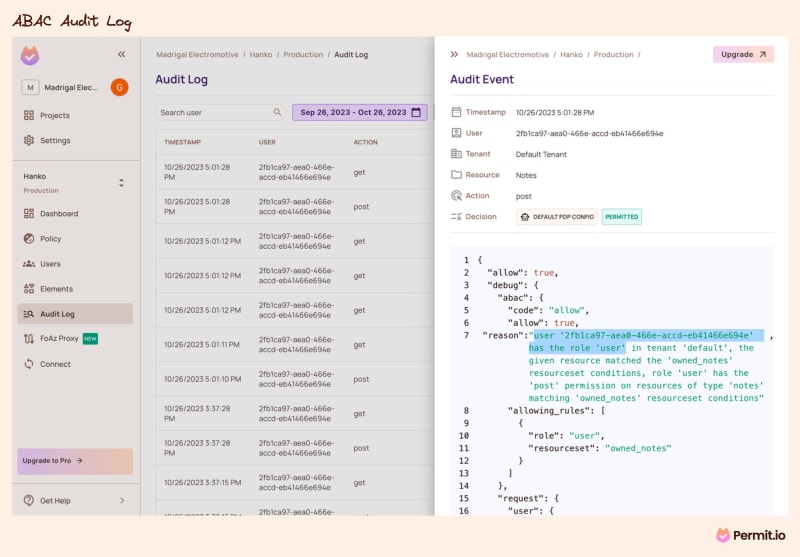
A fundamental requirement for stable access control is audit logs, often referred to as the recurring this.audit({…}) code snippet that should be placed wherever an authorization decision occurs. Given the diversity of identities accessing our applications, these logs require special attention. We must ensure that at any given time, we can precisely audit who has access to which resource in our applications.
Modern policy engines and policy-as-code architectures solve many aspects of audit log challenges. First, they allow developers to define a single location where all the authorization audit logs are logged. Second, since all the policy rules are configured in the same way, the logs can provide much more data with no extra effort.
Besides that, Policy as Code architectures provide logging of all the changes in authorization. It starts with configuration changes that are logged in the same format, continues with versions and data updates, and then the application decisions themselves.
Using a policy-as-code system can provide you with what you need to start improving audit logs in your applications in 2024.
Approval Flows
In the early days of applications, permissions were only in a Mandatory Access Control (MAC) model, which meant the application developer was the only one to assign permissions to users. The modern web replaces MAC with Discretionary Access Control (DAC), which allows users to assign permissions to themselves and to other users.
The rise of AI and cloud-native architectures in 2023 pushed the DAC to a new limit. Users now need to assign permissions for scopes of data that are unknown to the application developer. For example, users now want the ability to give access to third-party AI applications that are unknown to developers, and they want to define the scope of the data to which they are allowing access. The best way to deal with this is through policy-based approval flows.
In a well-structured approval flow, the developer defines the tasks or the flow of permissions in the form of request → approve (or partial approve) → policy change. Using policy as code, this configuration is not coupled to a particular configuration or data. For example, a developer defines a method for users to approve other users to access their data by dynamically generating new policy rules into the policy engine.
In our work in 2023, we found that Approval Flows are one of the most requested features by our users for their applications. Our perspective is that 2024 will be full of ideas and work around defining and designing smart approval flows for applications.
Conclusion
The list you just read summarizes the work we did at Permit.io with Application Developers in 2023. As the leader in end-to-end solutions for application authorization as a service, we have experience with various types of applications and engineering teams around authorization and access control.
If you plan to implement improved access control in your application in 2023, we encourage you to open a free account on the Permit.io platform and try our solutions for fine-grained authorization. Our service is based on policy-as-code and a decentralized architecture, and our audit logs are industry-leading.
In the meantime, you can join our Authorization Slack community, where we chat and collaborate on day-to-day access control challenges. See you there.









Top comments (0)