In the world of Cloud Computing, we design everything with Security in mind. While you may have heard about AWS Security Groups — have you ever stopped to think about what a security group is, and what it actually does?
What is a Security Group?
A security group acts as a virtual firewall for your instance to control inbound and outbound traffic. For each security group, you add rules that control the inbound traffic to instances, and a separate set of rules that control the outbound traffic.
Security groups are acting as a "firewall" on EC2 instances.
They regulate:
- Access to ports
- Authorized IP ranges (IPv4 and IPv6)
- Controls inbound network (from other to the instance)
- Controls outbound network (from instance to other)
What to know about Security Groups?
- It can be attached to multiple instances within a security group.
- Locked down to a region / VPC combination.
- It lives "outside" the EC2 - if traffic is blocked the EC2 instance won't see it.
- If an application is not accessible (time out), then it's a security group issue.
- If an application gives a connection error, then it's an application error, or the application isn't launched.
- By default, all inbound traffic is blocked and all outbound traffic is authorized.
NB: It is good to maintain one separate security group for SSH access
Security group rules
Inbound: Inbound rules control the incoming traffic to reach the instances that are associated with the security group.
Outbound: Outbound rules control the traffic to leave the instances that are associated with the security group.
NB: For each inbound and outbound rule, you can add, update, or remove rules that take effect immediately in all instances associated with the security group.
Each rule consists of the following key elements:
Name: The name for the security group (for example: webserver-security-group, database-security-group).
Protocol: The network protocols to allow (for example: TCP, UDP, ICMP, etc.).
Port range: A specific port or the range of ports to allow traffic on (for example: 80, 22, 7000-8000, etc.).
Source or destination: The source (inbound rules) or destination (outbound rules) for the traffic that can specify by an IP, IP range, or other security groups.
Ports to know
- 22 = SSH (Secure Shell) - Log into a Linux instance
- 3389 = RDP (Remote Desktop Protocol) - Log into a Windows instance.
- 22 = SFTP (Secure File Transfer Protocol) - Upload files using SSH.
- 21 = FTP (File Transfer Protocol) - Upload files into a file share.
- 80 = HTTP (Hyper Text Transfer Protocol ) - Access unsecured websites.
- 443 = HTTPS (Hyper Text Transfer Protocol Secure) - Access secured websites.
Let's practice on our AWS console
1. Create an EC2 instance and launch it, check if it is running.
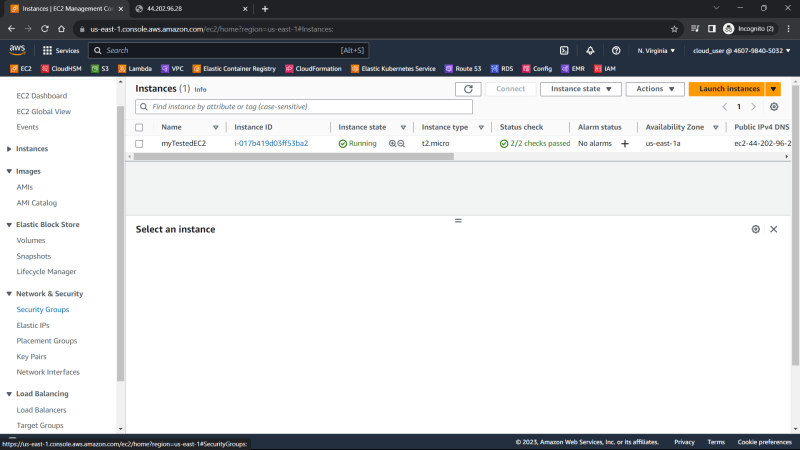
2. Under Network & Security, click Security Groups
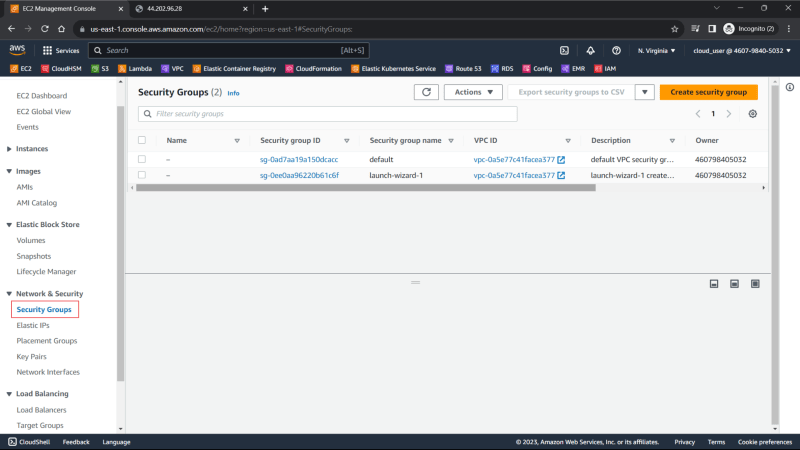
You see two Security Groups, Default Security Group created by default and Launch-wizard-1 Security Group created when the EC2 instances was launched.
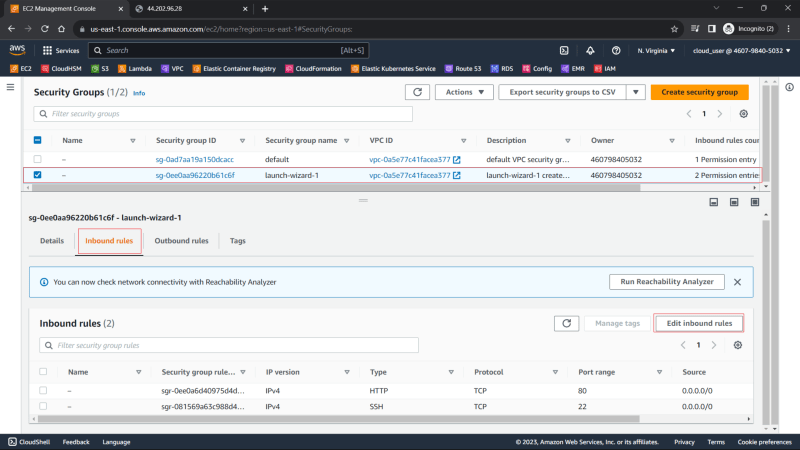
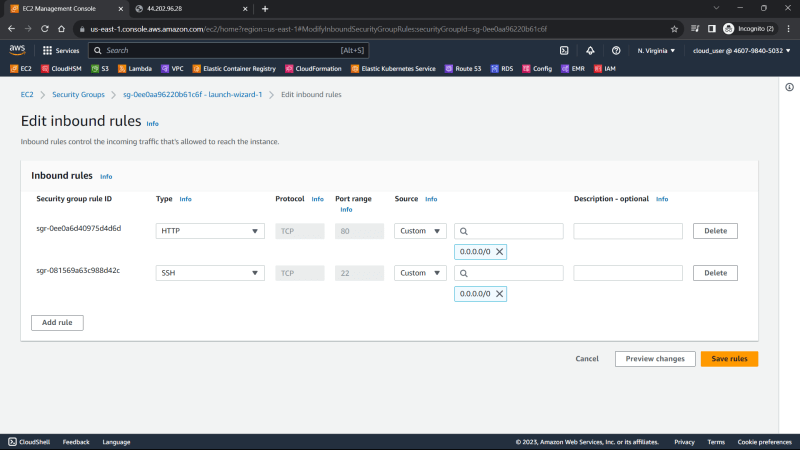
3. Click on the security group to edit the inbound rules
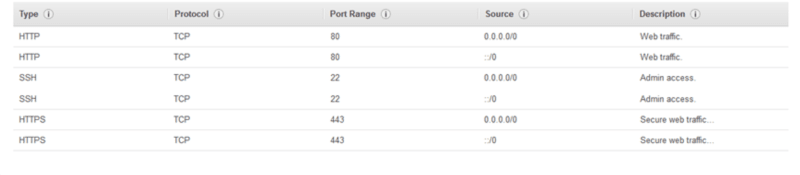
4. Inbound has two rules
HTTP which allows port 80 in the EC2 instances from anywhere
SSH which allows port 22 in the EC2 instances from anywhere
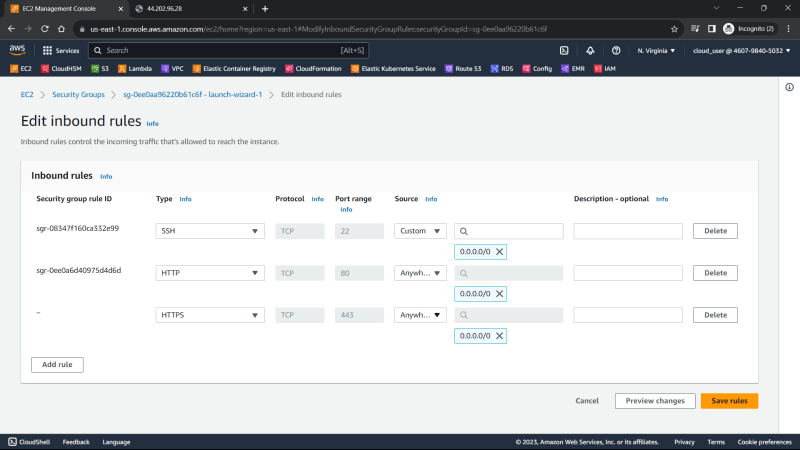
5. Add more rules
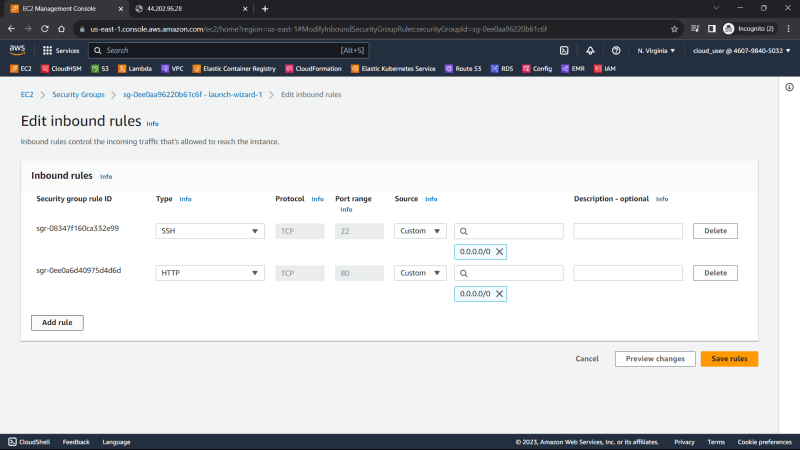
6. Delete the rule
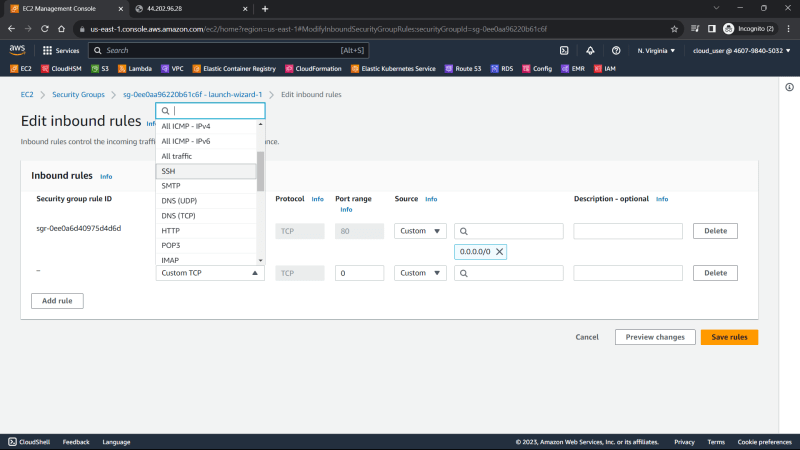
7. Edit the rule
Cloud to the world







Top comments (0)