Copy-paste malware has become a growing concern in today's digital age. This type of malware is designed to infect a computer (running desktop or mobile operating systems) by hiding within copied and pasted text or code. As soon as the copied content is pasted into a new document, the malware infects the system, giving hackers access to sensitive information.
The most concerning aspect of copy-paste malware is its silent operation. They can easily slip under the radar of even the most advanced antivirus software, making them difficult to detect. Once they have infiltrated a system, they can be used to steal sensitive data such as passwords, financial information, and confidential documents. It is crucial to stay vigilant and take the necessary precautions to prevent the spread of these digital saboteurs. For the most part, it may seem like a harmless function, but it can pose a significant risk to your digital security. Cybercriminals often use copy-paste techniques to spread malicious code, steal sensitive information, and gain unauthorized access to systems. By copying and pasting content from untrusted sources, you could inadvertently expose yourself to serious cyber threats.
To protect your data from copy-paste attacks, you should avoid copying and pasting content from untrusted sources. Instead, type URLs directly into your browser and be cautious when downloading files or opening email attachments. Additionally, you can use security software that scans your computer for malware and blocks suspicious activity. By taking these precautions, you can minimize the risk of falling victim to copy-paste attacks and keep your data safe.
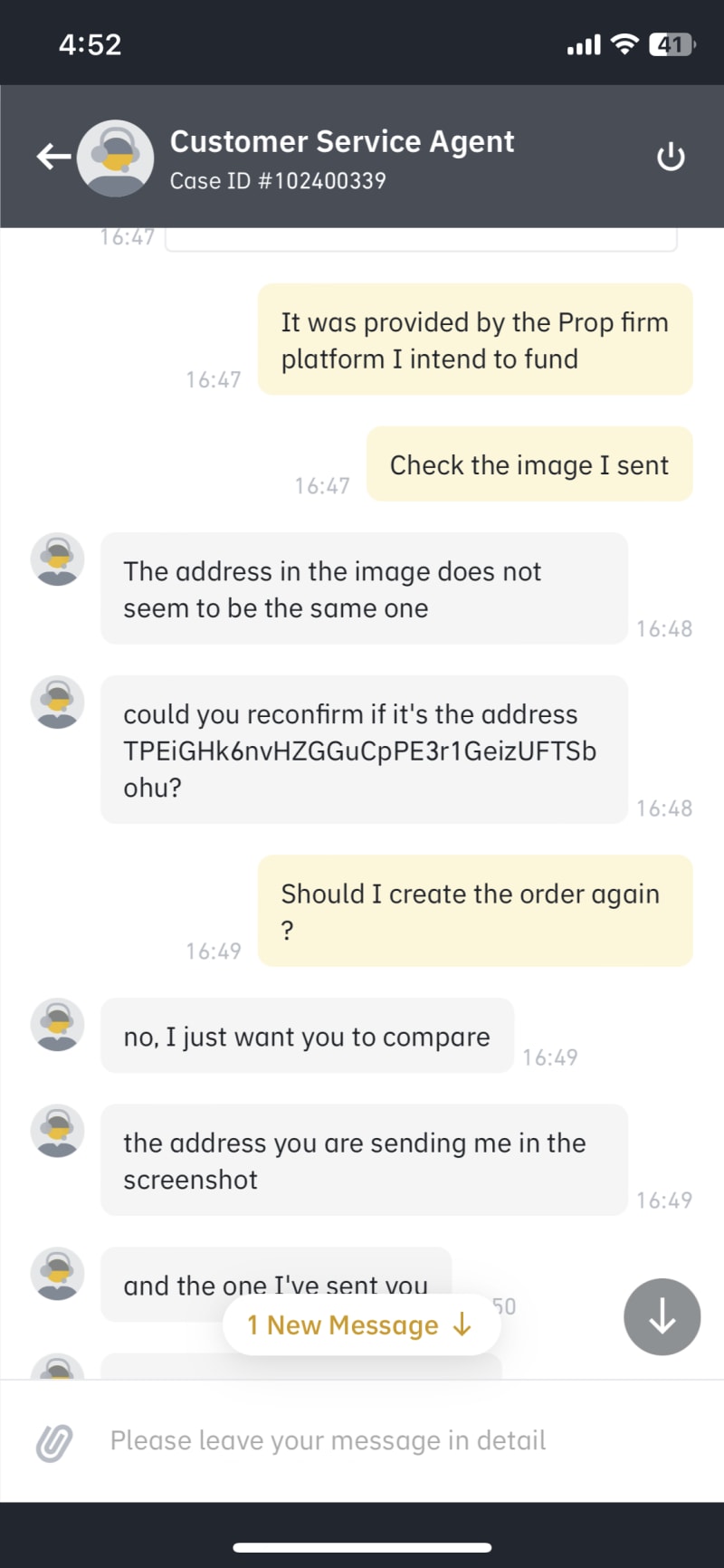
As someone who considers themselves tech-savvy, I never thought I would fall victim to a copy-paste malware attack. But a recent experience with a close friend showed me just how easy it can be for hackers to gain access to sensitive information. It all started when my friend asked for my help in making a payment to a platform they subscribed to. They needed the payment to be made using cryptocurrency, and the options included Bitcoin, Litecoin, and USDT (both ERC20 and TRC20). Fortunately, I had some USDT in my Binance wallet, and I agreed to help. We communicated over WhatsApp, with my friend using WhatsApp Web on their laptop and me using the WhatsApp and Binance mobile apps on my smartphone. They provided the USDT address to send the payment to, and I copied and pasted it into my Binance app.
As I was about to send the funds (after inputting both OTPs sent via SMS and email), I was surprised to see that Binance's system had flagged the address. My withdrawal function was temporarily disabled, and I immediately contacted Binance support to find out what was going on.
To my horror, Binance support informed me that the USDT (TRX) address my friend had sent me was not the correct address. Instead, it was a copy-paste malware attack where the attacker had intercepted my friend's message and changed the USDT (TRX) address to their own. My friend's laptop had been infected with malware, and their personal information was at risk.
Thankfully, It turned out that the said address ‘’ had been reported a couple of times to Binance and their security systems caught the attack. My friend was able to get their laptop cleaned up and secured. However, this experience opened my eyes to just how vulnerable we all are to copy-paste malware attacks. It's a reminder that we should always be vigilant and cautious when copying and pasting information, especially when it comes to sensitive data like cryptocurrency addresses, bank account details, or login credentials. We should also be mindful of the applications and websites we use, ensuring that they are reputable and secure.
In conclusion, my experience with copy-paste malware was a wake-up call for me. This could affect professionals in different fields, a software Engineers, DevOps Engineers could copy-paste malicious codes orchestrated by nefarious players. It reminded me that we live in a digital age where our personal information is constantly at risk of being compromised. We must take steps to protect ourselves, such as using strong passwords, enabling two-factor authentication, and keeping our devices and softwares up-to-date.
**
Simple Steps to Prevent Copy-Paste Malware from Infecting your computer or smartphone:
**
Copy-paste malware can be a challenging threat to detect and prevent. However, there are steps you can take to reduce the risk of infection. Here are five simple steps to prevent copy-paste malware from infecting your system:
- Keep your antivirus software up to date and perform regular system scans.
- Only copy and paste content from trusted sources.
- Double check content copies from trusted and untrusted sources ⚠️ 👀
- Disable the "Automatically download external images and style formats" option in your email settings.
- Use a firewall to block suspicious incoming connections.
- Educate yourself and your employees about the risks of copy-paste malware and how to avoid them.
By following these simple steps, you can significantly reduce the risk of copy-paste malware infecting your system and keep your data safe from cybercriminals.








Top comments (0)