One question students frequently ask at the beginning of their cybersecurity learning journey is: how are hackers able to break into a system or network? The simple answer is that hackers and other threat actors look for vulnerabilities on a target system. A vulnerability is a security weakness or flaw in a system that could be exploited by a threat. The competition between security researchers and hackers is an ongoing one — a race to discover security flaws first. Security researchers are always looking for new vulnerabilities to help software and product vendors to fix and close security weaknesses, while hackers are looking to exploit and gain access to their victims' systems.
Tip
Nessus is one of the most popular vulnerability assessment tools within the cybersecurity industry. Further information on Nessus can be found at https://www.tenable.com/products/nessus.
A vulnerability may take the form of a weakness or flaw in a configuration, security policy, or even something technological in nature. For example, a network device such as a router is configured to use Telnet and not SSH as the preferred method for remote access management. Telnet is an unsecured protocol that transfers data in plaintext whereas SSH encrypts all traffic. TCP/IP is the language all devices speak when connected to an Ethernet network, so you may think the TCP/IP protocol suite offers good security. In reality, however, this is not necessarily the case.
Many vulnerabilities exist in the various protocols within TCP/IP. Those protocols include Internet Protocol (IP), Internet Control Message Protocol (ICMP), Hypertext Transfer Protocol (HTTP), and even Simple Network Management Protocol (SNMP). If the IP was not designed with good security, an attacker can simply spoof the IP address of another device on the network. SNMPv1 does not support user authentication, so this means an attacker is able to remotely connect to an SNMP-enabled device and gather sensitive information. Attackers can take advantage of various weaknesses within these protocols and capture sensitive information while network traffic is traveling along a network.
Hackers are always looking for a way inside your network and devices, and your network components provide an easy way in if they are not updated and secured properly.
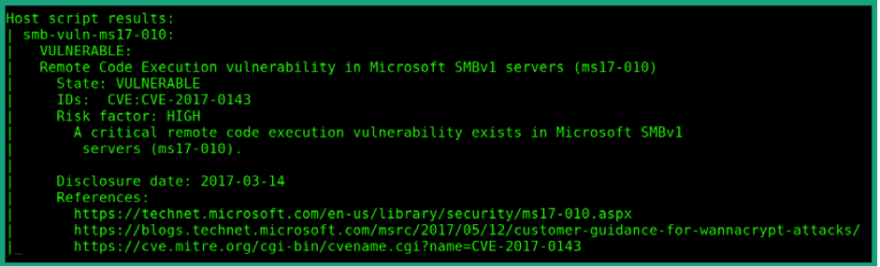
The following screenshot shows the NMap tool, which has found the EternalBlue vulnerability on a Windows system:
In this screenshot, NMap reports that the target system is vulnerable to the EternalBlue exploit, which will allow an attacker to exploit the vulnerability in Server Message Block (SMB) version 1 to execute remote code. Furthermore, NMap reports that the risk on the target is high, and it provides reference URLs for additional research.
Also, some enterprise network devices such as routers and switches support network security functions to help prevent various malicious threats and attacks on your network. Sometimes, a misconfiguration on a router can give an attacker remote access into the management pane of the device.
Each device requires a firmware or an operating system in order to work and perform its functions. Operating system vendors are always researching for vulnerabilities within their products, so that they can quickly release updates and security patches that fix any issues for their customers. Many organizations do not update their computers' operating systems for many months, however, and this increases the risk of their being compromised. Imagine if a new threat came about and the operating system vendor released a security patch to fix the issues but the organization ignored the updates and patches by the vendor; their systems would be vulnerable to the threat until security patching occurred on their network. Remember, every day hackers are looking for ways into your systems; operating system vendors release updates very frequently in order to help protect you.
Many configuration vulnerabilities exist on networks. They can exist within user account management, network services configuration, and default device configurations. When logging in to a system, your user credentials may be sent across the network via an unsecured protocol.
The following screenshot shows that a Windows user credential was captured as it was sent to the Active Directory server on the network:
Figure 2 – User account details

In the preceding screenshot, we can see that user Bob has entered his username and password on a Windows 10 system to authenticate himself on the network. However, in this scenario, the Active Directory server (Windows Server) is using the default directory query protocol, Lightweight Directory Access Protocol (LDAP). LDAP does not encrypt user information by default; only the user's password is hashed, using NTLMv2, and sent across the network. In the preceding screenshot, the hash was captured, allowing the attacker to perform offline decryption of the hash to retrieve Bob's password. This is an example of an unsecured user account and insecure protocols on a network.
Configuration vulnerabilities also exist when an administrator configures weak or insecure passwords for user accounts. Such vulnerability enables a hacker to easily compromise user accounts and quickly gain access. Another vulnerability occurs if default configurations are used on a system or network device. Default configurations are applied on a device at the point it leaves the manufacturer; they allow us to easily get the device up and working quickly without having to spend too much time trying to figure out how to get it working. Default configurations often contain many configuration weaknesses, such as security features being absent and remote access being enabled for all. It's important to ensure that default configurations are never used on systems and devices on a production network.
Human vulnerabilities
One major vulnerability we often overlook when designing a secure network is the human factor. Humans are also vulnerable to various online and offline cyber-attacks, such as so-called social engineering attacks. Social engineering is simply when an attacker is able to manipulate a person to reveal sensitive information or perform a certain task.
Important note
Social engineering is usually non-technical in nature. This means a computer is not required to perform various types of social engineering attacks on a victim. The attack usually exploits the trust and social behavior of the victim.
The following are various types of cyber-attack that target human vulnerabilities:
• Phishing is a form of social engineering carried out using a computer; the attacker creates and sends a fake email to a potential victim. The email is crafted to look and sound as if it comes from a legitimate source, such as a financial institution. The message usually contains some instructions and a malicious link embedded in the message. The instructions might say, Your user account has been hacked; click the following link to reset it. If the user follows these instructions, they'll end up downloading malware and infecting the system, visiting a site that allows the attacker to capture the victim's username and password.
• Another type of social engineering is spear phishing. In a spear phishing attack, the attacker makes a fake message or email look more legitimate and believable. This type of attack is usually focused on a specific group of people. An example would be an attacker who crafts an email that looks like it originates from Bank X and sends it to everyone associated with that bank. People who have an account with Bank X will be more susceptible to the scam, click any malicious links, or follow any instructions with the message whereas a person who does not have an account with Bank X will simply block, delete, or ignore the message.
• Whaling is a type of phishing attack that focuses on high-profile people within an organization, such as the CEO or a director. The objective of the attack is to compromise a high-profile person's account and use the account to conduct transactions. Imagine if the CEO's email account were compromised: the attacker could send emails to the accounting department requesting confidential financial details about the organization. People within the accounting department would see the email as originating from the CEO and therefore trust it to be the actual CEO requesting the information. In such an attack, trust between the employee and the CEO is being exploited.
• Social engineering attacks can be carried out during a telephone conversation—this is known as vishing. In vishing, the attacker calls the potential victim while pretending to be someone with authority or a person the victim may trust. During the conversation, the attacker may also try to build or improve the trust between the victim and the attacker and take advantage of that trust. In vishing attacks, the attacker may pretend to be calling from the victim's bank and request the victim's online banking user credentials, or perhaps request their credit card number and pin.
• Social engineering can also be done using Short Message Service (SMS), a form of attack known as smishing. This is when an attacker attempts to perform social engineering using the text messaging service on mobile phones.
• Sometimes an attacker will take a more aggressive approach to getting victims to visit a compromised website. Hackers are able to compromise vulnerable Domain Name System (DNS) servers and can modify the DNS records, for example, by changing the DNS A record for a hostname to point to a compromised website rather than the legitimate IP address. This means that any device requesting the IP address of a certain website will be redirected to a malicious website. This type of social engineering is known as pharming.
• It is important to build a fortress around and within your organization to protect it from both internal and external cyber-attacks and threats. Sometimes, when an attacker realizes he/she is unable to compromise the target's network, the attacker may attempt to perform a waterhole attack. In a waterhole attack, the attacker will attempt to compromise a site or location that the employees of the target organization are known to commonly visit, such as a local coffee shop. By compromising the coffee shop Wi-Fi network, any device connected to that network will download a payload and become infected. When an employee connects their infected mobile device to the corporate network, it will compromise the organization. However, anyone who connects to the Wi-Fi network, or the waterhole, will be infected, not just the target users who belong to the organization.
Next let's learn about password vulnerabilities and management.
Password vulnerabilities and management
To prove our identity to a system, we must provide a valid username and password. People often create simple and easy-to-remember passwords for their online accounts. While these are simple to remember, a simple password is a security vulnerability which may allow a hacker to gain access to the victim's account. Creating a secure and complex password is important and prevents hackers and other threat actors from compromising user accounts and gaining access to sensitive information.
When creating secure and complex passwords, follow the following guidelines:
• Passwords should at least 8 characters in length.
• Ensure that the password includes a combination of uppercase and lowercase letters, numbers, special characters, and symbols.
• Ensure the password is not used on another account you own.
• Passwords should not be regular words you would find in the dictionary.
• Passwords should not contain personal details such as birthdays or relative names.
• Passwords should be changed frequently.
• Passwords should not be written down anywhere around the workplace.
Using a password manager can help you to create, store, and manage secure passwords. There are many free password managers available on the internet.
The following screenshot shows a secure password generated by the LastPass password manager:
Passwords are still breakable by a hacker who has a lot of time and computing power. Using Multifactor Authentication (MFA) adds an extra layer of security to our user accounts; the user has to provide multiple sets of information to prove his/her identity.
Sometimes, after a username and password combination has been validated by a system, it requests a second form of authentication to validate your identity. This is sometimes referred to as 2-Factor Authentication (2FA). Authenticator apps on your smartphone can be associated with a supported website. Cisco is an example of this. Its user accounts support 2FA, which allows you to add a third-party authenticator, such as Google Authenticator, on your Cisco user account. Each time you attempt to log in to the Cisco website, a unique code is required from the authenticator app. This code changes approximately every 30 seconds, making it difficult for a hacker to guess the sequence of codes being generated each time.
Rather than using passwords, you can use biometrics. Biometrics allows you to use a part of your body to authenticate to a system. Most new smartphones support biometric authentication, which allows a person to unlock their smartphone using their fingerprint. On Microsoft Windows 10, Windows Hello uses facial recognition technology.
Note
Other forms of biometrics are voice, iris, and retina scans.
Digital certificates are an alternative method to authenticate to a system. Digital certificates are granted by a Certificates Authority (CA), which verifies the identity and authenticity of the requester. The CA functions as a trusted third party who can verify that the holder of the certificate is who they claim to be.
Exploits
Exploits are the malicious code or actions an attacker uses to take advantage of a vulnerability on a system. Within each operating system, application, and device, there are known and unknown vulnerabilities. Once a hacker has discovered a vulnerability on his/her target system, the next step is to acquire an exploit that will leverage the security flaw. One popular website for finding exploits is Exploit Database (www.exploit-db.com). This website is maintained by Offensive Security, the creators of the popular penetration testing Linux distro, Kali Linux. The purpose of such a website is to share information with other cybersecurity professionals such as penetration testers who require exploits during their jobs.
Tip
To understand how threats, vulnerabilities, and exploits all fit together, remember the following sentence: a threat uses an exploit to take advantage of a vulnerability on a system.
One such vulnerability is known as EternalBlue (MS17-010); this vulnerability is a weakness found in Microsoft Windows operating systems with Microsoft Server Message Block 1.0 (SMBv1). An attacker with an exploit for EternalBlue will be able to perform remote code execution on a vulnerable machine.
Note
Further information about the MS17-010 security bulletin can be found at https://docs.microsoft.com/en-us/security-updates/securitybulletins/2017/ms17-010
The following are the search results for the EternalBlue (MS17-010) vulnerability on Exploit Database:
Figure 4 – Search results for EternalBlue
Additionally, the attacker or the penetration tester can use an exploitation development framework such as Metasploit to create a custom payload and deliver it to the target. Metasploit allows a cybersecurity professional to build custom payloads that leverage the weaknesses found in applications and operating systems; however, an attacker can do this as well.
Tip
If you want to learn more about Metasploit, please see
https://www.offensive-security.com/metasploitunleashed/
Once an attacker has gained access to a system, he or she is able to escalate their user privileges on the victim's system and even pivot the attack through the compromised system to all other internal devices on the network.
Summary
Systems, networks, and people are liable to present a range of security weaknesses, or vulnerabilities, by which malicious actors may seek to gain access to an organization’s systems and information. Understanding what the different kinds of vulnerability are, along with knowledge of the steps which can be taken to mitigate them, allows the cybersecurity professional to greatly reduce the risk of unwanted access to networked information systems and the disruptive consequences which can flow from that.
To purchase the book on Amazon, click on: https://packt.live/3rxd9Sp







Top comments (0)